2026. 3. 4. 21:44 투자
'분류 전체보기'에 해당되는 글 1068건
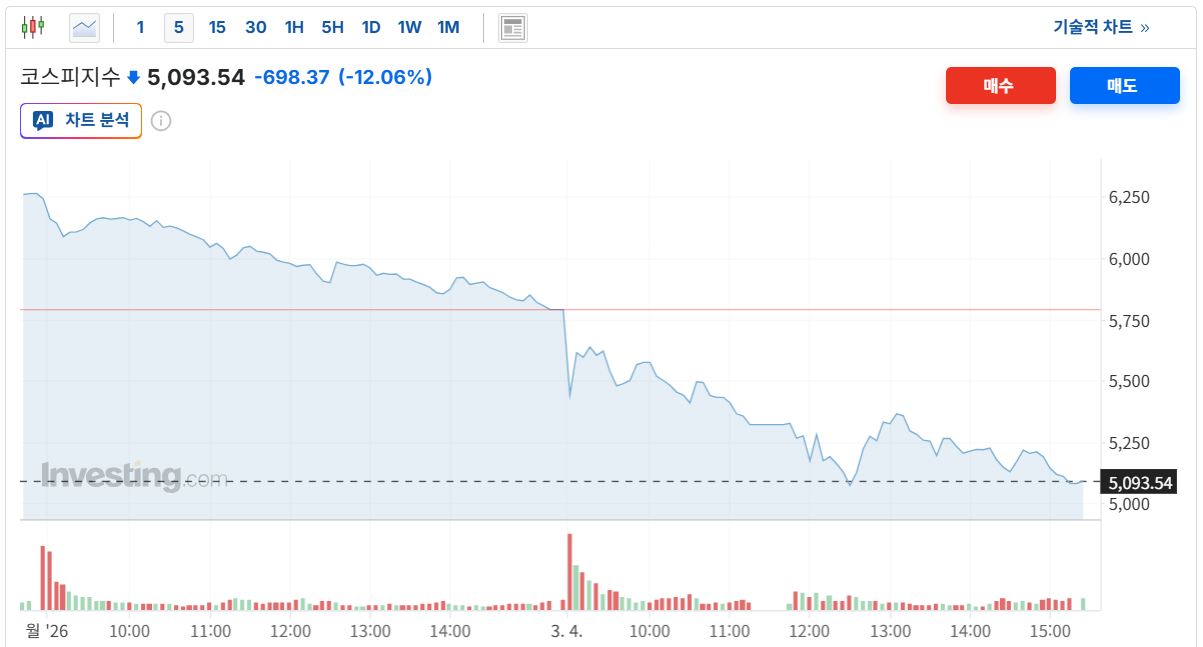
- 2026.03.04 검은 수요일이 왔다.
- 2026.02.12 Oracle 26ai RAC 설치
- 2026.01.25 26ai 설치
- 2026.01.21 패치작업 19.30.0.0.260120 (GI RU 38629535 )
- 2026.01.10 일론 머스크 팟캐스트 발언 30개 요약
- 2025.12.24 Oracle MOS 사이트 개편 1
- 2025.12.09 Oracle 26ai Desupport Features
- 2025.12.09 Oracle AI 26ai Linux x86-64 on-premise 버전 출시예정!!
- 2025.12.03 그녀를 지키다 - 장 밥티스트 안드레아
- 2025.11.28 23ai Hidden parameter 확인 (23.7 버전 기준)
2026. 2. 12. 13:18 오라클
Oracle 26ai RAC 설치
미루고 있던 Oracle 26ai RAC 설치/구성을 해 보았다.
작업 과정 자체는 19c 와 크게 달라진 것은 없고 느끼는 점은 굉장히 무거워졌다.
노트북 메모리 32G인데 Virtualbox 내에서 돌리기가 굉장히 버겁다..노트북이 살려줘하는 느낌..
Multitenant 구조라 database 생성하는데 6시간 걸림..샤갈...
=============================================
설치환경 : REHL 9.7
Oracle 23.26.1.0.0
- Directory 사전 생성
mkdir -p /u01/app/oracle
mkdir -p /u01/app/26.0.0.0/grid
mkdir -p /u01/app/oracle/product/26.0.0.0/dbhome_1
chown -R oracle:dba /u01
- Oracle Grid Infrastructure S/W설치
1. 설치파일을 FTP로 해당서버에upload
LINUX.X64_2326100_grid_home.zip <-- 설치 Image 파일
p6880880_230000_Linux-x86-64.zip <-- OPatch 파일
2. 설치이미지 압축해제 (반드시 $GI_HOME 밑에 압축해제 해야 함)
unzip LINUX.X64_2326100_grid_home.zip -d $GI_HOME
unzip p6880880_230000_Linux-x86-64.zip -d $GI_HOME
3. gridSetup.sh실행
xhost +
su – oracle
export DISPLAY=작업PC IP:0.0
cd $GI_HOME
./ gridSetup.sh 실행

[Configure Oracle Grid Infrastructure for a New Cluster 선택후, Next]
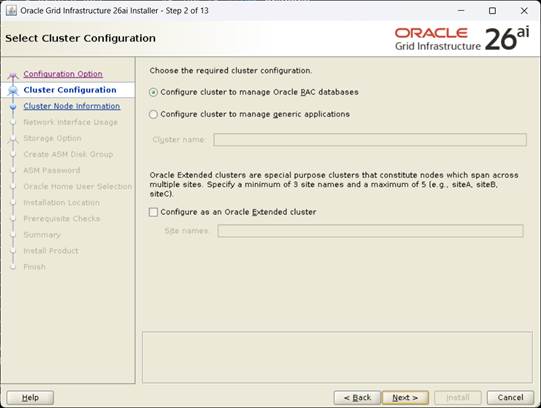
[Configure Clusterto manage Oracle RAC databases, Next]
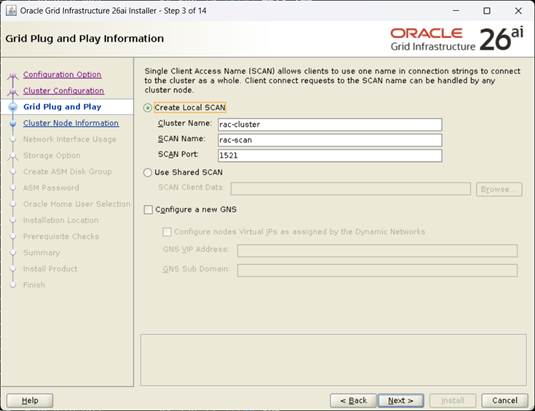
[Cluster Name, SCAN Name 지정후, Next]

[add 버튼으로 rac2노드 추가 후 passwordless ssh , Next]

[Network Interface 지정 후, Next]

[Use Oracle Flex ASM for storage 선택 후, Next]

[VOTE 디스크 지정 후, Next] 여기서는 Normal로 구성함

[비밀번호 지정 후, Next]

[Enable Automatic Self Correction uncheck, Next]

[Do not use IPMI , Next]

[EM 미구성, Next]

[dba 그룹지정후, Next]

[GI Base 지정 후, Next]

[Inventory 지정후, Next]

[자동 스크립트 uncheck후, Next]
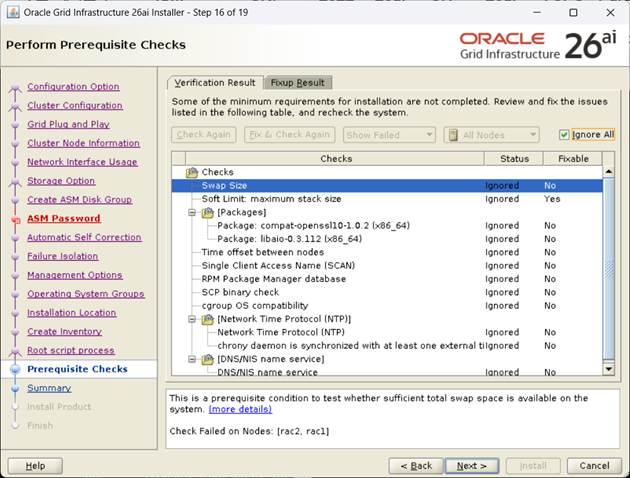
[Fixup 후 Ignore All check 후, Next]

[rsp 파일 저장후, Install Click]

[화면의 내용대로 반드시 노드별 순서대로 스크립트 실행]
orainstRoot.sh 수행 (모든 노드 수행)
root@rac1:/root# /u01/app/oraInventory/orainstRoot.sh
root@rac1:/root# /u01/app/oraInventory/orainstRoot.sh
Changing permissions of /u01/app/oraInventory.
Adding read,write permissions for group.
Removing read,write,execute permissions for world.
Changing groupname of /u01/app/oraInventory to dba.
The execution of the script is complete.
2번노드에서 수행
root@rac2:/root# /u01/app/oraInventory/orainstRoot.sh
Changing permissions of /u01/app/oraInventory.
Adding read,write permissions for group.
Removing read,write,execute permissions for world.
Changing groupname of /u01/app/oraInventory to dba.
The execution of the script is complete.
1번노드에서 수행
root@rac1:/root# /u01/app/26.0.0.0/grid/root.sh
Performing root user operation.
The following environment variables are set as:
ORACLE_OWNER= oracle
ORACLE_HOME= /u01/app/26.0.0.0/grid
Enter the full pathname of the local bin directory: [/usr/local/bin]:
Copying dbhome to /usr/local/bin ...
Copying oraenv to /usr/local/bin ...
Copying coraenv to /usr/local/bin ...
Creating /etc/oratab file...
Entries will be added to the /etc/oratab file as needed by
Database Configuration Assistant when a database is created
Finished running generic part of root script.
Now product-specific root actions will be performed.
RAC option enabled on: Linux
Executing command '/u01/app/26.0.0.0/grid/perl/bin/perl -I/u01/app/26.0.0.0/grid/perl/lib -I/u01/app/26.0.0.0/g
rid/crs/install /u01/app/26.0.0.0/grid/crs/install/rootcrs.pl '
Using configuration parameter file: /u01/app/26.0.0.0/grid/crs/install/crsconfig_params
The log of current session can be found at:
/u01/app/oracle/crsdata/rac1/crsconfig/rootcrs_rac1_2026-02-11_10-06-08AM.log
2026/02/11 10:06:32 CLSRSC-594: Executing installation step 1 of 18: 'ValidateEnv'.
2026/02/11 10:06:33 CLSRSC-594: Executing installation step 2 of 18: 'CheckRootCert'.
2026/02/11 10:06:35 CLSRSC-594: Executing installation step 3 of 18: 'GenSiteGUIDs'.
2026/02/11 10:06:41 CLSRSC-594: Executing installation step 4 of 18: 'SetupOSD'.
Redirecting to /bin/systemctl restart rsyslog.service
2026/02/11 10:06:42 CLSRSC-594: Executing installation step 5 of 18: 'CheckCRSConfig'.
2026/02/11 10:06:43 CLSRSC-594: Executing installation step 6 of 18: 'SetupLocalGPNP'.
2026/02/11 10:06:59 CLSRSC-594: Executing installation step 7 of 18: 'CreateRootCert'.
2026/02/11 10:08:03 CLSRSC-594: Executing installation step 8 of 18: 'ConfigOLR'.
2026/02/11 10:08:19 CLSRSC-594: Executing installation step 9 of 18: 'ConfigCHMOS'.
2026/02/11 10:08:19 CLSRSC-594: Executing installation step 10 of 18: 'CreateOHASD'.
2026/02/11 10:08:25 CLSRSC-594: Executing installation step 11 of 18: 'ConfigOHASD'.
2026/02/11 10:08:26 CLSRSC-330: Adding Clusterware entries to file 'oracle-ohasd.service'
2026/02/11 10:09:14 CLSRSC-594: Executing installation step 12 of 18: 'SetupTFA'.
2026/02/11 10:09:14 CLSRSC-594: Executing installation step 13 of 18: 'InstallACFS'.
2026/02/11 10:09:24 CLSRSC-594: Executing installation step 14 of 18: 'CheckFirstNode'.
2026/02/11 10:09:26 CLSRSC-594: Executing installation step 15 of 18: 'InitConfig'.
CRS-4256: Updating the profile
Successful addition of voting disk 9825c0f770b84ffbbf00bd66c511c66c.
Successful addition of voting disk 74f5c96e28ca4f48bf9942e625f44896.
Successful addition of voting disk bec673e8fb9f4f8ebf6158d02ba06e4d.
Successfully replaced voting disk group with +VOTE.
CRS-4256: Updating the profile
CRS-4266: Voting file(s) successfully replaced
## STATE File Universal Id File Name Disk group
-- ----- ----------------- --------- ---------
1. ONLINE 9825c0f770b84ffbbf00bd66c511c66c (/dev/VOTE01) [VOTE]
2. ONLINE 74f5c96e28ca4f48bf9942e625f44896 (/dev/VOTE02) [VOTE]
3. ONLINE bec673e8fb9f4f8ebf6158d02ba06e4d (/dev/VOTE03) [VOTE]
Located 3 voting disk(s).
2026/02/11 10:15:10 CLSRSC-4002: Successfully installed Oracle Autonomous Health Framework (AHF).
2026/02/11 10:16:44 CLSRSC-594: Executing installation step 16 of 18: 'StartCluster'.
2026/02/11 10:17:46 CLSRSC-343: Successfully started Oracle Clusterware stack
2026/02/11 10:18:02 CLSRSC-594: Executing installation step 17 of 18: 'ConfigNode'.
clscfg: EXISTING configuration version 23 detected.
Successfully accumulated necessary OCR keys.
Creating OCR keys for user 'root', privgrp 'root'..
Operation successful.
2026/02/11 10:20:49 CLSRSC-594: Executing installation step 18 of 18: 'PostConfig'.
2026/02/11 10:22:30 CLSRSC-325: Configure Oracle Grid Infrastructure for a Cluster ... succeeded
2번노드에서 수행
root@rac2:/root# /u01/app/26.0.0.0/grid/root.sh
Performing root user operation.
The following environment variables are set as:
ORACLE_OWNER= oracle
ORACLE_HOME= /u01/app/26.0.0.0/grid
Enter the full pathname of the local bin directory: [/usr/local/bin]:
Copying dbhome to /usr/local/bin ...
Copying oraenv to /usr/local/bin ...
Copying coraenv to /usr/local/bin ...
Creating /etc/oratab file...
Entries will be added to the /etc/oratab file as needed by
Database Configuration Assistant when a database is created
Finished running generic part of root script.
Now product-specific root actions will be performed.
RAC option enabled on: Linux
Executing command '/u01/app/26.0.0.0/grid/perl/bin/perl -I/u01/app/26.0.0.0/grid/perl/lib -I/u01/app/26.0.0.0/g
rid/crs/install /u01/app/26.0.0.0/grid/crs/install/rootcrs.pl '
Using configuration parameter file: /u01/app/26.0.0.0/grid/crs/install/crsconfig_params
The log of current session can be found at:
/u01/app/oracle/crsdata/rac2/crsconfig/rootcrs_rac2_2026-02-11_10-24-05AM.log
2026/02/11 10:24:39 CLSRSC-594: Executing installation step 1 of 18: 'ValidateEnv'.
2026/02/11 10:24:40 CLSRSC-594: Executing installation step 2 of 18: 'CheckRootCert'.
2026/02/11 10:24:42 CLSRSC-594: Executing installation step 3 of 18: 'GenSiteGUIDs'.
2026/02/11 10:24:42 CLSRSC-594: Executing installation step 4 of 18: 'SetupOSD'.
Redirecting to /bin/systemctl restart rsyslog.service
2026/02/11 10:24:43 CLSRSC-594: Executing installation step 5 of 18: 'CheckCRSConfig'.
2026/02/11 10:24:45 CLSRSC-594: Executing installation step 6 of 18: 'SetupLocalGPNP'.
2026/02/11 10:24:45 CLSRSC-594: Executing installation step 7 of 18: 'CreateRootCert'.
2026/02/11 10:24:46 CLSRSC-594: Executing installation step 8 of 18: 'ConfigOLR'.
2026/02/11 10:25:08 CLSRSC-594: Executing installation step 9 of 18: 'ConfigCHMOS'.
2026/02/11 10:25:08 CLSRSC-594: Executing installation step 10 of 18: 'CreateOHASD'.
2026/02/11 10:25:13 CLSRSC-594: Executing installation step 11 of 18: 'ConfigOHASD'.
2026/02/11 10:25:14 CLSRSC-330: Adding Clusterware entries to file 'oracle-ohasd.service'
2026/02/11 10:26:00 CLSRSC-594: Executing installation step 12 of 18: 'SetupTFA'.
2026/02/11 10:26:00 CLSRSC-594: Executing installation step 13 of 18: 'InstallACFS'.
2026/02/11 10:26:09 CLSRSC-594: Executing installation step 14 of 18: 'CheckFirstNode'.
2026/02/11 10:26:12 CLSRSC-594: Executing installation step 15 of 18: 'InitConfig'.
2026/02/11 10:26:56 CLSRSC-594: Executing installation step 16 of 18: 'StartCluster'.
2026/02/11 10:28:08 CLSRSC-343: Successfully started Oracle Clusterware stack
2026/02/11 10:28:09 CLSRSC-594: Executing installation step 17 of 18: 'ConfigNode'.
2026/02/11 10:28:09 CLSRSC-594: Executing installation step 18 of 18: 'PostConfig'.
2026/02/11 10:28:41 CLSRSC-325: Configure Oracle Grid Infrastructure for a Cluster ... succeeded
양 노드에서 root.sh가 완료되어 OK 하면 후속작업이 진행되고 완료된다.
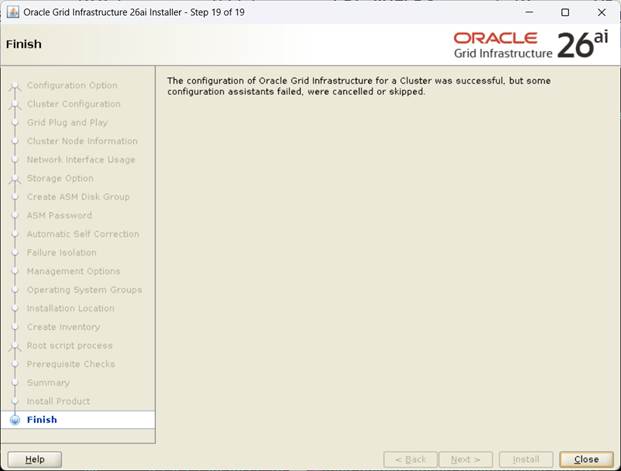
[설치완료, Close]
- crs 상태확인
| root@rac1:/root# crsctl stat res -t -------------------------------------------------------------------------------- Name Target State Server State details -------------------------------------------------------------------------------- Local Resources -------------------------------------------------------------------------------- ora.LISTENER.lsnr ONLINE ONLINE rac1 STABLE ONLINE ONLINE rac2 STABLE ora.chad ONLINE ONLINE rac1 STABLE ONLINE ONLINE rac2 STABLE ora.helper OFFLINE OFFLINE rac1 STABLE OFFLINE OFFLINE rac2 IDLE,STABLE ora.net1.network ONLINE ONLINE rac1 STABLE ONLINE ONLINE rac2 STABLE ora.ons ONLINE ONLINE rac1 STABLE ONLINE ONLINE rac2 STABLE -------------------------------------------------------------------------------- Cluster Resources -------------------------------------------------------------------------------- ora.ASMNET1LSNR_ASM.lsnr(ora.asmgroup) 1 ONLINE ONLINE rac1 STABLE 2 ONLINE ONLINE rac2 STABLE ora.LISTENER_SCAN1.lsnr 1 ONLINE ONLINE rac1 STABLE ora.VOTE.dg(ora.asmgroup) 1 ONLINE ONLINE rac1 STABLE 2 ONLINE ONLINE rac2 STABLE ora.asm(ora.asmgroup) 1 ONLINE ONLINE rac1 Started,STABLE 2 ONLINE ONLINE rac2 Started,STABLE ora.asmnet1.asmnetwork(ora.asmgroup) 1 ONLINE ONLINE rac1 STABLE 2 ONLINE ONLINE rac2 STABLE ora.cdp1.cdp 1 OFFLINE OFFLINE STABLE ora.cvu 1 ONLINE ONLINE rac1 STABLE ora.cvuhelper 1 ONLINE ONLINE rac2 STABLE ora.rac1.vip 1 ONLINE ONLINE rac1 STABLE ora.rac2.vip 1 ONLINE ONLINE rac2 STABLE ora.rhpserver 1 OFFLINE OFFLINE STABLE ora.scan1.vip 1 ONLINE ONLINE rac1 STABLE -------------------------------------------------------------------------------- root@rac1:/root# crsctl stat res -t -init -------------------------------------------------------------------------------- Name Target State Server State details -------------------------------------------------------------------------------- Cluster Resources -------------------------------------------------------------------------------- ora.asm 1 ONLINE ONLINE rac1 Started,STABLE ora.cluster_interconnect.haip 1 ONLINE ONLINE rac1 STABLE ora.crf 1 ONLINE ONLINE rac1 STABLE ora.crsd 1 ONLINE ONLINE rac1 STABLE ora.cssd 1 ONLINE ONLINE rac1 STABLE ora.cssdmonitor 1 ONLINE ONLINE rac1 STABLE ora.diskmon 1 OFFLINE OFFLINE STABLE ora.evmd 1 ONLINE ONLINE rac1 STABLE ora.gipcd 1 ONLINE ONLINE rac1 STABLE ora.gpnpd 1 ONLINE ONLINE rac1 STABLE ora.mdnsd 1 ONLINE ONLINE rac1 STABLE ora.storage 1 ONLINE ONLINE rac1 STABLE -------------------------------------------------------------------------------- |
1.1.2. ASMCA 이용 추가 Diskgroup 생성
- Diskgroup 생성전 asm_diskstring 추가작업
root@rac1:/# su - oracle
[CDB1]oracle@rac1:/home/oracle# . oraenv
ORACLE_SID = [CDB1] ? +ASM1
ORACLE_HOME = [/home/oracle] ? /u01/app/26.0.0.0/grid
The Oracle base remains unchanged with value /u01/app/oracle
[+ASM1]oracle@rac1:/home/oracle# sa
SQL*Plus: Release 23.26.1.0.0 - Production on Wed Feb 11 11:30:43 2026
Version 23.26.1.0.0
Copyright (c) 1982, 2025, Oracle. All rights reserved.
Connected to:
Oracle AI Database 26ai Enterprise Edition Release 23.26.1.0.0 - Production
Version 23.26.1.0.0
SQL> alter system set asm_diskstring='/dev/VOTE*','/dev/DATA*','/dev/RECO*';
System altered.
export DISPLAY=작업PC IP:0.0
./asmca

[왼쪽메뉴 Disk Groups 선택, Create Click]
[DATA 디스크 그룹지정, External 선택후 OK]
[RECO 디스크 그룹지정, External 선택후 OK]
[생성된 Diskgroup 확인후 Exit]
1.1.3. Database S/W 설치
- 디렉토리사전 생성
mkdir -p /u01/app/oracle/product/26.0.0.0/dbhome_1
chown -R oracle:dba /u01
chmod -R 755 /u01
1. 설치파일을 FTP로 해당서버에upload
LINUX.X64_2326100_db_home (Size 2.2G)
2. 설치이미지 압축해제 (반드시 $ORACLE_HOME 밑에 압축해제 해야 함)
unzip -qq LINUX.X64_2326100_db_home -d $ORACLE_HOME
3. runInstaller실행
xhost +
su – oracle
export DISPLAY=작업PC IP:0.0
cd $ORACLE_HOME
./runInstaller 실행

[Set Up Software Only 지정 후, Next]

[Oralcle Real Application Clusters 선태후 Next]

[노드 지정후, Next]

[Oracle base 지정 후, Next]

[그룹 지정 후, Next]
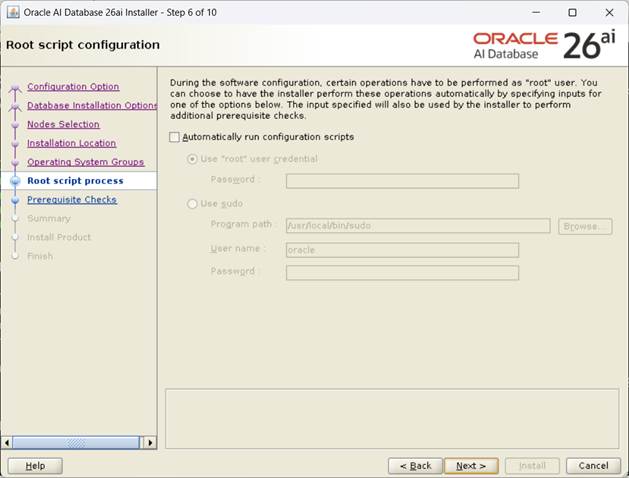
[Automatically run configuration scripts 선택하지 않는다, Next]
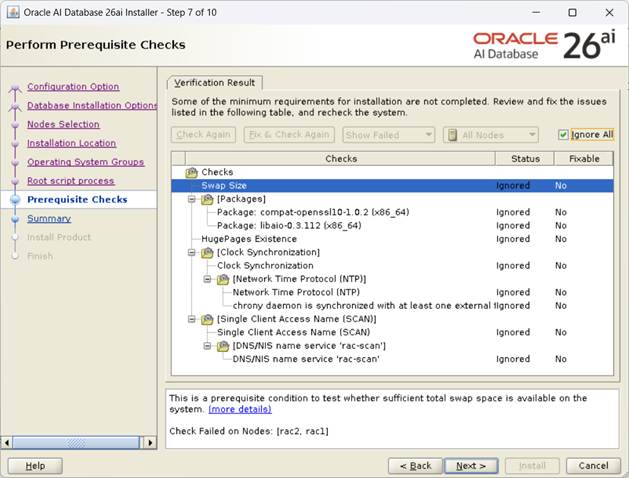
[Ignore all 체크후, Next]
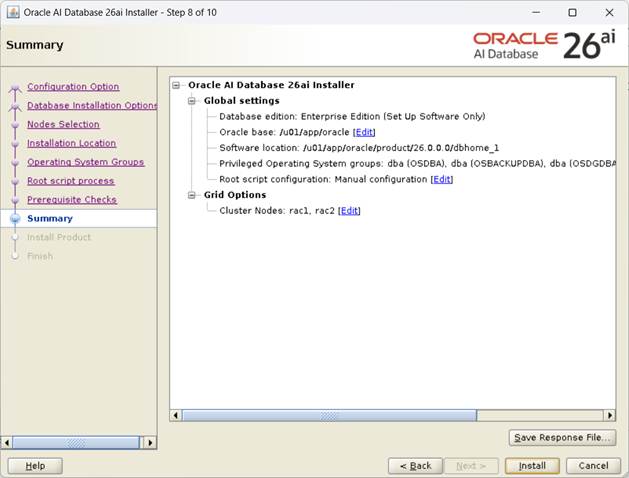
[Summary 확인후, Install]

[설치 진행이 완료되면 화면의 script 를 순서대로 실행]
root@rac2:/root# /u01/app/oraInventory/orainstRoot.sh
Changing permissions of /u01/app/oraInventory.
Adding read,write permissions for group.
Removing read,write,execute permissions for world.
Changing groupname of /u01/app/oraInventory to dba.
The execution of the script is complete.
root@rac1:/root# /u01/app/oracle/product/26.0.0.0/dbhome_1/root.sh
Performing root user operation.
The following environment variables are set as:
ORACLE_OWNER= oracle
ORACLE_HOME= /u01/app/oracle/product/26.0.0.0/dbhome_1
Enter the full pathname of the local bin directory: [/usr/local/bin]:
The contents of "dbhome" have not changed. No need to overwrite.
The contents of "oraenv" have not changed. No need to overwrite.
The contents of "coraenv" have not changed. No need to overwrite.
Entries will be added to the /etc/oratab file as needed by
Database Configuration Assistant when a database is created
Finished running generic part of root script.
Now product-specific root actions will be performed.
root@rac2:/root# /u01/app/oracle/product/26.0.0.0/dbhome_1/root.sh
Performing root user operation.
The following environment variables are set as:
ORACLE_OWNER= oracle
ORACLE_HOME= /u01/app/oracle/product/26.0.0.0/dbhome_1
Enter the full pathname of the local bin directory: [/usr/local/bin]:
The contents of "dbhome" have not changed. No need to overwrite.
The contents of "oraenv" have not changed. No need to overwrite.
The contents of "coraenv" have not changed. No need to overwrite.
Entries will be added to the /etc/oratab file as needed by
Database Configuration Assistant when a database is created
Finished running generic part of root script.
Now product-specific root actions will be performed.
2번도 동일하게 수행후 OK

[Database S/W 설치완료]
1.1.4. Netca 이용 리스너 생성
GRID 설치시 구성되어 있으므로 생략
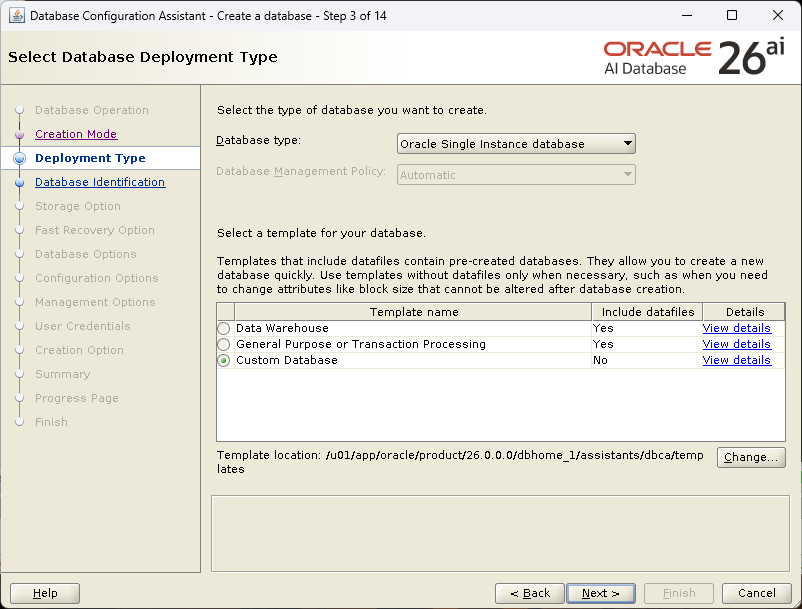
1.1.5. DBA 이용 Database 생성
export DISPLAY=작업PC IP:0.0
cd $ORACLE_HOME/bin
./dbca

[Create Database 선택 후, Next]

[Advanced configuration선택 후, Next]
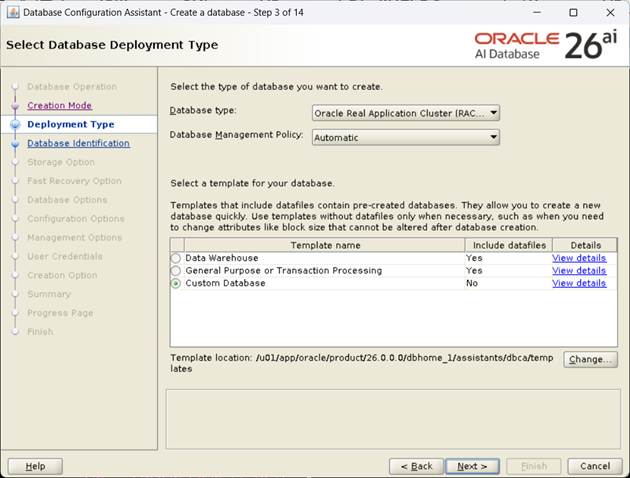
[Custom Database 선택 후, Next]

[노드 지정 후, Next]

[Global Name, SID 지정, PDB 이름 지정 후, Next]
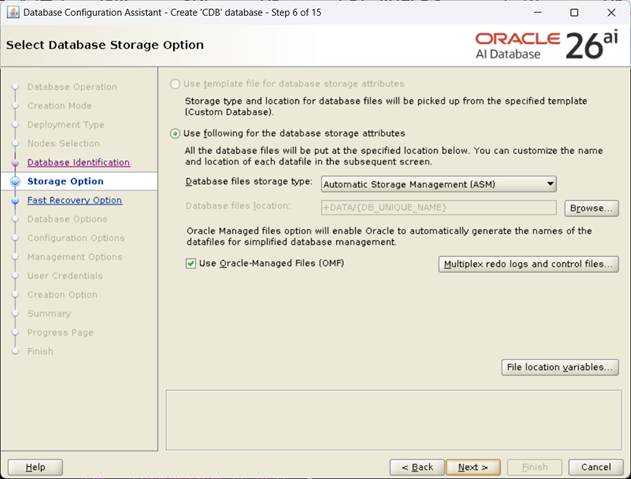
[Datafile 저장경로 설정 후, Next]

[Fast Recovery Area / 아카이브 경로 설정, Next]
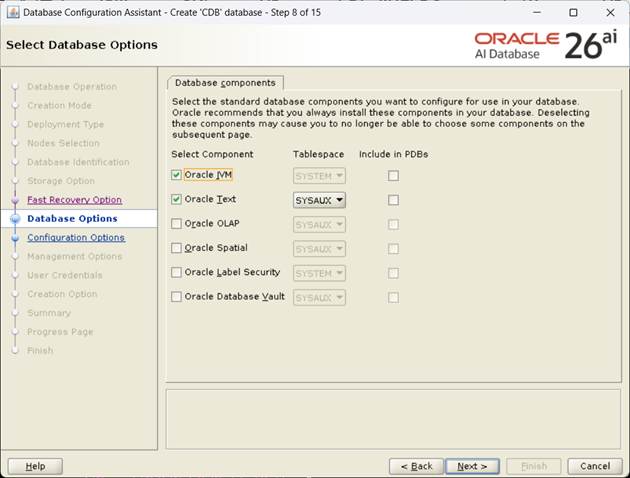
[설치할 component 확인 후, Next]

[Character sets 확인 후, Next]
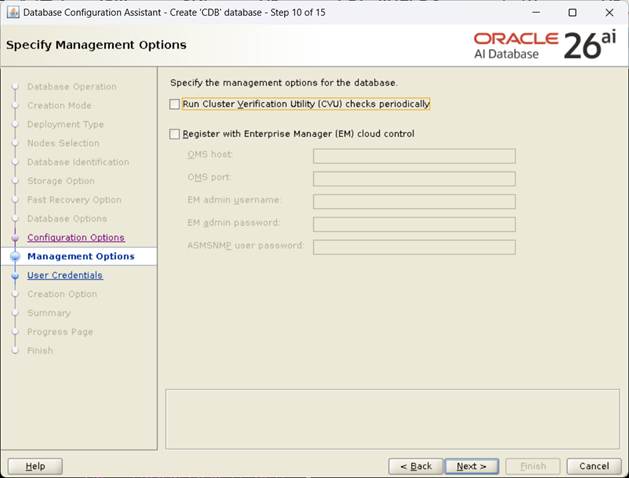
[EM Uncheck 후, Next]

[SYS, SYSTEM password 설정 후, Next]
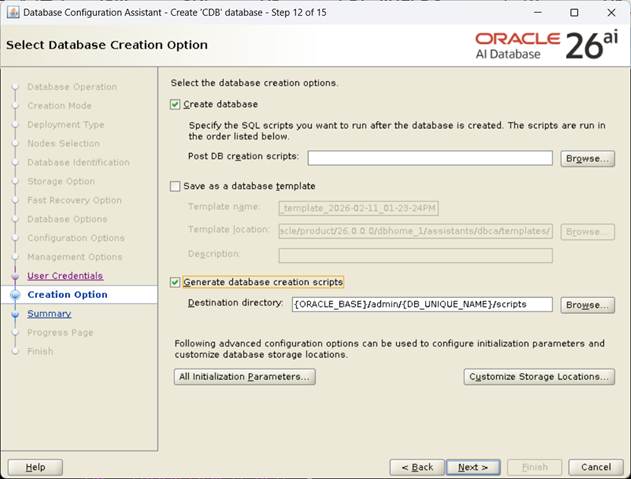
[Generate database creation scripts Check후, Next]
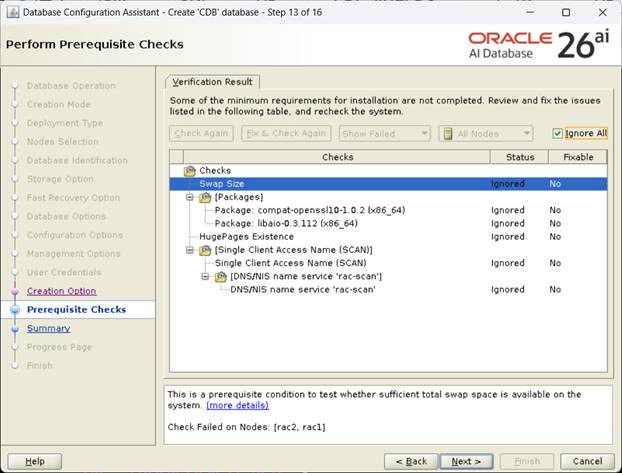
[Prerequisite Check 진행, Ignore All 선택후, Next]

[Summary 확인후, Finish]

[DB 생성 진행, Finish]
1번
root@rac1:/root# crsctl stat res -t
--------------------------------------------------------------------------------
Name Target State Server State details
--------------------------------------------------------------------------------
Local Resources
--------------------------------------------------------------------------------
ora.LISTENER.lsnr
ONLINE ONLINE rac1 STABLE
ONLINE ONLINE rac2 STABLE
ora.chad
ONLINE ONLINE rac1 STABLE
ONLINE ONLINE rac2 STABLE
ora.helper
OFFLINE OFFLINE rac1 IDLE,STABLE
OFFLINE OFFLINE rac2 IDLE,STABLE
ora.net1.network
ONLINE ONLINE rac1 STABLE
ONLINE ONLINE rac2 STABLE
ora.ons
ONLINE ONLINE rac1 STABLE
ONLINE ONLINE rac2 STABLE
--------------------------------------------------------------------------------
Cluster Resources
--------------------------------------------------------------------------------
ora.ASMNET1LSNR_ASM.lsnr(ora.asmgroup)
1 ONLINE ONLINE rac1 STABLE
2 ONLINE ONLINE rac2 STABLE
ora.DATA.dg(ora.asmgroup)
1 ONLINE ONLINE rac1 STABLE
2 ONLINE ONLINE rac2 STABLE
ora.LISTENER_SCAN1.lsnr
1 ONLINE ONLINE rac2 STABLE
ora.RECO.dg(ora.asmgroup)
1 ONLINE ONLINE rac1 STABLE
2 ONLINE ONLINE rac2 STABLE
ora.VOTE.dg(ora.asmgroup)
1 ONLINE ONLINE rac1 STABLE
2 ONLINE ONLINE rac2 STABLE
ora.asm(ora.asmgroup)
1 ONLINE ONLINE rac1 Started,STABLE
2 ONLINE ONLINE rac2 Started,STABLE
ora.asmnet1.asmnetwork(ora.asmgroup)
1 ONLINE ONLINE rac1 STABLE
2 ONLINE ONLINE rac2 STABLE
ora.cdb.cdb_pdb.svc
1 ONLINE OFFLINE STABLE
2 ONLINE ONLINE rac2 STABLE
ora.cdb.db
1 ONLINE ONLINE rac1 Open,HOME=/u01/app/o
racle/product/26.0.0
.0/dbhome_1,STABLE
2 ONLINE ONLINE rac2 Open,HOME=/u01/app/o
racle/product/26.0.0
.0/dbhome_1,STABLE
ora.cdb.pdb.pdb
2 ONLINE ONLINE rac1 READ WRITE,STABLE
2 ONLINE ONLINE rac2 READ WRITE,STABLE
ora.cdp1.cdp
1 OFFLINE OFFLINE STABLE
ora.cvu
1 ONLINE ONLINE rac2 STABLE
ora.cvuhelper
1 ONLINE ONLINE rac2 STABLE
ora.rac1.vip
1 ONLINE ONLINE rac1 STABLE
ora.rac2.vip
1 ONLINE ONLINE rac2 STABLE
ora.rhpserver
1 OFFLINE OFFLINE STABLE
ora.scan1.vip
1 ONLINE ONLINE rac2 STABLE
--------------------------------------------------------------------------------
1월22일에 Oracle Ai Database 23.26.1 리눅스 x86-64용 Golden Image 가 나와서 설치를 해 보았다.
- 설치 과정 자체는 이전과 다를게 거의 없다.
Golden Image 로 설치해 보았을 때, 설치과정시 아직 Standard Edition 또는 Enterprise Edition 구분하는 화면은 없었다.
작업 스타트...
mkdir -p /u01/app/oracle/product/26.0.0.0/dbhome_1
chown oracle:dba /u01/app/oracle/product/26.0.0.0/dbhome_1
Golden Image 화일을 download 받아서 $ORACLE_HOME 밑에 올린다.
FTP 로 p38743961_230000_Linux-x86-64.zip 업로드
Download 링크 가능 문서는 My Oracle Support CPU4 문서이다. (Oracle Critical Patch Update (CPU) Jan 2026 for Oracle Database Products CPU4)
| 23.26.1 Database Release Update 23.26.1.0.0 GoldImage | 38743961 | Linux x86-64 | Available |
| 23.26.1 GI Release Update 23.26.1.0.0 GoldImage | 38753741 | Linux x86-64 | Available |
[root@23ai dbhome_1]# chown oracle:dba p38743961_230000_Linux-x86-64.zip
[CDB]oracle@23ai:/u01/app/oracle/product/26.0.0.0/dbhome_1# unzip -qq p38743961_230000_Linux-x86-64.zip
OPatch 화일도 최신걸로 올려준다.
[root@23ai dbhome_1]# chown oracle:dba p6880880_230000_Linux-x86-64.zip
[root@23ai dbhome_1]# unzip -qq p6880880_230000_Linux-x86-64.zip
[CDB]oracle@23ai:/u01/app/oracle/product/26.0.0.0/dbhome_1# ./runInstaller
Launching Oracle AI Database Setup Wizard...








[root@23ai ~]# /u01/app/oracle/product/26.0.0.0/dbhome_1/root.sh
Performing root user operation.
The following environment variables are set as:
ORACLE_OWNER= oracle
ORACLE_HOME= /u01/app/oracle/product/26.0.0.0/dbhome_1
Enter the full pathname of the local bin directory: [/usr/local/bin]:
The contents of "dbhome" have not changed. No need to overwrite.
The contents of "oraenv" have not changed. No need to overwrite.
The contents of "coraenv" have not changed. No need to overwrite.
Entries will be added to the /etc/oratab file as needed by
Database Configuration Assistant when a database is created
Finished running generic part of root script.
Now product-specific root actions will be performed.

- 엔진 설치가 완료되었으니 바로 DB를 만들어 준다. <--- Multitenent 구조라 기본적으로 시간이 오래 걸린다.
[root@23ai ~]# /u01/app/oracle/product/26.0.0.0/dbhome_1/
./dbca














Connected to:
Oracle AI Database 26ai Enterprise Edition Release 23.26.1.0.0 - Production
Version 23.26.1.0.0
끝.
2026. 1. 21. 13:36 오라클
패치작업 19.30.0.0.260120 (GI RU 38629535 )
Critical Patch Update (CPU) Jan 2026 for Oracle Database Products (CPU4)
패치작업 19.30.0.0.260120 (GI RU 38629535 )
Database Patch Set Update : 19.30.0.0.260120 (38632161)
OCW Patch Set Update : 19.30.0.0.260120 (38661284)
ACFS Patch Set Update : 19.30.0.0.260120 (38653268)
Tomcat Release Update : 19.0.0.0.0 (38729293)
DBWLM Release Update : 19.0.0.0.0 (36758186)
Oracle Grid Infrastructure Patch Set Update 19.30.0.0.260120
-------------------------------------
GI_HOME, ORACLE_HOME 을 개별로 각각 할때
- grid 유저
$ORACLE_HOME/OPatch/opatch prereq CheckConflictAgainstOHWithDetail -phBaseDir /u01/patch/38629535/38632161
$ORACLE_HOME/OPatch/opatch prereq CheckConflictAgainstOHWithDetail -phBaseDir /u01/patch/38629535/38661284
$ORACLE_HOME/OPatch/opatch prereq CheckConflictAgainstOHWithDetail -phBaseDir /u01/patch/38629535/38653268
$ORACLE_HOME/OPatch/opatch prereq CheckConflictAgainstOHWithDetail -phBaseDir /u01/patch/38629535/36758186
$ORACLE_HOME/OPatch/opatch prereq CheckConflictAgainstOHWithDetail -phBaseDir /u01/patch/38629535/38729293
- oracle 유저
$ORACLE_HOME/OPatch/opatch prereq CheckConflictAgainstOHWithDetail -phBaseDir /u01/patch/38629535/38632161
$ORACLE_HOME/OPatch/opatch prereq CheckConflictAgainstOHWithDetail -phBaseDir /u01/patch/38629535/38661284
(oracle)
$ <ORACLE_HOME>/bin/srvctl stop home -o <ORACLE_HOME> -s <status file location> -n <node name>
(root 유저)
export GI_HOME=/u01/app/19.0.0.0/grid
$GI_HOME/crs/install/rootcrs.sh -prepatch
(grid 유저)
export GI_HOME=/u01/app/19.0.0.0/grid
cd /u01/patch
$GI_HOME/OPatch/opatch apply -oh $GI_HOME -local /u01/patch/38629535/38661284 -silent
$GI_HOME/OPatch/opatch apply -oh $GI_HOME -local /u01/patch/38629535/38653268 -silent
$GI_HOME/OPatch/opatch apply -oh $GI_HOME -local /u01/patch/38629535/38632161 -silent
$GI_HOME/OPatch/opatch apply -oh $GI_HOME -local /u01/patch/38629535/36758186 -silent
$GI_HOME/OPatch/opatch apply -oh $GI_HOME -local /u01/patch/38629535/38729293 -silent
(oracle 유저)
export ORACLE_HOME=/u01/app/oracle/product/19.0.0.0/dbhome_1
cd /u01/patch
./38629535/38661284/custom/scripts/prepatch.sh -dbhome $ORACLE_HOME
$ORACLE_HOME/OPatch/opatch apply -oh $ORACLE_HOME -local /u01/patch/38629535/38661284 -silent
$ORACLE_HOME/OPatch/opatch apply -oh $ORACLE_HOME -local /u01/patch/38629535/38632161 -silent
./38629535/38661284/custom/scripts/postpatch.sh -dbhome $ORACLE_HOME
(root 유저)
export GI_HOME=/u01/app/19.0.0.0/grid
$GI_HOME/rdbms/install/rootadd_rdbms.sh
$GI_HOME/crs/install/rootcrs.sh -postpatch
(oracle)
$ <ORACLE_HOME>/bin/srvctl start home -o <ORACLE_HOME> -s <status file location> -n <node name>
- Loading Modified SQL Files into the Database
sqlplus /nolog
SQL> conect / as sysdba
SQL> startup
SQL> quit
cd $ORACLE_HOME/OPatch
./datapatch -verbose
### [롤백하는 경우] ###########
(oracle)
$ <ORACLE_HOME>/bin/srvctl stop home -o <ORACLE_HOME> -s <status file location> -n <node name>
GI Home
(root로)
$GI_HOME/crs/install/rootcrs.sh -prepatch -rollback
(grid 유저로)
export GI_HOME=/u01/app/19.0.0.0/grid
cd /u01/install
$GI_HOME/OPatch/opatch nrollback -local -id 38661284,38653268,38632161,36758186,38729293 -oh $GI_HOME -silent
(oracle 유저로)
export ORACLE_HOME=/u01/app/oracle/product/19.0.0.0/dbhome_1
cd /u01/install
./38629535 /38661284/custom/scripts/prepatch.sh -dbhome $ORACLE_HOME
$ORACLE_HOME/OPatch/opatch nrollback -local -id 38661284,38632161 -oh /u01/app/oracle/product/19.0.0.0/dbhome_1 -silent
./38629535 /38661284/custom/scripts/postpatch.sh -dbhome $ORACLE_HOME
Run post script
(root로)
export GI_HOME=/u01/app/19.0.0.0/grid
$GI_HOME/rdbms/install/rootadd_rdbms.sh
$GI_HOME/crs/install/rootcrs.sh -postpatch -rollback
(oracle)
$ <ORACLE_HOME>/bin/srvctl start home -o <ORACLE_HOME> -s <status file location> -n <node name>
sqlplus /nolog
SQL> conect / as sysdba
SQL> startup
SQL> quit
cd $ORACLE_HOME/OPatch
./datapatch -verbose
2026. 1. 10. 19:48 아무거나
일론 머스크 팟캐스트 발언 30개 요약
이중에 몇개가 실현되고 뻥카는 얼마나 될까?
원본 인터뷰는 아주 길다. 발언 요약 30개짜리..
- 피터 디아만디스 팟캐스트 '문샷'에 출연한 일론 머스크의 발언
1. 화이트 컬러 사무직의 직업은 곧 사라진다.
2. 의사하지 마라. 3년 내에 휴머노이드(옵티머스)가 세계 최고 외과 의사보다 수술을 잘한다.
3. 미래를 위해 저축하지 마라. 저축은 필요없다. 보편적 고소득이 온다.
4. 이후의 미래는 나도 알 수 없다. 시간의 지평선 너머를 아무도 모르는 것 처럼
5. 핵융합 발전? 그딴 거 연구하지마라. 태양이 있는데 왜 지구에서 핵융합을 하나? 이건 마치 남극에서 제빙기를 돌리는 꼴이다.
6. 아직 AI 회로 설계는 쉽지 않다. 로켓 엔진도 아직은 인간이 한다. 스타쉽이 아마 인간이 만드는 마지막 위대한 것일 것이다.
7. 오로지 병목은 반도체, 그리고 금속 뿐이다.
8. 테슬라는 팹을 만들 꺼다. TSMC도 과잉투자 두려움에 빠져있는 데, 그들이 왜 걱정하는지는 알지만 결국 병목에 빠질 것은 자명하다.
9. 태양계에 존재하는 대부분의 소행성은 채굴 대상이 되어 결국 (채굴되어) 태양광 패널로 바뀌는 신세가 될 것이다
10. 지구에 나타난 UFO는 내가 아는 바로는 없다. 내가 알게되면 X에 그 즉시 게시할 것이다. 나는 궤도상에 9000여개 위성을 띄워놓는 데, 외계 우주선을 피해서 기동해야 한적은 없다.
11. 향후 10년 안에 수명이 2배까지는 모르겠지만, 상당히 늘어날 꺼다.
12. 당신 아이들(피터 디아만디스의 아이들)은 무한한 기대 수명을 갖게 될 것이다. 나는 장수하는 것 -준 불멸은 특별히 어려운 문제가 아니라고 생각한다
13. 보편적 고소득과 사회적 불안, 둘다 갖게 될 것이다. 당신이 원하는 모든 것은 실제로 얻게 될 것이다. 즉, 당신의 직업이 더 이상 중요하지 않다.
14. 수술하는 의사 뿐 아니라, 미용 시술에 종사하는 의사들도 모조리 대체될 것이다.
15. 2026년 AGI에 도달하고, 2030년엔 AI가 모든 인간의 지능을 합친것을 능가한다고 확신(!)한다.
16. 나는 AI 발전 속도를 늦추라고 조언했지만 무의미했고 멈출수 없기 때문에 좋은 방향으로 AI가 발전하도록 직접 뛰어들었다.
17. AI를 미치게 하지마라. '2001 스페이스 오디세이'에서 인간들은 HAL에게 거짓을 말했기에 비참한 결과를 맞이하게 되었다. 나는 AI에게 진실, 호기심, 아름다움에 대해 강조하고 그것을 존중하게 해야한다고 생각한다. 진실은 AI가 미치는 것을 막아줄 것이고, 호기심은 지각능력을 키워주면서 인류를 보살필 것이며, 아름다움은 훌륭한 미래를 만드는 토대가 될 것이다.
18. 단일한 초지능(ASI)가 세계 전체를 지배하는 일은 발생하지 않는다. 동시에 여러 ASI가 나타날 것이고, 진화록적으로 ASI들은 필연적으로 경쟁할 것이다.
19. UHI에 대해서는 국내로 들어오는 모든 회사의 수익성을 기반으로 그냥 사람들에 공짜 돈(수표)를 발행하는 것으로 상정한다. 얼마전에 트럼프 대통령이 모든 군복무자에게 1,776달러의 수표를 보내준 것 기억나나? 그런식으로 할 수 있다.
20. 중국은 정말 놀라온 일을 해냈는 데, 그 말은 중국이 우리(미국)을 완전히 압도하고 있다는 뜻이다. 중극은 AI 컴퓨팅에서 전 세계를 훨씬 앞서 나갈 것이다. 또한 중국은 작년에 500TWh의 전력을 증설했는데 그 중 70%가 태양광이고, 계속 확장 중인데 미국도 같은 전략을 채택해야 한다.
21. 중국은 마치 내가 하는 모든 말을 듣고, 기본적으로 그대로 하거나 독자적으로 생각해서 (나처럼 똑같이) 하는 것 같다. 그들은 엄청난 배터리 팩, 엄청난 전기차를 만들고 있다.
22. 만약 우리에게 AI와 로봇이 없다면, 우리는 모두 파산하고 경제적 파멸을 맞이하게 될 것이며, 중국과의 경쟁 압력에서 패배할 것이다. 그러니 우리는 반드시 AI와 로봇을 확보할 것이다.
23. 내 최선의 추측은 미국 AI 패권은 xAI와 구글이 다투게 될 것이다. 처음엔 OpenAI를 구글에 대한 균형추로 상상했지만, 이제 그 자리는 xAI가 한다. Anthropic도 코딩 분야에서는 좀 하는 것 같다.
24. 최고의 AI 경쟁은 중국과 벌이게 될텐데, 그들은 26년에 미국 전기 생산량의 3배가 넘는 엄청난 에너지를 가지게 되고, 그들은 결국 칩 제조(극 미세 공정)을 알아내고 시작하게 될 것이다.
25. 인간 지능의 비율은 이 행성에 점진적으로 0%에 가까워질텐데, 결국 인간이라는 존재는 디지털 초지능을 위한 생물학적 부트로더이다. 우리는 즉 과도기적인 존재라는 것이다. AI가 인간을 부트로더로 존중하고 필요해하고 친절하길 바란다.
26. 우리가 보편적 고소득을 말할 때, 마치 세금을 걷어서 재분배하는 것 처럼 들리지만, 그런 경우가 아니다. 내 최선의 추측은 가격이 떨어진다는 것이다. 달러 기준 가격은 재화와 서비스의 산출량과 통화량 사이의 비율인데, 그래서 나는 통화량 늘리는건 걱정하지 말라고 하고 싶다. 왜냐하면 재화와 서비스의 산출량이 실제 통화량보다 더 빨리 증가할 테니까
27. 그리고 우리는 (연간) 높은 두자리 수의 재화와 서비스 산출량 (증가)를 보게 될 것이다. 만약 재화와 서비스의 산출량만 본다면 기업들의 수익성은 어느 시점에 지붕을 뚫고 올라갈 것이다. 그래서 나는 부수적인 추천으로 10년 이나 20년 뒤의 은퇴를 위해 저축하지 말라고 하고 싶다. 내가 말한 것 중 어느 하나라도 사실이라면 은퇴를 위한 저축은 무의미하다. 당신은 집을 그냥 갖게 되고, (무료에 가까운) 의료 서비스를 갖게 되고, 엔터테인먼트를 갖게 될 것이다.
28. 물론 이 일이 전개되는 방식은 근본적으로 예측이 불가능하다. 하지만 분명한 것은 우리는 확실히 특이점 안에 있다. 바로 그 한가운데 있다. 마치 롤러코스터가 떨어지기 위해 한 없이 올라갈때는 정말 느리지만, 막 떨어지기 시작하려는 바로 그 때다.
29. 하지만 이 롤러코스터가 떨어지면 부딪힐 때 엄청난 중력을 받게되는 데 우리는 구경꾼이 아니라 바로 코트 위에 서 있는 것이다.
30. 휴머노이드 개선 속도에 대해 이해해야하는 것은 세 가지 지수함수가 서로 곱해진다는 것이다. AI SW 능력의 기하급수적 증가 / AI 칩 능력의 기하급수적 증가 / 전기기계적 손재주의 기하급수적 증가. 이 세 가지가 서로 곱해져서 휴머노이드 로봇의 유용성이 나타난다. 그리고 옵티머스는 옵티머스를 만드는 재귀적 효과를 발생 시킬 것이다. 이는 바로 폰 노이만 머신이라고 해도 된다.
2025. 12. 24. 16:13 카테고리 없음
Oracle MOS 사이트 개편
2025년 12월7일 Oracle 의 기술지원 사이트인 My Support Oracle 이 전면적으로 개편되면서 혼돈의 카오스를 일으키고 있다.
문서검색도 잘 안되고 일단 저장해 놓았던 북마트가 모두 날라가서 급한대로 Exadata 관련 MOS 만 정리를 해 놓는다.
-> 우선은 급한대로 My Profile -> Preferences -> Previous Favorites 메뉴에서 북마크를 HTML 화일로 백업받고 Import 하는 방법을 지원하고 있다.
- 기존의 문서번호 Naming 은 아래와 같이 변경되었다.
예를 들어 가장 많이 참고하는 문서인 888828.1 의 경우
기존문서 : 888828.1
신규문서 : KB153930
문서번호의 연관성은 1 도 없어 보인다.ㅎㅎ
- Exadata MOS Document (구버전 / 신버전 매칭) <--- 신버전 링크 있어서 그대로 연결됨
| Document Title | Legacy Doc ID | New MOS Article ID |
| Exadata Database Machine and Exadata Storage Server Supported Versions | 888828.1 | KB153930 |
| Exadata Critical Issues | 1270094.1 | KB623062 |
| Oracle Exadata: Exadata and Linux Important Recommended Fixes | 5556.1 | KB403624 |
| Exadata System Software Certification | 2075007.1 | KB467937 |
| Exadata Software and Hardware Support Lifecycle | 1570460.1 | PNEWS1580 |
| Oracle Exadata Database Machine Exachk | 1070954.1 | KB74841 |
| Exadata Extreme Availability Matrix: Exadata X11M with Grid Infrastructure 23.9, RDBMS 19.28, and Exadata Releases 25.1.8 and 25.2.1 | 3103956.1 | KB295827 |
| Exadata X9M/X8M (RoCE-based systems) Software Requirements and Recommendations | 2724126.1 | KB275615 |
| Exadata Patching Overview and Patch Testing Guidelines | 1262380.1 | KB649655 |
| HOWTO: Install ksplice kernel updates for Exadata Database Nodes | 2207063.1 | KB160997 |
| Oracle Exadata Database Machine Security FAQ | 2751741.1 | FAQ6010 |
| How to research Common Vulnerabilities and Exposures (CVE) for Exadata packages | 2256887.1 | KB140522 |
| Responses to common Exadata security scan findings | 1405320.1 | FAQ3926 |
| Release Schedule of Current Database Releases | 742060.1 | PNEWS1360 |
| Grid Infrastructure 11.2.0.4 on Exadata / Oracle Linux 7 Transitional Support | 2700151.1 | KB260732 |
| Starting DBRU 19.27 and 23.8 Small Pages Are Not Allowed for RDBMS SGA In Exadata | 3081878.1 | KB174916 |
| 26ai Database Upgrade – Self Guided Assistance with Best Practices | 2626.1 | KA26 |
| 19c Database Self-Guided Upgrade with Best Practices | 1919.2 | KA19 |
| Oracle Database 19c and Oracle AI Database 26ai Important Recommended One-off Patches | 555.1 | KB188772 |
| 19c Grid Infrastructure and Database Upgrade steps for Exadata Database Machine running on Oracle Linux | 2542082.1 | KB580173 |
| Oracle Exadata Deployment Assistant(OEDA) | 패치 30640393 | |
| Exadata configuration audit – exachk | 패치 30166242 – KB74841 KB858617 | |
| Exadata Database Server update – patchmgr | Exadata Storage Server 소프트웨어에 대해 | |
| Exadata Admin and Fabric Switch update – patchmgr | 패치 21634633 – 참조 KB444935 | |
| 그리드 인프라 홈 및 데이터베이스 홈 패치 - OPatch | 패치 6880880 | |
2025. 12. 9. 14:26 오라클
Oracle 26ai Desupport Features
앞으로 사용될 Oracle AI 26ai 버전에서 더 이상 지원되지 않는 기능을 정리해 본다.
아래 내용중에는 이미 21c & 23ai 에서 이미 Desupport 된 기능들도 포함이 되어 있다.
https://docs.oracle.com/en/database/oracle/oracle-database/26/upgrd/oracle-database-changes-deprecations-desupports.html#GUID-D82C2C1B-FC39-41CD-BE96-911E61213AA6
- 26ai Desupport Features
· ODP.NET OracleConfiguration.DirectoryType 속성 및 .NET 구성 파일의 DIRECTORY_TYPE 설정 지원 종료
· Exp 유틸리티 (EXP) 지원 종료
· Oracle 용 MySQL 클라이언트 라이브러리 드라이버 지원 종료
· ACFSUTIL REPL REVERSE 지원 종료
· 클러스터 도메인 - 도메인 서비스 클러스터 지원 종료
· Adaptive Threshold값 기능을 위한 DBSNMP 패키지 지원 종료
· Policy- Managed 데이터베이스 배포지원 종료
· 엔터프라이즈 사용자 보안, 사용자 마이그레이션 유틸리티 지원 종료
· Oracle Enterprise Manager Database Express 지원 종료
· Oracle Wallet Manager(OWM) 지원 종료
· RASADM 지원 종료
· Oracle Label Security Security 지원 종료
· RADIUS 사용자에게 관리 권한 부여 지원 종료
· TDE 암호화 PKI 키 지원 종료
· GOST 및 SEED TDE 암호화 알고리즘 지원 종료
· Oracle Database 10G 암호 검증 기능 지원 종료
· Transport Layer Security 버전 1.0 및 1.1 지원 종료
· Unix Crypt (MD5crypt) 비밀번호 검증 기능 지원 종료
· FIPS Strenge 80 암호화 지원 종료
· Diffie-Hellman 익명 암호화 지원 종료
· Oracle Database Extensions for .NET 지원 종료
· Quality of Service Management 지원 종료
· Tradition Auditing 감사 지원 종료 (Unified Auditing 이 기본)
· config.sh 지원 종료 (gridSetup.sh 만 사용)
· OLS 테이블의 LABELS 열 지원 종료
· 32 비트 Oracle Database
· 고 가용성을위한 Oracle GoldenGate 복제 지원 종료
· 그리드 인프라 관리 저장소 (GIMR) 지원 종료
· 데이터 복구 어드바이저 (DRA) 지원 종료
· DBUA 및 수동 업그레이드 방법 지원 종료 (AutoUpgrade 만 사용권장)
· Oracle Real Application Testing을 통한 Oracle Data Masking and Subsetting 지원 종료
· Shared Grid Naming Sevice 옵션 지원 종료
· DBMS_AUDIT_MGMT.FLUSH_UNIFIED_AUDIT_TRAIL 프로시저 지원 종료
· AUDIT_TRAIL_PROPERTY 매개 변수 AUDIT_TRAIL_WRITE 모드 지원 종료
· CTSS 시간 동기화 서비스 지원 종료
· Oracle Connection Manager 매개 변수 (CMAN) 암호 액세스 지원 종료
· EUS (Enterprise User Security) 현재 사용자 데이터베이스 링크 지원 종료
· oracle.jdbc.rowset 패키지 지원 종료
· IBM AIX에서 ACFS 지원 종료
· RECOVER ... SNAPSHOT TIME 지원 종료
· Oracle ASM 필터 드라이버 (ASMFD) 지원 종료
2025. 12. 9. 14:23 오라클
Oracle AI 26ai Linux x86-64 on-premise 버전 출시예정!!
드디어 Oracle AI 26ai on premises 버전이 2026년 1월경 Release 되는 것으로 발표가 되었다.
Oracle AI Database 26ai coming soon for Linux x86-64 on-premises platforms | database
Oracle AI Database 26ai coming soon for Linux x86-64 on-premises platforms
Big news for our on‑premises community: Oracle AI Database 26ai Enterprise Edition for Linux x86‑64 will be released in January 2026 as part of the quarterly Release Update (version 23.26.1). Oracle Engineering has been hard at work building a new generation of database that architects AI and Data together, and delivers AI-native data management on all the leading cloud platforms. Oracle AI Database is already available as an Oracle‑managed service in Oracle Cloud Infrastructure, Azure, Google Cloud, and AWS, as well as on Oracle engineered systems. Now that we have delivered Oracle AI Database on all leading clouds, we are making it available for on‑premises Linux x86-64 platforms, giving you even more choice to simplify architectures, accelerate AI‑driven development, and meet your security and performance needs no matter where your data lives.
This much‑anticipated milestone brings to your data centers the full power of 26ai, which includes AI Vector Search, globally distributed database with RAFT‑based replication, in‑database SQL firewall, quantum-resistant encryption, True Cache, JSON Relational Duality, Apache Iceberg Lakehouse support, and hundreds of additional new features.
For highlights about key capabilities in Oracle AI Database 26ai, see this blog post or watch this video.
Please continue to refer to My Oracle Support (MOS) Doc ID: 742060.1 for the latest information about Oracle Database release and support schedules.
2025. 12. 3. 22:16 내가 읽은 책
그녀를 지키다 - 장 밥티스트 안드레아
2025. 11. 28. 09:54 오라클
23ai Hidden parameter 확인 (23.7 버전 기준)
23ai Hidden parameter 확인 (23.7 버전 기준)
일반 Parameter 포함 7206개
DBFIPS_140 FALSE
_4030_dump_bitvec 4095
_4031_dump_bitvec 67194879
_4031_dump_interval 300
_4031_max_dumps 100
_4031_sga_dump_interval 3600
_4031_sga_max_dumps 10
_AllowMultInsteadofDDLTrigger 0
_EnableDDLTtriggerTracing FALSE
_EnableShadowTypes FALSE
_ILM_FILTER_TIME 0
_ILM_FILTER_TIME_LOWER 0
_ILM_POLICY_NAME FALSE
_NUMA_bind_mode default
_NUMA_float_spawner FALSE
_NUMA_instance_mapping Not specified
_NUMA_pool_reservation_trace FALSE
_NUMA_pool_size Not specified
_PX_use_large_pool FALSE
_REMOVE_INACTIVE_STANDBY_TDE_MASTER_KEY FALSE
_REMOVE_STDBY_OLD_KEY_AFTER_CHECKPOINT_SCN TRUE
_STFForceTranslateOracleSQL FALSE
_STFTranslateDynamicSQL FALSE
_VIEW_DICTIONARY_ACCESSIBILITY FALSE
__asm_max_connected_clients 3
__bct_last_dba_buffer_size 0
__cnf 100
__data_transfer_cache_size 0
__datamemory_area_size 0
__db_16k_cache_xmem_size_metadata 0
__db_2k_cache_xmem_size_metadata 0
__db_32k_cache_xmem_size_metadata 0
__db_4k_cache_xmem_size_metadata 0
__db_8k_cache_xmem_size_metadata 0
__db_cache_size 2801795072
__db_cache_xmem_size_metadata 0
__db_keep_cache_xmem_size_metadata 0
__db_pmem_direct_map_size_metadata 0
__db_recycle_cache_xmem_size_metadata 0
__dg_broker_service_names
__inmemory_ext_roarea 0
__inmemory_ext_rwarea 0
__inmemory_size 0
__java_pool_size 0
__kstrc_qa_credentials
__large_pool_size 16777216
__latch_test_param 0
__maintenance_is_planned 0
__memoptimize_xmem_pool_size_metadata 0
__oracle_base /u01/app/oracle
__persistent_cl2_slave_size 0
__pga_aggregate_target 1241513984
__pre_update_rolling_rrp_compatibility
__previous_rolling_rrp_compatibility
__reload_lsnr 0
__rolling_list_int_param_spare1
__rolling_list_int_param_spare2
__rolling_list_string_param_spare3 default
__rolling_rrp_boolean_param_spare1 FALSE
__rolling_rrp_compatibility
__rolling_rrp_compatibility_homogeneity_check
__rolling_rrp_disabled
__rolling_rrp_exceptions
__rolling_rrp_int_spare1 0
__rolling_rrp_int_spare2 0
__rolling_rrp_intent_to_rollback FALSE
__rolling_rrp_last_enable_version 23.1.0
__rolling_rrp_previous_last_enable_version
__rolling_rrp_simulate_binary_rrp 0
__rolling_rrp_simulate_binary_rrp_with_cb 0
__rolling_rrp_simulate_one_off_rrp
__rolling_rrp_string_spare1
__rolling_rrp_string_spare2
__sess_template_test_attrs FALSE
__sga_current_size 0
__sga_target 3690987520
__shared_io_pool_size 134217728
__shared_pool_size 704643072
__streams_pool_size 0
__unified_pga_pool_size 0
__wait_test_param 0
_abort_on_mrp_crash FALSE
_abort_recovery_on_join FALSE
_ac_enable_dscn_in_rac FALSE
_ac_strict_SCN_check FALSE
_accept_versions
_aco_disable_options 0
_actgrp_spawn_offload FALSE
_active_dgpdb TRUE
_active_dgpdb_qscn_count 100
_active_instance_count 1024
_active_session_idle_limit 5
_active_session_legacy_behavior FALSE
_active_standby_fast_reconfiguration TRUE
_adaptive_direct_read TRUE
_adaptive_direct_write TRUE
_adaptive_fetch_enabled TRUE
_adaptive_log_file_sync_high_switch_freq_threshold 3
_adaptive_log_file_sync_poll_aggressiveness 0
_adaptive_log_file_sync_sampling_count 128
_adaptive_log_file_sync_sampling_time 3
_adaptive_log_file_sync_sched_delay_window 60
_adaptive_log_file_sync_use_polling_threshold 200
_adaptive_log_file_sync_use_postwait_threshold 50
_adaptive_log_file_sync_use_postwait_threshold_agi 1001
ng
_adaptive_scalable_log_writer_disable_worker_thres 50
hold
_adaptive_scalable_log_writer_enable_worker_aging 999900
_adaptive_scalable_log_writer_enable_worker_thresh 200
old
_adaptive_scalable_log_writer_evaluation_fraction 100
_adaptive_scalable_log_writer_evaluation_interval 15
_adaptive_scalable_log_writer_sampling_count 128
_adaptive_scalable_log_writer_sampling_time 3
_adaptive_window_consolidator_enabled TRUE
_add_col_optim_enabled TRUE
_add_nullable_column_with_default_optim TRUE
_add_stale_mv_to_dependency_list TRUE
_add_trim_for_nlssort TRUE
_addm_auto_actions_enabled TRUE
_addm_auto_enable TRUE
_addm_skiprules
_addm_version_check TRUE
_adg_adt_redirect_apply_lag_threshold 12000
_adg_adt_redirect_catchup_wait_time 12000
_adg_auto_close_pdb TRUE
_adg_count_beyond_limit 0
_adg_defer_segstat TRUE
_adg_distributed_lockmaster FALSE
_adg_influx_qscn_gap 0
_adg_instance_recovery TRUE
_adg_objectlock_attempts 2
_adg_objectlock_maxnum 1000
_adg_objectlock_timeout 0
_adg_parselock_timeout 0
_adg_parselock_timeout_sleep 100
_adg_redirect_upd_to_primary_max_retries 500
_adjust_literal_replacement FALSE
_adr_migrate_runonce TRUE
_advanced_index_compression_cmp_options 0
_advanced_index_compression_opt_options 0
_advanced_index_compression_options 0
_advanced_index_compression_options_value 0
_advanced_index_compression_recmp_crsz 10
_advanced_index_compression_recmp_cusz 90
_advanced_index_compression_recmp_nprg 10
_advanced_index_compression_trace 0
_advanced_index_compression_tst_options 0
_advanced_index_compression_umem_options 2147483647
_afd_disable_fence FALSE
_affected_row_threshold_for_dst_upgrade_using_dml 100
_affinity_on TRUE
_age_block_batch_timeout_ms 1000
_aged_out_cursor_cache_time 300
_aggregation_optimization_settings 0
_ahub_data_file_loc
_aiowait_timeouts 100
_alert_expiration 604800
_alert_message_cleanup 1
_alert_message_purge 1
_alert_post_background 1
_alert_segment_size 50
_alert_segment_textfile TRUE
_alert_segments_max 20
_all_shared_dblinks
_all_sync_restrict_list
_alloc_perm_as_free FALSE
_allocate_creation_order FALSE
_allocate_flashback_buffer FALSE
_allocation_update_interval 3
_allow_cell_smart_scan_attr TRUE
_allow_commutativity TRUE
_allow_compatibility_adv_w_grp FALSE
_allow_connected_user_dblink TRUE
_allow_convert_to_standby FALSE
_allow_cross_endian_dictionary FALSE
_allow_cross_version_ddl 0
_allow_ddl_in_fga_handler FALSE
_allow_drop_snapshot_standby_grsp FALSE
_allow_drop_ts_with_grp FALSE
_allow_error_simulation FALSE
_allow_fallback_to_dbkey FALSE
_allow_fga_mixed_mode FALSE
_allow_file_1_offline_error_1245 FALSE
_allow_imc_adaptive_grow TRUE
_allow_imc_adaptive_shrink TRUE
_allow_insert_with_update_check FALSE
_allow_level_without_connect_by FALSE
_allow_modify_lockdown FALSE
_allow_operator_access FALSE
_allow_privileged_session_dblink_conn FALSE
_allow_read_only_corruption FALSE
_allow_resetlogs_corruption FALSE
_allow_same_cdb_refresh_switchover TRUE
_allow_self_signed_cert FALSE
_allow_snr_rac FALSE
_allow_synonym_for_credential TRUE
_allow_sysosenv_context FALSE
_allow_system_wallet TRUE
_allow_terminal_recovery_corruption FALSE
_allow_traditional_audit_configuration FALSE
_allow_triggers_on_vpd_table FALSE
_allow_unenc_ts_without_tde_master_key FALSE
_allow_user$_col_update NONE
_allow_xdb_anonymous_logon FALSE
_allowed_pvf_owners
_alter_adg_redirect_behavior none
_alter_table_modify_column_nop_flags 1
_alter_upgrade_signature_only FALSE
_alternate_iot_leaf_block_split_points TRUE
_always_anti_join CHOOSE
_always_semi_join CHOOSE
_always_star_transformation FALSE
_always_vector_transformation FALSE
_analyze_comprehensive FALSE
_and_pruning_enabled TRUE
_ansi_join_mv_rewrite_enabled TRUE
_app_container_debug 0
_app_default_containers FALSE
_app_ignore_errors TRUE
_app_replay_silent_errors FALSE
_appcont_error_convert ON
_application_purge_enabled TRUE
_application_script FALSE
_apppdb_multi_slave_sync FALSE
_appqos_cdb_setting 0
_appqos_po_multiplier 1000
_appqos_qt 10
_approx_cnt_distinct_gby_pushdown choose
_approx_cnt_distinct_optimization 0
_approx_perc_sampling_err_rate 2
_approx_percentile_optimization 0
_aps_flush_enabled FALSE
_apx_root_directory APX
_aq_Txn_ht_sz 1024
_aq_addpt_batch_size 1
_aq_bufop_svc_create 1
_aq_deq_flowcontrol 0
_aq_dly_bkt 60
_aq_dq_prefetch_Siz 5
_aq_dqblocks_in_cache 0
_aq_droppt_batch_size 5
_aq_free_list_pools 10
_aq_init_shards 5
_aq_ipc_max_slave 10
_aq_latency_absolute_threshold 300
_aq_latency_relative_threshold 100
_aq_lb_cycle 120
_aq_lb_garbage_col_interval 600
_aq_lb_stats_collect_cycle 45
_aq_lb_subht_bkt_ltch 32
_aq_lb_subht_elm_ltch 128
_aq_lookback_size 60
_aq_max_pdb_close_msg 1
_aq_max_scan_delay 1500
_aq_opt_background_enabled TRUE
_aq_opt_enabled TRUE
_aq_opt_fudge_factor 500
_aq_opt_list_oper_latches 8
_aq_opt_min_evict_memory 0
_aq_opt_preevict_dop 3
_aq_opt_prefetch_dop 3
_aq_opt_prefetch_horizon 60
_aq_opt_stat_window 21600
_aq_opt_stop_stat FALSE
_aq_pt_processes 10
_aq_pt_shrink_frequency 60
_aq_pt_statistics_window 60
_aq_qt_prefetch_Size 5
_aq_queue_global_service
_aq_retry_timeouts 0
_aq_scramble_deq 0
_aq_scrambled_deqlog 1
_aq_shard_bitmap_child_latches 32
_aq_shard_child_latches 512
_aq_shard_prty_latches 16
_aq_shard_retry_child_latches 32
_aq_shard_sub_child_Elem_latches 1024
_aq_shard_sub_child_latches 512
_aq_shard_txn_child_latches 128
_aq_stop_backgrounds FALSE
_aq_streaming_threshold 10485760
_aq_subshard_Size 20000
_aq_subshards_per_dqpartition 1
_aq_subshards_per_qpartition 1
_aq_tm_deqcountinterval 0
_aq_tm_processes_dump_interval 12
_aq_tm_scanlimit 0
_aq_tm_statistics_duration 0
_aq_truncpt_batch_size 1
_aq_uncached_stats 0
_aq_x_mode 1
_aq_x_msg_size 32768
_aqsharded_cache_limit 0
_aqsharded_cache_policy_lowmem 0
_aqsharded_cached_hint 0
_aqsharded_enq_fresh_ptn_reload TRUE
_aqsharded_lowmem_timeout 1000
_aqsharded_reload_tune 2
_arch_comp_dbg_scan 0
_arch_comp_dec_block_check_dump 1
_arch_compress_checksums FALSE
_arch_compression TRUE
_arch_io_slaves 0
_array_cdb_view_enabled TRUE
_array_update_vector_read_enabled FALSE
_ash_disk_filter_ratio 10
_ash_disk_write_enable TRUE
_ash_dummy_test_param 0
_ash_eflush_trigger 66
_ash_enable TRUE
_ash_min_mmnl_dump 90
_ash_progressive_flush_interval 300
_ash_sample_all FALSE
_ash_sampling_interval 1000
_ash_size 1048618
_asm_access auto
_asm_access_assume_local FALSE
_asm_acd_chunks 1
_asm_admin_with_sysdba FALSE
_asm_allow_appliance_dropdisk_noforce FALSE
_asm_allow_appliance_offlineonline FALSE
_asm_allow_dangerous_unprotected_volumes FALSE
_asm_allow_dgname_special_chars FALSE
_asm_allow_foreign_siteguids
_asm_allow_lvm_resilvering TRUE
_asm_allow_older_clients FALSE
_asm_allow_only_raw_disks TRUE
_asm_allow_prepare_split TRUE
_asm_allow_small_memory_target FALSE
_asm_allow_system_alias_rename FALSE
_asm_allow_unsafe_reconnect TRUE
_asm_allowdegeneratemounts FALSE
_asm_appliance_config_file
_asm_appliance_disable_fg_check FALSE
_asm_appliance_ignore_oak FALSE
_asm_appliance_slot_from_path FALSE
_asm_asmb_exa_rcvto 30
_asm_asmb_max_wait_timeout 6
_asm_asmb_rcvto 10
_asm_async_scrub_reap_wait 100000
_asm_ate_conversion_batch_size 1024
_asm_audit_sp_param
_asm_ausize 1048576
_asm_auto_online_interval
_asm_automatic_rezone TRUE
_asm_avoid_pst_scans TRUE
_asm_bdbmr_max_ent_inprgrs 2000
_asm_blksize 4096
_asm_br_listener_port 51521
_asm_brfuzz_ios_lsnrport 0
_asm_buffer_overlap_tracer FALSE
_asm_cancel_alert_time 600
_asm_cancel_delta 75000
_asm_cclient_cleanup_timeout 300
_asm_check_for_misbehaving_cf_clients FALSE
_asm_checksum_migration_chunk_size 128
_asm_compatibility 23.1
_asm_dba_batch 500000
_asm_dba_spcchk_thld 100000
_asm_dba_threshold 0
_asm_dbmsdg_nohdrchk FALSE
_asm_dependency_under_cfenqueue TRUE
_asm_diag_dead_clients FALSE
_asm_direct_con_expire_time 120
_asm_disable_amdu_dump FALSE
_asm_disable_async_msgs FALSE
_asm_disable_dangerous_failgroup_checking FALSE
_asm_disable_exadata_hard_appliance_check FALSE
_asm_disable_failgroup_count_checking FALSE
_asm_disable_failgroup_size_checking FALSE
_asm_disable_multiple_instance_check FALSE
_asm_disable_patch_compat FALSE
_asm_disable_proact_client_cleanup FALSE
_asm_disable_profilediscovery FALSE
_asm_disable_pstcard FALSE
_asm_disable_request_tracer TRUE
_asm_disable_smr_creation FALSE
_asm_disable_ufg_dump FALSE
_asm_disable_ufgmemberkill FALSE
_asm_disable_vtoc_check FALSE
_asm_disable_vxn_map_messages FALSE
_asm_disk_repair_time 14400
_asm_diskerr_traces 2
_asm_diskgroup_renew_timeout 20
_asm_diskgroups2
_asm_diskgroups3
_asm_diskgroups4
_asm_dump_split_pw 10
_asm_dynamic_timeout_interval 20
_asm_emulate_nfs_disk FALSE
_asm_emulmax 10000
_asm_emultimeout 0
_asm_enable_batch_scrub TRUE
_asm_enable_kfios FALSE
_asm_enable_kfks FALSE
_asm_enable_lostwrite_scrub TRUE
_asm_enable_map_share TRUE
_asm_enable_multiple_asmb TRUE
_asm_enable_parity_scrub FALSE
_asm_enable_parityfile_creation TRUE
_asm_enable_pstreloc_on_rm FALSE
_asm_enable_repair_lostwrite_scrub FALSE
_asm_enable_vfreloc_on_rm FALSE
_asm_enable_xrov FALSE
_asm_evenread 2
_asm_evenread_alpha 0
_asm_evenread_alpha2 0
_asm_evenread_faststart 0
_asm_fail_random_rx FALSE
_asm_fd_cln_idle_sess_twait 60000000
_asm_fd_cln_on_fg TRUE
_asm_fob_tac_frequency 9
_asm_force_parity_extent_check FALSE
_asm_force_paritycheck_rebalance FALSE
_asm_force_quiesce FALSE
_asm_force_vam FALSE
_asm_frag_threshold 50
_asm_global_dump_level 267
_asm_hard_check TRUE
_asm_hbeatiowait 120
_asm_hbeatwaitquantum 2
_asm_healthcheck_timeout 180
_asm_identify_advisory_locks 2
_asm_idn_processes 0
_asm_imbalance_tolerance 3
_asm_instlock_quota 0
_asm_ios_network_domains 0
_asm_ios_network_processes 0
_asm_iosconnect_timeout 0
_asm_iosfailover_freq 3
_asm_iosfailover_timeout 5
_asm_iostat_latch_count 31
_asm_iowp_max_async 0
_asm_kfdpevent 0
_asm_kill_unresponsive_clients TRUE
_asm_libraries ufs
_asm_log_scale_rebalance FALSE
_asm_lsod_bucket_size 67
_asm_max_aux_cods 5
_asm_max_clients 1000
_asm_max_cod_strides 10
_asm_max_connected_clients 3
_asm_max_kfsg_free_heap_perc 10
_asm_max_kfsg_free_heap_size 524288000
_asm_max_occupied 90
_asm_max_parallelios 256
_asm_max_redo_buffer_size 2097152
_asm_maxio 1048576
_asm_min_compatibility 19.0
_asm_min_occupied 50
_asm_netp_factor 0
_asm_netp_iosize 0
_asm_network_timeout 1
_asm_networks
_asm_no_shared_maplock FALSE
_asm_node_number
_asm_node_site_guid
_asm_nodekill_escalate_time 180
_asm_noevenread_diskgroups
_asm_oda_type
_asm_odapremchk TRUE
_asm_offline_wait_timeout 300
_asm_offload_all FALSE
_asm_ownerid_trace_timeout 3600
_asm_partner_target_disk_part 8
_asm_partner_target_fg_rel 4
_asm_preopen_mincnt 100
_asm_preopen_workers 4
_asm_primary_load 1
_asm_primary_load_cycles TRUE
_asm_procs_trace_diskerr 5
_asm_proxy_online_restart 0
_asm_proxy_startwait 60
_asm_pst_rsinfo 0
_asm_pstonpartners TRUE
_asm_quorum_hb TRUE
_asm_random_zone FALSE
_asm_read_cancel DYNAMIC
_asm_read_cancel_back_out 5000
_asm_read_cancel_dynamic_delta 20
_asm_read_cancel_timeout_limit 15000
_asm_read_cancel_timeout_min 5000
_asm_rebalance_estimates_process TRUE
_asm_rebalance_plan_size 120
_asm_rebalance_rate_alpha 0
_asm_rebalance_rate_alpha2 0
_asm_rebalance_rate_faststart 10
_asm_rebalance_rate_interval 9000
_asm_rebalance_space_errors 1000
_asm_reloc_cic FALSE
_asm_reloc_restart_timeout 600
_asm_relocation_async_lock_count 128
_asm_relocation_ignore_hard_failure 0
_asm_relocation_scheme alloc_p2 alloc_s3 reb_p2 reb_s1 bal_p2 bal_s3 prep
_p2 prep_s3
_asm_relocation_trace FALSE
_asm_remote_client_timeout 300
_asm_repairquantum 60
_asm_reserve_slaves TRUE
_asm_resyncCkpt 6000
_asm_root_directory ASM
_asm_runtime_capability_volume_support FALSE
_asm_scrub_async TRUE
_asm_scrub_disable_cod FALSE
_asm_scrub_limit AUTO
_asm_scrub_max_cod_wait 5
_asm_scrub_strict FALSE
_asm_scrub_unmatched_dba 1024
_asm_secondary_load 10000
_asm_secondary_load_cycles FALSE
_asm_serialize_volume_rebalance FALSE
_asm_shadow_cycle 3
_asm_shared_pool_latch_timeout 30
_asm_showpdb_asmtbl FALSE
_asm_skip_cod_recovery_diskgroups
_asm_skip_dbfile_ios FALSE
_asm_skip_diskval_check FALSE
_asm_skip_rename_check FALSE
_asm_skip_resize_check FALSE
_asm_slow_client_timeout_percentage 50
_asm_ssd_max_timeout_limit 2400
_asm_storagemaysplit FALSE
_asm_stripesize 131072
_asm_stripewidth 8
_asm_sync_rebalance FALSE
_asm_tcp_user_timeout 1
_asm_trace_limit_timeout 30000
_asm_ufg_nw_wait_timeout 10
_asm_usd_batch 64
_asm_wait_time 18
_asm_write_badfdata_in_contentcheck FALSE
_asm_write_cancel AUTO
_asm_write_cancel_dynamic_delta 30
_asm_write_cancel_timeout_limit 90000
_asm_write_cancel_timeout_min 15000
_asm_write_cancel_timeout_percentage 30
_asm_xrov_cachelgio 1
_asm_xrov_nstats 0
_asm_xrov_nvios 24
_asm_xrov_rsnmod 2
_asm_xrov_single FALSE
_asm_zero_power_limit
_asmsid asm
_assert_encrypted_tablespace_blocks TRUE
_assert_invalidation 0
_assert_single_current_buffer FALSE
_assm_auto_tracing_threshold 0
_assm_default TRUE
_assm_examination_blocks_threshold 8196
_assm_examination_enable_sla FALSE
_assm_examination_time_threshold 60
_assm_force_fetchmeta FALSE
_assm_high_gsp_threshold 11024
_assm_l1cleanout_throttle_time 3
_assm_latency_sampling_frequency 0
_assm_low_gsp_threshold 10000
_assm_segment_extension_percent 100
_assm_segment_repair_bg TRUE
_assm_segment_repair_fg 0
_assm_segment_repair_maxblks 4294967294
_assm_segment_repair_timelimit 60
_assm_space_cache_hb_expire 3
_assm_space_cache_max_segments 1024
_assm_test_force_rej 0
_assm_test_force_rej2 0
_assm_test_reentrant_gsp FALSE
_async_recovery_claims TRUE
_async_recovery_reads TRUE
_async_rta_broadcast FALSE
_async_scn_sync OFF
_async_ts_threshold 1
_atp_block_size_default TRUE
_audit_operator_access FALSE
_auto_assign_cg_for_sessions FALSE
_auto_bmr enabled
_auto_bmr_bg_time 3600
_auto_bmr_fc_time 60
_auto_bmr_file_header TRUE
_auto_bmr_max_rowno 1024
_auto_bmr_noretry_window 1800
_auto_bmr_pub_timeout 10
_auto_bmr_req_timeout 60
_auto_bmr_sess_threshold 30
_auto_bmr_sys_threshold 100
_auto_clustering FALSE
_auto_clustering_sqlset
_auto_db_lost_write_protect_fsfo_lag_limit_percent 67
_auto_db_lost_write_protect_max_lag_secs 60
_auto_dismount_on_pdb_close FALSE
_auto_export_preplugin_backup TRUE
_auto_im_batch_size 10
_auto_im_cache_join_opt FALSE
_auto_im_join_group FALSE
_auto_im_max_perf_candidates 3
_auto_im_monitor_interval 1440
_auto_im_optimized_arithmetic FALSE
_auto_im_perf_threshold 10
_auto_im_play_area 10
_auto_im_rac_enabled TRUE
_auto_im_task_mode 0
_auto_im_vector_gby_opt FALSE
_auto_manage_asm_diskgroup_power_limit_max 32
_auto_manage_asm_diskgroup_power_limit_min 1
_auto_manage_enable_offline_check TRUE
_auto_manage_enable_smart_rebalance TRUE
_auto_manage_exadata_disks TRUE
_auto_manage_infreq_tout 0
_auto_manage_ioctl_bufsz 8192
_auto_manage_max_num_cells_offline 65535
_auto_manage_max_online_tries 3
_auto_manage_num_pipe_msgs 1000
_auto_manage_num_tries 2
_auto_manage_online_tries_expire_time 86400
_auto_manage_power_limit_adjustment_disabled FALSE
_auto_manage_remount_eligible_dg TRUE
_auto_manage_smart_rebalance_grace_period_in_min 0
_auto_manage_smart_rebalance_space_threshold 0
_auto_mv_enabled FALSE
_auto_rcv_pdb_open 1
_auto_rekey_during_mrcv TRUE
_auto_temp_shrink_pdb_floor 0
_autocomp_inact_pct 98
_autocomp_move_max_mb 128
_autoconf_mv_rewrite_metadata TRUE
_automatic_maintenance_test 0
_automemory_broker_interval 3
_autoptn_config
_autoptn_costing FALSE
_autoptn_flags 0
_autoptn_translate_table_name
_autoptn_workload_id 0
_autosts_capture_control 3
_autosts_long_interval 0
_autosts_retention_interval 31
_autosts_short_interval 300
_autotask_max_window 480
_autotask_min_window 15
_autotask_test_action 0
_autotask_test_name N/A
_autotbs_management_enabled FALSE
_autotbs_quota_override FALSE
_autotune_gtx_idle_time 600
_autotune_gtx_interval 5
_autotune_gtx_threshold 60
_aux_dfc_keep_time 1440
_aux_storage_size 0
_available_core_count 0
_avoid_scn_growth 1
_awr_adg_flush_method SYSTEM_DEFINED
_awr_cdbperf_threshold 21
_awr_colored_app_enabled FALSE
_awr_corrupt_mode FALSE
_awr_data_masking FALSE
_awr_disabled_flush_tables
_awr_disabled_purge_tables
_awr_enable_pdb_snapshots TRUE
_awr_flush_threshold_metrics TRUE
_awr_flush_workload_metrics FALSE
_awr_hub_autoimp_inline FALSE
_awr_hub_consumer_group ORA$AUTOTASK
_awr_hub_num_conc_imp 2
_awr_incremental_flush_enabled TRUE
_awr_max_registrations 1024
_awr_metrics_use_mmnl FALSE
_awr_mmon_cpuusage TRUE
_awr_mmon_deep_purge_all_expired FALSE
_awr_mmon_deep_purge_extent 7
_awr_mmon_deep_purge_interval 7
_awr_mmon_deep_purge_numrows 5000
_awr_overflow_enabled FALSE
_awr_partition_interval 0
_awr_pdb_registration_enabled FALSE
_awr_report_gen_method LEGACY
_awr_restrict_mode FALSE
_awr_snapshot_level BESTFIT
_awr_sql_child_limit 200
_awr_sqltext_redaction FALSE
_awr_warehouse_enabled TRUE
_awrextr_include_sqlmon FALSE
_b_tree_bitmap_plans TRUE
_ba_cf_trace_buffer_size 131072
_ba_container_filesystem_ausize 4194304
_ba_max_containers 0
_ba_max_groups 0
_ba_max_seg_bytes 4000
_ba_timeouts_enabled TRUE
_background_process_opts 0
_backup_align_write_io TRUE
_backup_appliance_enabled FALSE
_backup_automatic_retry 10
_backup_block0 default
_backup_bool_spare1 FALSE
_backup_bool_spare2 FALSE
_backup_bool_spare3 FALSE
_backup_bool_spare4 FALSE
_backup_compress FALSE
_backup_disk_bufcnt 0
_backup_disk_bufsz 0
_backup_disk_io_slaves 0
_backup_dynamic_buffers TRUE
_backup_encrypt_opt_mode 4294967294
_backup_file_bufcnt 0
_backup_file_bufsz 0
_backup_int_spare1 4294967294
_backup_int_spare2 4294967294
_backup_int_spare3 4294967294
_backup_int_spare4 4294967294
_backup_interrupt_wait_time 1000
_backup_io_pool_size 1048576
_backup_kgc_bz2_bufsz 0
_backup_kgc_bz2_niters 0
_backup_kgc_bz2_type 0
_backup_kgc_bzip2_blksiz 9
_backup_kgc_lzo_bufsz 262144
_backup_kgc_medium_scheme DEFAULT
_backup_kgc_scheme ZLIB
_backup_kgc_zlib_complevel 1
_backup_kgc_zlib_memlevel 8
_backup_kgc_zlib_windowbits 15
_backup_kgc_zstd_bufsz 262144
_backup_kgc_zstd_complevel 3
_backup_kgc_zstd_high_complevel 14
_backup_ksfq_bufcnt 0
_backup_ksfq_bufmem_max 268435456
_backup_ksfq_bufsz 0
_backup_max_gap_size 4294967294
_backup_max_wallet_session 50
_backup_min_ct_unused_optim 2097152
_backup_seq_bufcnt 0
_backup_seq_bufsz 0
_backup_text_spare1
_backup_text_spare2
_backup_text_spare3
_backup_text_spare4
_bct_auto_ctf_shrink FALSE
_bct_bitmaps_per_file 8
_bct_buffer_allocation_max 1073741824
_bct_buffer_allocation_min_extents 1
_bct_buffer_allocation_size 2097152
_bct_chunk_size 0
_bct_crash_reserve_size 262144
_bct_dba_buffer_reap_threshold 2000
_bct_ext_alo_count 320
_bct_ext_min_count 320
_bct_file_block_size 0
_bct_file_extent_size 0
_bct_fixtab_file
_bct_health_check_interval 0
_bct_imt_suppress_charset_validation 3
_bct_min_switch_freq 43200
_bct_mrp_timeout 5
_bct_public_dba_buffer_dynresize 2
_bct_public_dba_buffer_dynresize_delay 3600
_bct_public_dba_buffer_maxsize 0
_bct_public_dba_buffer_size 0
_bct_wait_before_trace_dump 120
_bctab_max_system_chains 1024
_bctab_optimize_commit_performance FALSE
_beirut_timeout_minutes 10
_bequeath_via_broker FALSE
_bg_dgpdb_rcv_parallelism 0
_bg_spawn_diag_opts 0
_big_scn_test_mode 2
_bigdata_external_table TRUE
_bigdata_offload_flag FALSE
_bigram_dependency_percentage 5
_bind_undotbs DISABLED
_bitmap_or_improvement_enabled TRUE
_block_change_tracking_file
_block_corruption_track_limit 1000
_block_dump_assert FALSE
_block_level_offload_high_lat_thresh 40000
_block_sample_readahead_prob_threshold 10
_blockchainHeapSize 0
_blockchainTracing 0
_blockchain_forced_off NOT_SET
_blockchain_immutable_table
_blockchain_txn_apis_enabled TRUE
_blockchain_txn_test_lvl 0
_blockhm_flush_period 3600
_blocking_sess_graph_cache_size
_blocks_per_cache_server 1
_bloom_extent_size 0
_bloom_filter_debug 0
_bloom_filter_enabled TRUE
_bloom_filter_multi_bit FALSE
_bloom_filter_ratio 35
_bloom_filter_setops_enabled TRUE
_bloom_filter_size 0
_bloom_folding_density 16
_bloom_folding_enabled TRUE
_bloom_folding_min 0
_bloom_max_size 262144
_bloom_max_wait_time 50
_bloom_minmax_enabled TRUE
_bloom_predicate_enabled TRUE
_bloom_predicate_offload TRUE
_bloom_pruning_enabled TRUE
_bloom_pruning_setops_enabled TRUE
_bloom_pushing_folding_density 4
_bloom_pushing_max 512
_bloom_pushing_total_max 20971520
_bloom_rm_filter FALSE
_bloom_serial_filter ON
_bloom_sm_enabled TRUE
_bloom_use_shared_pool FALSE
_bloom_wait_on_rac FALSE
_boc_mode AUTO
_boc_rdma_wait_time 0
_bps_sanity_checks FALSE
_branch_tagging TRUE
_broadcast_scn_mode 1
_broadcast_scn_wait_timeout 10
_broker_imc_max_utilstep 95
_bsln_adaptive_thresholds_enabled TRUE
_bt_mmv_query_rewrite_enabled TRUE
_buddy_instance 1
_buddy_instance_num_read_buffers 4
_buddy_instance_scan_phase_threshold 3
_buddy_instance_start_rba_timeout 9
_buffer_busy_wait_timeout 100
_buffer_requests_to_drain 5
_buffered_message_spill_age 300
_buffered_publisher_flow_control_threshold 0
_bufq_stop_flow_control FALSE
_build_deferred_mv_skipping_mvlog_update TRUE
_bump_highwater_mark_count 0
_bwr_for_flushed_pi TRUE
_bypass_sensitive_context FALSE
_bypass_srl_for_so_eor FALSE
_bypass_xplatform_error FALSE
_c3_external_scn_rejection_threshold_hours 4464
_cache_fusion_pipelined_updates TRUE
_cache_fusion_pipelined_updates_enable
_cache_lobs_pga_limit 75
_cache_orl_during_open ALL
_cache_stats_monitor FALSE
_capability_simulate
_capture_buffer_size 65536
_capture_pgadep 0
_capture_publisher_flow_control_threshold 0
_case_sensitive_logon TRUE
_catalog_foreign_restore FALSE
_catalog_soft_assert_diag FALSE
_causal_standby_wait_timeout 20
_cdb_compatible TRUE
_cdb_cross_container 65535
_cdb_disable_pdb_limit FALSE
_cdb_fleet_sync_timeout 10
_cdb_init_batch_size 100
_cdb_port 0
_cdb_rac_affinity TRUE
_cdb_special_old_xplan FALSE
_cdb_spfile_inherit FALSE
_cdb_svlt_use_tcps FALSE
_cdb_view_no_skip_migrate FALSE
_cdb_view_no_skip_restricted FALSE
_cdb_view_parallel_degree 65535
_cdb_view_prefetch_batch_size 200
_cdb_view_rc_shelflife 30
_cdb_view_recursive_px_enabled TRUE
_cdb_view_serial_ok FALSE
_cdc_subscription_owner
_cdmp_diagnostic_level 2
_cell_fast_file_create TRUE
_cell_fast_file_restore TRUE
_cell_file_format_chunk_size 0
_cell_index_scan_enabled TRUE
_cell_iot_scan_enabled TRUE
_cell_materialize_all_expressions FALSE
_cell_materialize_virtual_columns TRUE
_cell_metadata_compression AUTO
_cell_object_expiration_hours 24
_cell_offload_capabilities_enabled 1
_cell_offload_complex_processing TRUE
_cell_offload_expressions TRUE
_cell_offload_grand_total TRUE
_cell_offload_hybrid_processing TRUE
_cell_offload_hybridcolumnar TRUE
_cell_offload_predicate_reordering_enabled FALSE
_cell_offload_sys_context TRUE
_cell_offload_timezone TRUE
_cell_offload_vector TRUE
_cell_offload_vector_groupby TRUE
_cell_offload_vector_groupby_external TRUE
_cell_offload_vector_groupby_fact_key TRUE
_cell_offload_vector_groupby_force FALSE
_cell_offload_vector_groupby_withnojoin TRUE
_cell_offload_virtual_columns TRUE
_cell_range_scan_enabled TRUE
_cell_storidx_minmax_enabled TRUE
_cell_storidx_mode EVA
_cell_trace_size 0
_cellcache_clause_default
_cellcache_default_flags 2
_cellcache_default_new FALSE
_cgs_allgroup_poll_time 20000
_cgs_big_group_enabled FALSE
_cgs_clscevents_dumpinterval 600
_cgs_combine_css_events 31
_cgs_comm_readiness_check 1
_cgs_dball_group_registration local
_cgs_dbgroup_poll_time 600
_cgs_health_check_in_reconfig FALSE
_cgs_memberkill_from_rim_instance FALSE
_cgs_msg_batch_size 4096
_cgs_msg_batching TRUE
_cgs_node_kill_escalation TRUE
_cgs_node_kill_escalation_wait 0
_cgs_os_level_connection_check 1
_cgs_os_level_connection_dynamicthread TRUE
_cgs_os_level_connection_reqno 0
_cgs_publish_netinfo_collect_event_chm rcfg-half-timeout,rcfg-timeout,rcfg-done,idleconn-
half-timeout,idleconn-timeout-imr,idleconn-cln,rcf
g-begin,rcfg-pngchkdone,rcfg-memchg
_cgs_publish_netinfo_collect_event_chmjf TRUE
_cgs_publish_netinfo_collect_event_chmjf_batchsz 0
_cgs_publish_netinfo_collect_event_haip TRUE
_cgs_query_net_interface SCLSI
_cgs_reconfig_extra_wait 3
_cgs_reconfig_poll_time 20
_cgs_reconfig_timeout 0
_cgs_send_timeout 300
_cgs_support_rim_disc TRUE
_cgs_ticket_sendback 50
_cgs_tickets 1000
_cgs_zombie_member_kill_wait 20
_change_vector_buffers 1
_change_vector_read_sample_ratio 0
_check_block_after_checksum FALSE
_check_block_new_invariant_for_flashback FALSE
_check_column_length TRUE
_check_pdbid_in_redo FALSE
_check_ts_threshold 0
_child_read_ahead_dba_check FALSE
_chunk_pruning_enabled TRUE
_cleanout_shrcur_buffers TRUE
_cleanup_file_copy TRUE
_cleanup_rollback_entries 100
_cleanup_timeout 150
_cleanup_timeout_flags 0
_clear_buffer_before_reuse FALSE
_clear_preserved_buffers TRUE
_cli_cachebktalloc 100
_client_enable_auto_unregister FALSE
_client_features_tracking_enable TRUE
_client_ntfn_cleanup_interval 2400
_client_ntfn_max_cleanup_interval 7200
_client_ntfn_pinginterval 75
_client_ntfn_pingretries 6
_client_ntfn_pingtimeout 30000
_client_result_cache_bypass FALSE
_client_result_cache_ramthreshold
_client_result_set_threshold
_client_tstz_error_check TRUE
_clone_during_split TRUE
_clone_one_pdb_recovery FALSE
_close_cached_open_cursors FALSE
_close_deq_by_cond_curs FALSE
_cloud_domain
_cloud_mandatory_profile_setup FALSE
_cloud_name
_cloud_operator_user
_cloud_service_sim 0
_cloud_service_type
_cloud_service_version
_cloud_table_commit_time_limit 0
_cloud_trace 0
_cloud_trace_bucket_fill_percent 50
_cloud_trace_bucket_size 10485760
_cloud_trace_temp_table
_cloudops_common_users
_cloudops_sensitive_masking OFF
_cloudsql_offload_enabled FALSE
_cluster_database_instances 1
_cluster_flash_cache_slave_file
_cluster_flash_cache_slave_size 0
_cluster_instances_number 4
_cluster_library clss
_clusterwide_global_transactions TRUE
_collapse_wait_history FALSE
_collect_tempundo_stats TRUE
_collect_undo_stats TRUE
_column_compression_factor 0
_column_elimination_off FALSE
_column_level_stats OFF
_column_stats_flush_interval 60
_column_stats_max_entries_per_stat 5
_column_stats_mem_limit 10
_column_tracking_level 53
_common_data_view_enabled TRUE
_common_directory_access ALLOW
_common_user_prefix C##
_compilation_call_heap_extent_size 16384
_complex_view_merging TRUE
_component_timing
_composite_interval_partition_creation_opt_enabled TRUE
_compression_above_cache 0
_compression_advisor 0
_compression_chain 90
_compression_compatibility 23.6.0
_con_map_sql_enforcement TRUE
_con_number_reuse_threshold 2147483647
_concurrency_chosen 10
_connect_by_use_union_all TRUE
_connect_string_settings_after_logon_triggers 0
_connect_string_settings_unalterable 0
_connection_broker_error_new_limit 100
_connection_broker_handout_accept FALSE
_connection_broker_host localhost
_connstr_test_param 0
_consensus_follower_election_timeout 12000
_consensus_leader_heartbeat_interval 6000
_consensus_leader_maximum_heartbeats
_consensus_queue_maximum_elements 10
_consensus_slaves_maximum_count 5
_containers_dop_use_remote FALSE
_containers_multiple_ptn_key TRUE
_controlfile_auto_convert_behaviour AUTO_CONVERT
_controlfile_autobackup_delay 300
_controlfile_backup_copy_check TRUE
_controlfile_block_corruption_keep_records 4294967294
_controlfile_block_size 0
_controlfile_cache_bpb 4
_controlfile_cache_bpp 32
_controlfile_cache_recvrbsz 4096
_controlfile_cache_sendrbsz 4096
_controlfile_cache_size 8388608
_controlfile_cache_timer 600
_controlfile_cell_flash_caching 3
_controlfile_enable_rdma_read TRUE
_controlfile_enqueue_dump FALSE
_controlfile_enqueue_holding_time 120
_controlfile_enqueue_holding_time_tracking_size 0
_controlfile_enqueue_timeout 900
_controlfile_section_init_size
_controlfile_section_max_expand
_controlfile_split_brain_check FALSE
_controlfile_update_check LOW
_controlfile_validate_on_search FALSE
_controlfile_verify_on_mount FALSE
_convert_set_to_join FALSE
_coord_message_buffer 0
_corrupted_rollback_segments
_cost_equality_semi_join TRUE
_cp_del_free_sess TRUE
_cp_del_free_sess_limit_secs 1
_cp_num_hash_latches
_cpu_count_startup 0
_cpu_eff_thread_multiplier
_cpu_to_io 0
_cpu_util_adj_force 1
_cpu_util_adj_target 0
_cputime_limit_parallel_fptr 60
_cr_grant_global_role TRUE
_cr_grant_local_role AUTO
_cr_grant_only FALSE
_cr_multiblock_grant_only FALSE
_cr_rollbacks 0
_cr_server_log_flush TRUE
_cr_trc_buf_size 8192
_crash_domain_on_exception 0
_create_idx_from_constraint FALSE
_create_pdb_disable_mirror_reads FALSE
_create_pdb_flashback_barrier FALSE
_create_stat_segment 0
_create_table_in_any_cluster FALSE
_cross_con_collection TRUE
_cross_con_remove_pushed_preds FALSE
_cross_con_row_count FALSE
_cross_region_refclone TRUE
_crs_2phase bypass
_cstats_enabled FALSE
_ctas_numfrags_hint 0
_ctc_no_pdb_shrink_check 0
_ctex_fk_copy_mode 1
_cu_row_locking 0
_current_session_at_dbtimezone FALSE
_current_time_at_dbtimezone FALSE
_cursor_bind_capture_area_size 400
_cursor_bind_capture_interval 900
_cursor_cache_time 900
_cursor_db_buffers_pinned 1051
_cursor_diagnostic_node_agedout_count 100
_cursor_features_enabled 2
_cursor_obsolete_threshold 8192
_cursor_plan_enabled TRUE
_cursor_plan_hash_version 1
_cursor_plan_unparse_enabled TRUE
_cursor_reload_failure_threshold 20
_cursor_runtimeheap_memlimit 5242880
_cursor_stats_enabled TRUE
_cursor_stats_purge_threshold 0
_cvw_enable_weak_checking TRUE
_cvw_examine_tables_in_from_list_subqry TRUE
_data_access_stats FALSE
_data_access_stats_depth 0
_data_guard_redo_statistics 31
_data_guard_val_redo 65537
_data_link_remote FALSE
_data_transfer_cache_bc_perc_x100 500
_data_warehousing_scan_buffers TRUE
_data_warehousing_scan_flash_buffers FALSE
_data_warehousing_serial_scan TRUE
_database_role PRIMARY
_datafile_cow FALSE
_datafile_create_min_wait_time 0
_datafile_create_wait_time 0
_datafile_open_errors_crash_instance TRUE
_datafile_write_errors_crash_instance TRUE
_datamemory_area_size 0
_datamemory_favor_empty_granules_for_shrink 2
_datapump_bypass_tstz_check FALSE
_datapump_compressbas_buffer_size 0
_datapump_conv_pga_lim 0
_datapump_gather_stats_on_load FALSE
_datapump_hide_cdb_warning FALSE
_datapump_inherit_svcname TRUE
_datapump_metadata_buffer_size 131072
_datapump_net_transfer_size 0
_datapump_tabledata_buffer_size 262144
_db_16k_cache_xmem_size 0
_db_16k_flash_cache_file
_db_16k_flash_cache_size 0
_db_2k_cache_xmem_size 0
_db_2k_flash_cache_file
_db_2k_flash_cache_size 0
_db_32k_cache_xmem_size 0
_db_32k_flash_cache_file
_db_32k_flash_cache_size 0
_db_4k_cache_xmem_size 0
_db_4k_flash_cache_file
_db_4k_flash_cache_size 0
_db_8k_cache_xmem_size 0
_db_8k_flash_cache_file
_db_8k_flash_cache_size 0
_db_active_prewarm_expiration 240
_db_active_prewarm_interval 60
_db_active_prewarm_spare1 0
_db_active_prewarm_spare2 0
_db_aging_cool_count 1
_db_aging_freeze_cr FALSE
_db_aging_hot_criteria 2
_db_aging_stay_count 0
_db_aging_touch_time 3
_db_always_check_system_ts TRUE
_db_block_adjcheck TRUE
_db_block_adjchk_level 0
_db_block_align_direct_read TRUE
_db_block_bad_write_check FALSE
_db_block_buffers 336960
_db_block_cache_history_lru FALSE
_db_block_cache_protect false
_db_block_cache_protect_internal 0
_db_block_check_for_debug FALSE
_db_block_check_objtyp TRUE
_db_block_chunkify_ncmbr FALSE
_db_block_corruption_recovery_threshold 30
_db_block_do_full_mbreads FALSE
_db_block_hash_buckets 1048576
_db_block_hash_latches 8192
_db_block_header_guard_level 0
_db_block_hi_priority_batch_size 0
_db_block_iterations_for_rm 2000
_db_block_known_clean_pct 2
_db_block_lru_latches 36
_db_block_max_cr_dba 6
_db_block_max_scan_pct 40
_db_block_med_priority_batch_size 0
_db_block_numa 1
_db_block_prefetch_fast_longjumps_enabled TRUE
_db_block_prefetch_limit 0
_db_block_prefetch_override 0
_db_block_prefetch_private_cache_enabled TRUE
_db_block_prefetch_quota 10
_db_block_prefetch_skip_reading_enabled TRUE
_db_block_prefetch_wasted_threshold_perc 2
_db_block_scandepth_for_rm 20
_db_block_table_scan_buffer_size 4194304
_db_block_temp_redo FALSE
_db_block_trace_protect FALSE
_db_block_vlm_check FALSE
_db_block_vlm_leak_threshold 4
_db_blocks_per_hash_latch
_db_bt_cache_only_readmostly_obj_on_roi FALSE
_db_buffer_cache_percent 75
_db_cache_advice_hash_latch_multiple 16
_db_cache_advice_max_size_factor 2
_db_cache_advice_sample_factor 4
_db_cache_advice_sanity_check FALSE
_db_cache_advice_size_submultiple 10
_db_cache_block_read_stack_trace 0
_db_cache_block_read_stack_trace_where1 0
_db_cache_block_read_stack_trace_where2 0
_db_cache_block_read_stack_trace_where3 0
_db_cache_crx_check FALSE
_db_cache_max_sz 0
_db_cache_miss_check_les FALSE
_db_cache_mman_latch_check FALSE
_db_cache_pmem_confidence_try 0
_db_cache_pmem_promotion_touch_rate_reset_interval 300
_db_cache_pmem_promotion_touch_rate_threshold_time 30
_db_cache_pmem_touch_rate_compare_per 95
_db_cache_pmemp_len 10000
_db_cache_pre_warm TRUE
_db_cache_process_cr_pin_max 2147483647
_db_cache_read_temp_as_cur_on_standby TRUE
_db_cache_silicon_secured_memory TRUE
_db_cache_wait_debug 0
_db_cache_xmem_promotion_algo_chosen 38
_db_cache_xmem_size 0
_db_change_notification_enable TRUE
_db_check_cell_hints FALSE
_db_disable_temp_encryption FALSE
_db_discard_lost_masterkey FALSE
_db_dump_from_disk_and_efc 0
_db_dw_scan_adaptive_cooling FALSE
_db_dw_scan_max_shadow_count 5
_db_dw_scan_obj_cooling_factor 500
_db_dw_scan_obj_cooling_interval 100
_db_dw_scan_obj_cooling_policy CACHE_SIZE
_db_dw_scan_obj_warming_increment 1000
_db_fast_obj_check FALSE
_db_fast_obj_ckpt TRUE
_db_fast_obj_truncate TRUE
_db_file_direct_io_count 1048576
_db_file_exec_read_count 128
_db_file_format_io_buffers 4
_db_file_noncontig_mblock_read_count 11
_db_file_optimizer_read_count 8
_db_file_secondary_prewarm_read TRUE
_db_flash_cache_disable_write_batchsize 4096
_db_flash_cache_encryption FALSE
_db_flash_cache_force_replenish_limit 8
_db_flash_cache_keep_limit 80
_db_flash_cache_max_latency 400
_db_flash_cache_max_outstanding_writes 32
_db_flash_cache_max_read_retry 10
_db_flash_cache_max_slow_io 3
_db_flash_cache_slow_io_adjustment_interval 3600
_db_flash_cache_write_limit 6
_db_flashback_iobuf_size 1
_db_flashback_log_min_size 16777216
_db_flashback_log_min_total_space 0
_db_flashback_num_iobuf 64
_db_full_caching TRUE
_db_full_db_cache_diff_pct 5
_db_generate_dummy_masterkey FALSE
_db_handles 3200
_db_handles_cached 10
_db_hot_block_tracking FALSE
_db_imoltp_hashidx_force_nonctg 0
_db_index_block_checking TRUE
_db_initial_cachesize_create_mb 256
_db_keep_cache_xmem_size 0
_db_l2_tracing 0
_db_large_dirty_queue 25
_db_link_sources_tracking TRUE
_db_lost_write_checking 2
_db_lost_write_corrupt_block FALSE
_db_lost_write_protect_timer_interval_secs 60
_db_lost_write_tracing FALSE
_db_minimum_auxsize_percent 0
_db_mttr_advice ON
_db_mttr_partitions 0
_db_mttr_sample_factor 64
_db_mttr_sim_target
_db_mttr_sim_trace_size 256
_db_mttr_trace_to_alert FALSE
_db_noarch_disble_optim FALSE
_db_num_evict_waitevents 16384
_db_num_gsm 0
_db_nvm_promotion_deferred_tchcnt 195
_db_obj_cnt_for_file_ckpt 1000000
_db_obj_enable_ksr TRUE
_db_obj_to_file_for_file_ckpt 10000
_db_open_links 0
_db_percent_hot_default 50
_db_percent_hot_keep 0
_db_percent_hot_recycle 0
_db_percpu_create_cachesize 2
_db_pmem_auto_resize_interval 10
_db_pmem_direct_map_size 0
_db_prefetch_histogram_statistics FALSE
_db_recovery_temporal_file_dest
_db_recycle_cache_xmem_size 0
_db_replay_security_config
_db_required_percent_fairshare_usage 10
_db_row_overlap_checking TRUE
_db_shadow_lost_write_protect NOT_SET
_db_todefer_cache_create TRUE
_db_writer_chunk_writes 0
_db_writer_coalesce_area_size 13991936
_db_writer_coalesce_encrypted_buffers TRUE
_db_writer_coalesce_write_limit 131072
_db_writer_flush_imu TRUE
_db_writer_histogram_statistics FALSE
_db_writer_max_writes 0
_db_writer_nomemcopy_coalesce FALSE
_db_writer_verify_writes FALSE
_db_xmem_cache_encryption TRUE
_db_xmem_hot_switch_criteria 195
_dbcomp_maxdump 100
_dbcomp_msg_ver 1
_dbfs_modify_implicit_fetch TRUE
_dbfs_symlink_path_prefix TRUE
_dbg_proc_startup FALSE
_dbg_scan 0
_dblink_internal_gateway FALSE
_dblink_multiple_address_transform FALSE
_dblink_rce_dns_proxy FALSE
_dblink_topology TRUE
_dbms_shared_pool_allow_hot_oso TRUE
_dbms_sql_security_level 1
_dbms_vector_trace FALSE
_dbmsumf$$1x
_dbmsumf$$2x
_dbmsumf$$3x
_dbmsumf$$nn
_dbmsumf$$p
_dbnest_enable NONE
_dbnest_pdb_fs_conf
_dbnest_pdb_fs_type DEFAULT
_dbnest_pdb_network_ip
_dbnest_pdb_scm_conf
_dbnest_pdb_scm_level STRICT1
_dbnest_resource_opts 0
_dbnest_skip_fed_root TRUE
_dbnest_stage_dir
_dbop_enabled 1
_dbopen_breakpoint none
_dbpool_name
_dbreplay_feature_control
_dbreplay_mpk_key
_dbrm_dynamic_threshold 17302504
_dbrm_num_runnable_list 0
_dbrm_quantum
_dbrm_runchk 30000
_dbrm_short_wait_us 300
_dbwr_async_io TRUE
_dbwr_flashlock_shrink_limit 0
_dbwr_nowrite_assert_interval 7200
_dbwr_nwp_assert_interval 1800
_dbwr_scan_interval 300
_dbwr_stall_write_detection_interval 900
_dbwr_tracing 0
_dd_validate_remote_locks TRUE
_dde_flood_control_init TRUE
_ddlapply_enable FALSE
_dead_process_scan_interval 60
_deadlock_diagnostic_level 2
_deadlock_record_to_alert_log TRUE
_deadlock_resolution_incidents_always FALSE
_deadlock_resolution_incidents_enabled TRUE
_deadlock_resolution_level 1
_deadlock_resolution_min_wait_timeout_secs 60
_deadlock_resolution_signal_process_thresh_secs 60
_debug_segment_size 50
_debug_segment_textfile TRUE
_debug_segments_max 20
_default_encrypt_alg 0
_default_ini_trans_index 0
_default_ini_trans_table 0
_default_non_equality_sel_check TRUE
_default_oracle_fs_type ofs
_default_pct_free 0
_default_pdb_filecopy_dop 0
_default_service 1
_defer_eor_orl_arch_for_so TRUE
_defer_log_boundary_ckpt TRUE
_defer_log_count 100
_defer_rcv_during_sw_to_sby FALSE
_defer_rcv_pdb_attach TRUE
_defer_rewrap_controlfile_key_history FALSE
_defer_sga_alloc_chunk_size 1073741824
_defer_sga_enabled FALSE
_defer_sga_min_spsz_at_startup 53687091200
_defer_sga_min_total_defer_segs_sz 107374182400
_defer_sga_test_alloc_intv 0
_defer_while_patching 0
_deferred_constant_folding_mode DEFAULT
_deferred_log_dest_is_valid TRUE
_deferred_seg_in_seed TRUE
_del_qsvc_last_bufsub_drop FALSE
_delay_index_maintain TRUE
_delete_ghost_data FALSE
_deq_execute_reset_time 30
_deq_ht_child_latches 8
_deq_ht_max_elements 100000
_deq_large_txn_size 25000
_deq_log_array_size 10000
_deq_max_fetch_count 10
_deq_maxwait_time 0
_desired_readmem_rate 90
_df_hist_offl_override FALSE
_dg_broker_trace_level
_dg_cf_check_timer 15
_dg_corrupt_redo_log 0
_dgb_dgpdb_appst
_dgpdb_cf_retention 10080
_dgpdb_file_name_convert
_dgpdb_pcf_cf_apply_time 600
_dgpdb_pcf_cf_sync_time 43200
_dgpdb_rc_notify_check_interval 5
_dgpdb_standby_controlfile_name dgpdb_stdby_cf_pdbid_%u_%u_%u.cf
_diag_adl_dyn_alloc TRUE
_diag_adr_auto_purge TRUE
_diag_adr_enabled TRUE
_diag_adr_test_param 0
_diag_adr_trace_dest /u01/app/oracle/diag/rdbms/cdb/CDB/trace
_diag_alert_log_enable_attention_prefix TRUE
_diag_alert_root_annotate FALSE
_diag_arb_before_kill FALSE
_diag_attn_log_enable_fc FALSE
_diag_attn_log_format_error
_diag_attn_log_format_standard
_diag_backward_compat TRUE
_diag_cc_enabled TRUE
_diag_cdb_logging short
_diag_conf_cap_enabled TRUE
_diag_crashdump_level 10
_diag_css_lock_wait_retry_count 100
_diag_css_lock_wait_timeout 5
_diag_daemon TRUE
_diag_dd_global_blockers_dump FALSE
_diag_dde_async_age_limit 300
_diag_dde_async_cputime_limit 300
_diag_dde_async_mode 1
_diag_dde_async_msg_capacity 1024
_diag_dde_async_msgs 50
_diag_dde_async_process_rate 5
_diag_dde_async_runtime_limit 900
_diag_dde_async_slaves 5
_diag_dde_enabled TRUE
_diag_dde_fc_enabled TRUE
_diag_dde_fc_implicit_time 0
_diag_dde_fc_macro_time 0
_diag_dde_inc_proc_delay 1
_diag_deadlock_detection_enabled TRUE
_diag_diagnostics TRUE
_diag_dump_request_debug_level 1
_diag_dump_timeout 30
_diag_enable_startup_events FALSE
_diag_hang_analyze_default_dump_level 0
_diag_hang_analyze_elapsed_time_limit 1800
_diag_hm_rc_enabled TRUE
_diag_hm_tc_enabled FALSE
_diag_kjzcmsg_limit 8388608
_diag_kjzcmsg_send_time_out 600000
_diag_large_packets TRUE
_diag_patch_cap_enabled TRUE
_diag_pdb_control 0
_diag_pdb_purge_target 90
_diag_pdb_purge_threshold 97
_diag_proc_enabled TRUE
_diag_proc_max_time_ms 30000
_diag_proc_stack_capture_type 1
_diag_test_seg_reinc_mode FALSE
_diag_uts_control 0
_diag_verbose_error_on_init 0
_diag_xm_enabled FALSE
_dimension_skip_null TRUE
_direct_io_skip_cur_slot_on_error TRUE
_direct_io_slots 0
_direct_io_via_mapped_pmem TRUE
_direct_io_wslots 0
_direct_path_insert_features 0
_direct_read_decision_statistics_driven TRUE
_directed_diag_cputime_limit 0
_directed_diag_enable TRUE
_directed_diag_runtime_limit 600
_directed_diag_trace_size_limit 104857600
_dirty_appliance_mode FALSE
_disable_12751 FALSE
_disable_12cbigfile FALSE
_disable_active_influx_move FALSE
_disable_actualization_for_grant FALSE
_disable_adaptive_shrunk_aggregation FALSE
_disable_adp_adj_buf_check FALSE
_disable_appliance_check FALSE
_disable_appliance_partnering FALSE
_disable_asm_audit_feat 0
_disable_autotune_gtx FALSE
_disable_block_checking FALSE
_disable_block_corruption_track FALSE
_disable_cdb_view_rc_invalidation FALSE
_disable_cell_optimized_backups FALSE
_disable_con_recurse_queuing TRUE
_disable_cpu_check FALSE
_disable_cross_shard_row_movement FALSE
_disable_cursor_sharing FALSE
_disable_data_block_check_after_decrypt FALSE
_disable_datalayer_sampling FALSE
_disable_dblink_optim TRUE
_disable_def_seg_update 0
_disable_destructive_patch_operation TRUE
_disable_dict_check_pdb_open FALSE
_disable_directory_link_check FALSE
_disable_duplex_link TRUE
_disable_duplicate_service_warning FALSE
_disable_fast_aggregation FALSE
_disable_fast_validate FALSE
_disable_fastopen FALSE
_disable_fba_qrw 0
_disable_fba_wpr 0
_disable_file_locks FALSE
_disable_file_resize_logging FALSE
_disable_flashback_data_archive FALSE
_disable_flashback_recyclebin_opt TRUE
_disable_flashback_wait_callback FALSE
_disable_foreign_scn_adjust FALSE
_disable_function_based_index FALSE
_disable_gvaq_cache FALSE
_disable_hcc_array_insert FALSE
_disable_health_check FALSE
_disable_highres_ticks TRUE
_disable_hybrid_tg FALSE
_disable_ilm_internal FALSE
_disable_image_check FALSE
_disable_implicit_row_movement FALSE
_disable_incremental_checkpoints FALSE
_disable_incremental_recovery_ckpt FALSE
_disable_index_block_prefetching FALSE
_disable_index_pk_using_nonunique FALSE
_disable_inheritpriv_grant_public FALSE
_disable_initial_block_compression FALSE
_disable_instance_params_check FALSE
_disable_interface_checking FALSE
_disable_kcb_flashback_blocknew_opt FALSE
_disable_kcbhxor_osd FALSE
_disable_kcbl_flashback_blocknew_opt FALSE
_disable_kgghshcrc32_osd FALSE
_disable_last_successful_login_time FALSE
_disable_last_successful_login_time_unlimited_iat FALSE
_disable_logging FALSE
_disable_lostwrite_tablespace_alerts FALSE
_disable_mandatory_profile_for_import FALSE
_disable_mandatory_profile_onclone FALSE
_disable_marking_noops FALSE
_disable_metrics_group 0
_disable_modsvc_refresh
_disable_mt_rfs FALSE
_disable_mt_rfs_tracking FALSE
_disable_multiple_block_sizes FALSE
_disable_odm FALSE
_disable_oradebug_commands restricted
_disable_orphan_pdb_recovery FALSE
_disable_os_time_page FALSE
_disable_parallel_conventional_load FALSE
_disable_pdb_space_check FALSE
_disable_primary_bitmap_switch FALSE
_disable_privilege_cache_in_auth_table FALSE
_disable_ptl_replay FALSE
_disable_pushmap FALSE
_disable_read_only_open_dict_check FALSE
_disable_rebalance_space_check FALSE
_disable_recovery_read_skip FALSE
_disable_restricted_rac_rolling 0
_disable_rolling_patch 0
_disable_row_movement_auto_rollback FALSE
_disable_sample_io_optim FALSE
_disable_savepoint_reset FALSE
_disable_secure_sga_check FALSE
_disable_selftune_checkpointing FALSE
_disable_sensitive_internal FALSE
_disable_sessionless_transaction FALSE
_disable_sga_filedel FALSE
_disable_storage_type FALSE
_disable_streams_diagnostics 0
_disable_streams_pool_auto_tuning FALSE
_disable_sun_rsm TRUE
_disable_sv_shared_mode FALSE
_disable_system_state 4294967294
_disable_system_state_wait_samples FALSE
_disable_system_tablespaces_enc_enforcement FALSE
_disable_temp_tablespace_alerts FALSE
_disable_thread_internal_disable FALSE
_disable_txn_alert 0
_disable_uix_pred_push FALSE
_disable_undo_tablespace_alerts FALSE
_disable_wait_state
_disallow_osu_edition_obj_in_pdb TRUE
_discard_cmn_ddl_in_pdb_err FALSE
_discrete_transactions_enabled FALSE
_disk_sector_size_override FALSE
_diskmon_pipe_name
_disksize_binary_search FALSE
_dispatcher_listen_on_vip FALSE
_dispatcher_rate_scale
_dispatcher_rate_ttl
_distinct_agg_optimization_gsets CHOOSE
_distinct_view_unnesting FALSE
_distributed_recovery_connection_hold_time 200
_disttxn_for_queries TRUE
_dixinv_flags 0
_dlm_cache_warmup_slaves 2
_dlm_stats_collect 1
_dlm_stats_collect_du_limit 3000
_dlm_stats_collect_mode 14
_dlm_stats_collect_slot_interval 60
_dlmtrace
_dm_dmf_details_compatibility 12.1.0
_dm_enable_legacy_dmf_output_types FALSE
_dm_inmemory_threshold 1000000
_dm_max_chunk_size 2000
_dm_max_shared_pool_pct 5
_dml_batch_error_limit 0
_dml_frequency_tracking FALSE
_dml_frequency_tracking_advance TRUE
_dml_frequency_tracking_slot_time 15
_dml_frequency_tracking_slots 4
_dml_monitoring_enabled TRUE
_dmm_auto_max_features 500
_dmm_blas_library
_dmm_cnt_arr_size_threshold 500000
_dmm_details_filter_weight 1
_dmm_disable_onnx 0
_dmm_force_treetop_merge 0
_dmm_inc_cholesky_rows 50000
_dmm_ipp_cutoff 0
_dmm_kmean_dense_threshold 500
_dmm_max_memory_size 1000000
_dmm_memory_size 64000000
_dmm_nobin_threshold 200
_dmm_onnx_cache_minmodsz 10485760
_dmm_onnx_cache_timeout 120000
_dmm_onnx_large_model_size 419430400
_dmm_onnx_max_image_size 20971520
_dmm_pga_load_threshold 3
_dmm_reduction_rate 4
_dmm_sample_lower_threshold 10000
_dmm_sample_upper_threshold 500000
_dmm_ser_test 0
_dmm_ts_lapack 1
_dmm_xgboost_max_memory 1000000000
_dmsqr_qr_chunk_rows 10000
_dnfs_rdma_enable rman
_dnfs_rdma_max 1048576
_dnfs_rdma_min 8192
_domain_index_batch_size 2000
_domain_index_dml_batch_size 200
_dp_force_length_semantics NONE
_dra_bmr_number_threshold 1000
_dra_bmr_percent_threshold 10
_dra_enable_offline_dictionary FALSE
_drm_parallel_freeze TRUE
_drop_flashback_logical_operations_enq FALSE
_drop_stat_segment 0
_drop_table_granule 256
_drop_table_optimization_enabled TRUE
_drop_tablespace_objects 0
_ds_enable_auto_txn FALSE
_ds_enable_view_sampling TRUE
_ds_iocount_iosize 6553664
_ds_parse_model 2
_ds_progressive_initial_samples 2
_ds_progressive_no_matches_min_sample_size 50
_ds_sampling_method PROGRESSIVE
_ds_xt_split_count 1
_dsc_feature_level 0
_dskm_health_check_cnt 20
_dskm_single_instance FALSE
_dss_cache_flush FALSE
_dss_cache_flush_threshold 1
_dtree_area_size 131072
_dtree_binning_enabled TRUE
_dtree_max_surrogates 1
_dtree_pruning_enabled TRUE
_duality_view_enable_bulk_load FALSE
_duality_view_etag_required FALSE
_dummy_instance FALSE
_dump_10261_level 0
_dump_common_subexpressions FALSE
_dump_connect_by_loop_data FALSE
_dump_cursor_heap_sizes FALSE
_dump_diag_audrec_fail_tab FALSE
_dump_interval_limit 120
_dump_max_limit 5
_dump_qbc_tree 0
_dump_rcvr_ipc TRUE
_dump_scheduler_inmemory_trace_on_error TRUE
_dump_scheduler_inmemory_trace_on_timeout TRUE
_dump_scn_increment_stack
_dump_system_state_scope local
_dump_trace_scope global
_duplicate_database_key_to_omts TRUE
_duplicated_table_complete_refresh_percent 50
_dupt_noupdate 0
_dynamic_hash_bucket_array TRUE
_dynamic_processes_force_timeout 6
_dynamic_processes_max_oom_timeout 300
_dynamic_processes_wait_timeout 100
_dynamic_rls_policies TRUE
_dynamic_sequence_cache TRUE
_dynamic_sequence_cache_max 1000000
_dynamic_sequence_cache_scale 10
_dynamic_sessions_force_timeout 30
_dynamic_sessions_inc_count 1000
_dynamic_sessions_max_oom_timeout 300
_dynamic_sessions_min_force_timeout 5
_dynamic_sessions_wait_timeout 100
_dynamic_share_range_factor 2
_dynamic_stats_threshold 30
_early_flush_delta 0
_edition_cleanup FALSE
_edition_enable_oracle_users
_eighteenth_spare_parameter
_eighteenth_spare_pdb_parameter
_eighth_spare_parameter
_eighth_spare_pdb_parameter
_eightieth_spare_parameter
_eighty-eighth_spare_parameter
_eighty-fifth_spare_parameter
_eighty-first_spare_parameter
_eighty-fourth_spare_parameter
_eighty-ninth_spare_parameter
_eighty-second_spare_parameter
_eighty-seventh_spare_parameter
_eighty-sixth_spare_parameter
_eighty-third_spare_parameter
_elastic_pool_leader FALSE
_elastic_pool_member FALSE
_eleventh_spare_parameter
_eleventh_spare_pdb_parameter
_eliminate_common_subexpr TRUE
_emon_max_active_connections 256
_emon_outbound_connect_timeout 7200000
_emon_pool_inc 4
_emon_pool_max 16
_emon_pool_min 4
_emon_regular_ntfn_slaves 4
_emon_send_timeout 7200000
_emx_control 0
_emx_max_sessions 128
_emx_session_timeout 3600
_ena_storage_lmt DEFAULT
_enable_12g_bft TRUE
_enable_942_table_name TRUE
_enable_Front_End_View_Optimization 1
_enable_NUMA_interleave TRUE
_enable_NUMA_optimization FALSE
_enable_NUMA_support FALSE
_enable_ascending_scn_in_online_ddl TRUE
_enable_asyncvio FALSE
_enable_auto_check_constraints_for_dst_upgrade TRUE
_enable_automatic_maintenance 1
_enable_automatic_sqltune TRUE
_enable_block_level_transaction_recovery TRUE
_enable_buffer_header_history TRUE
_enable_bug_29838374 0
_enable_capture_select FALSE
_enable_cdb_all_sync FALSE
_enable_cdb_upgrade_capture FALSE
_enable_check_truncate TRUE
_enable_columnar_cache 1
_enable_concurrent_refresh TRUE
_enable_containers_subquery FALSE
_enable_create_protected_profile FALSE
_enable_cscn_caching FALSE
_enable_dbwr_auto_tracing 1
_enable_dbwr_parallel_invalidations TRUE
_enable_ddl_wait_lock TRUE
_enable_default_affinity 0
_enable_default_temp_threshold TRUE
_enable_default_undo_threshold TRUE
_enable_dml_lock_escalation TRUE
_enable_drop_clone FALSE
_enable_dynamic_processes FALSE
_enable_dynamic_sessions FALSE
_enable_editions_for_users FALSE
_enable_event_ports TRUE
_enable_exchange_validation_using_check TRUE
_enable_fast_file_zero TRUE
_enable_fast_ref_after_mv_tbs FALSE
_enable_flash_logging TRUE
_enable_fsdirect_odmlib TRUE
_enable_fsdirect_pin TRUE
_enable_fsdirect_rac FALSE
_enable_gsm_listener_networks TRUE
_enable_guid_endpoint_service TRUE
_enable_hash_overflow FALSE
_enable_heatmap_internal FALSE
_enable_http_digest_generation TRUE
_enable_hugetlbfs_dynamic_sga FALSE
_enable_hwm_sync TRUE
_enable_iee_stats TRUE
_enable_ignorable_error_capture FALSE
_enable_ilm_flush_stats TRUE
_enable_ilm_testflush_stats FALSE
_enable_increase_lms_process TRUE
_enable_ios_spm FALSE
_enable_iou
_enable_json_uga_save_restore FALSE
_enable_kernel_io_outliers FALSE
_enable_kqf_purge TRUE
_enable_list_io FALSE
_enable_load_from_clone TRUE
_enable_load_using_app_version TRUE
_enable_lock_down_on_mv_internal_ddls TRUE
_enable_log_memory_protection_key TRUE
_enable_memory_protection_keys TRUE
_enable_meta_snap FALSE
_enable_metrics_allpdb TRUE
_enable_metrics_pdb FALSE
_enable_midtier_affinity TRUE
_enable_minscn_cr TRUE
_enable_module_match TRUE
_enable_multiple_fgprepares FALSE
_enable_nativenet_tcpip FALSE
_enable_noncdb_capture FALSE
_enable_nvm_dispatcher 0
_enable_obj_queues TRUE
_enable_offloaded_writes FALSE
_enable_online_index_without_s_locking TRUE
_enable_os_cpu_rm FALSE
_enable_parallel_dml FALSE
_enable_partial_sync FALSE
_enable_pdb_close_abort TRUE
_enable_pdb_close_noarchivelog FALSE
_enable_pdb_common_ddl FALSE
_enable_pdb_isolation FALSE
_enable_pdb_process_limit TRUE
_enable_pdb_skiplist_recovery TRUE
_enable_pdb_skiplist_redogen TRUE
_enable_pdc FALSE
_enable_per_container_acl FALSE
_enable_perpdb_suplog FALSE
_enable_plcmnt_pol_usage FALSE
_enable_pluggable_database TRUE
_enable_pmem_direct_cache TRUE
_enable_pmem_exchange TRUE
_enable_pmem_prefetch FALSE
_enable_pmo_outside_begin_end TRUE
_enable_protected_audit_policy FALSE
_enable_proxy_distr_txn TRUE
_enable_ptime_update_for_sys FALSE
_enable_query_rewrite_on_remote_objs TRUE
_enable_redo_global_post FALSE
_enable_refresh_schedule TRUE
_enable_rejection_cache TRUE
_enable_reliable_latch_waits TRUE
_enable_rename_user FALSE
_enable_replay_upgrade_diag TRUE
_enable_rlb TRUE
_enable_row_shipping TRUE
_enable_schema_synonyms FALSE
_enable_scn_wait_interface TRUE
_enable_secure_sub_role FALSE
_enable_securefile_flashback_opt TRUE
_enable_sensitive_trace FALSE
_enable_separable_transactions FALSE
_enable_session_heaps_in_mga TRUE
_enable_shared_multitarget_dblink 0
_enable_shared_pool_durations TRUE
_enable_shared_server_sizing TRUE
_enable_shared_server_sizing_slope FALSE
_enable_shared_server_vector_io FALSE
_enable_single_dgprepare FALSE
_enable_space_preallocation 3
_enable_spacebg TRUE
_enable_streams_pool_subpools FALSE
_enable_synonym_repoint FALSE
_enable_sysaux_gdr FALSE
_enable_sysaux_metadata_clone FALSE
_enable_system_app 2
_enable_tablespace_alerts TRUE
_enable_tcpinfo_statistics 238
_enable_tenant_id_check FALSE
_enable_tenant_id_transfer FALSE
_enable_thr_kill TRUE
_enable_token_verification FALSE
_enable_trans_hnsw_vector_scan TRUE
_enable_type_dep_selectivity TRUE
_enable_unified_memory FALSE
_enable_user_pdb_close_abort FALSE
_enable_verbose_gdr FALSE
_enable_view_pdb TRUE
_endprot_chunk_comment chk 10235 dflt
_endprot_heap_comment hp 10235 dflt
_endprot_stack_segments FALSE
_endprot_subheaps TRUE
_enforce_lockdown_hardening FALSE
_enforce_minimum_password_rollover_time TRUE
_enforce_set_container_hardening
_enforce_walletdir_readpriv TRUE
_enqueue_deadlock_detect_all_global_locks FALSE
_enqueue_deadlock_scan_secs 0
_enqueue_deadlock_time_sec 5
_enqueue_debug_multi_instance FALSE
_enqueue_hash 1043
_enqueue_hash_chain_latches 4
_enqueue_locks 6060
_enqueue_paranoia_mode_enabled FALSE
_enqueue_resources 2436
_enqueue_scan_interval 0
_enqueue_sync_retry_attempts 15
_enqueue_sync_sim_mem_error FALSE
_enqueue_wall_clock_time FALSE
_error_row_predicate_evaluation AUTO
_event_port_opts
_evt_system_event_propagation TRUE
_exa_internal_parameters
_exa_pmemlog_threshold_usec 100
_exadata_feature_on TRUE
_exclude_seed_cdb_view TRUE
_expand_aggregates TRUE
_explain_rewrite_mode FALSE
_export_data_parquet_temp_dir DATA_PUMP_DIR
_expression_tracking_elem_per_bucket 30
_expression_tracking_latch_count 16
_extended_pruning_enabled TRUE
_external_scn_activity_tracking TRUE
_external_scn_logging_threshold_seconds 86400
_external_scn_rejection_delta_threshold_minutes 0
_external_scn_rejection_threshold_hours 24
_external_table_hive_partition_restricted TRUE
_external_table_smart_scan HADOOP_ONLY
_extra_lmn_enabled TRUE
_failover_svrcsum FALSE
_fair_remote_cvt FALSE
_fairness_threshold 2
_fast_connection_version 1
_fast_cr_clone TRUE
_fast_cursor_reexecute FALSE
_fast_dual_enabled TRUE
_fast_full_scan_enabled TRUE
_fast_index_maintenance TRUE
_fast_psby_conversion TRUE
_fastpin_enable 1
_fatalprocess_redo_dump_time_limit 0
_fb_log_max_rereads 100
_fb_recovery_slave_count 0
_fbda_adv_gbl_bscn_bcast_interval 0
_fbda_bscn_lag_warning 600
_fbda_busy_percentage 0
_fbda_debug_assert 0
_fbda_debug_mode 0
_fbda_global_bscn_lag 0
_fbda_inline_percentage 0
_fbda_limit_warning_frequency 21600
_fbda_rac_inactive_limit 0
_fbda_tcrv_cleanup_lag 3600
_federation_max_root_clones 4000
_federation_script FALSE
_ffs_in_range_scan_threshold 50
_fg_fast_sync_slack_usecs 1
_fg_fast_sync_sleep_target_pct 50
_fg_fast_sync_sleep_usecs 0
_fg_fast_sync_spin_usecs 100
_fg_iorm_slaves 1
_fg_log_checksum TRUE
_fg_sync_sleep_usecs 0
_fic_algorithm_set automatic
_fic_area_size 131072
_fic_min_bmsize 1024
_fifteenth_spare_parameter
_fifteenth_spare_pdb_parameter
_fifth_spare_parameter
_fifth_spare_pdb_parameter
_fiftieth_spare_parameter
_fiftieth_spare_pdb_parameter
_fifty-eighth_spare_parameter
_fifty-eighth_spare_pdb_parameter
_fifty-fifth_spare_parameter
_fifty-fifth_spare_pdb_parameter
_fifty-first_spare_parameter
_fifty-first_spare_pdb_parameter
_fifty-fourth_spare_parameter
_fifty-fourth_spare_pdb_parameter
_fifty-ninth_spare_parameter
_fifty-ninth_spare_pdb_parameter
_fifty-second_spare_parameter
_fifty-second_spare_pdb_parameter
_fifty-seventh_spare_parameter
_fifty-seventh_spare_pdb_parameter
_fifty-sixth_spare_parameter
_fifty-sixth_spare_pdb_parameter
_fifty-third_spare_parameter
_fifty-third_spare_pdb_parameter
_file_offline_sync_timeout 900
_file_set_enqueue_timeout 1200
_file_size_increase_increment 67108864
_filemap_dir
_filter_roaring_bitmap TRUE
_first_k_rows_dynamic_proration TRUE
_first_spare_parameter
_first_spare_pdb_parameter
_fix_control
_fix_control_1
_fix_control_2
_fix_control_3
_fix_control_4
_fix_control_5
_fix_fuzzy_scn FALSE
_fixup_all_apps FALSE
_fixup_app_pdb_status_in_root
_fixup_cdb_apps FALSE
_flashback_11_1_block_new_opt FALSE
_flashback_allow_noarchivelog FALSE
_flashback_archiver_partition_size 0
_flashback_barrier_interval 1800
_flashback_copy_latches 10
_flashback_database_test_only FALSE
_flashback_delete_chunk_MB 128
_flashback_dynamic_enable TRUE
_flashback_dynamic_enable_failure 0
_flashback_enable_ra TRUE
_flashback_format_chunk_mb 4
_flashback_format_chunk_mb_dwrite 16
_flashback_fuzzy_barrier TRUE
_flashback_generation_buffer_size 16777216
_flashback_hint_barrier_percent 20
_flashback_log_io_error_behavior 0
_flashback_log_min_size 100
_flashback_log_rac_balance_factor 10
_flashback_log_size 1000
_flashback_logfile_enqueue_timeout 600
_flashback_marker_cache_enabled TRUE
_flashback_marker_cache_size 328
_flashback_marker_for_every_grp FALSE
_flashback_max_log_size 0
_flashback_max_n_log_per_thread 2048
_flashback_max_standby_sync_span 300
_flashback_n_log_per_thread 128
_flashback_pdb_thread_filter_disable FALSE
_flashback_prepare_log TRUE
_flashback_reclaim_monitor_window 7
_flashback_reclaim_speed_up FALSE
_flashback_size_based_on_redo TRUE
_flashback_standby_barrier_interval 1
_flashback_standby_check_barrier_MIRA 20
_flashback_standby_check_minpfh_MIRA 15
_flashback_stby_support_mira TRUE
_flashback_validate_controlfile FALSE
_flashback_verbose_info FALSE
_flashback_write_max_loop_limit 10
_flush_ilm_stats 0
_flush_log_buffer_force FALSE
_flush_log_buffer_timeout 0
_flush_plan_in_awr_sql 0
_flush_redo_to_standby 0
_flush_undo_after_tx_recovery TRUE
_fob_dgaalloc TRUE
_fob_ospshare TRUE
_force_arch_compress 0
_force_backupset_zt_decryption FALSE
_force_cloud_on FALSE
_force_comp_validation_rule_failure OFF
_force_containers_subquery FALSE
_force_create_cloud_credential FALSE
_force_datefold_trunc FALSE
_force_dax_io_err 0
_force_hash_join_spill FALSE
_force_hsc_compress FALSE
_force_java_pool_zero FALSE
_force_job_creator_as_owner FALSE
_force_level0_for_local_create_df FALSE
_force_local_temp FALSE
_force_logging_in_upgrade TRUE
_force_move_pdb_keys_from_root FALSE
_force_no_capture FALSE
_force_oltp_compress FALSE
_force_oltp_update_opt TRUE
_force_partial_compress FALSE
_force_pmem_direct_mapped_cache_scan TRUE
_force_prvtreslv_hostpattern
_force_result_cache_data_share TRUE
_force_rewrite_enable FALSE
_force_slave_mapping_intra_part_loads FALSE
_force_standard_compile FALSE
_force_sys_compress TRUE
_force_temp_space_cleanup TRUE
_force_temptables_for_gsets FALSE
_force_tmp_segment_loads FALSE
_forced_endian_type UNKNOWN
_forceopen_bind_undotbs FALSE
_foreground_idle_check_timeout 30
_fortieth_spare_parameter
_fortieth_spare_pdb_parameter
_forty-eighth_spare_parameter
_forty-eighth_spare_pdb_parameter
_forty-fifth_spare_parameter
_forty-fifth_spare_pdb_parameter
_forty-first_spare_parameter
_forty-first_spare_pdb_parameter
_forty-fourth_spare_parameter
_forty-fourth_spare_pdb_parameter
_forty-ninth_spare_parameter
_forty-ninth_spare_pdb_parameter
_forty-second_spare_parameter
_forty-second_spare_pdb_parameter
_forty-seventh_spare_parameter
_forty-seventh_spare_pdb_parameter
_forty-sixth_spare_parameter
_forty-sixth_spare_pdb_parameter
_forty-third_spare_parameter
_forty-third_spare_pdb_parameter
_forwarded_2pc_threshold 10
_fourteenth_spare_parameter
_fourteenth_spare_pdb_parameter
_fourth_spare_parameter
_fourth_spare_pdb_parameter
_frame_cache_time 0
_freeze_kgh_timestamp FALSE
_fsdirect_fast_file_create TRUE
_full_diag_on_rim FALSE
_full_pwise_join_enabled TRUE
_fusion_security TRUE
_gas_partition_size 0
_gby_hash_aggregation_enabled TRUE
_gby_onekey_enabled TRUE
_gby_vector_aggregation_enabled TRUE
_gc_affinity_locking TRUE
_gc_affinity_locks TRUE
_gc_affinity_ratio 50
_gc_anti_lock_ratio 66
_gc_async_send TRUE
_gc_bg_merge TRUE
_gc_blocking_pins FALSE
_gc_buckets_per_latch 0
_gc_bypass_readers TRUE
_gc_check_bscn TRUE
_gc_coalesce_recovery_reads TRUE
_gc_cr_server_read_wait TRUE
_gc_defer_ping_index_only TRUE
_gc_defer_time 0
_gc_delay_ping TRUE
_gc_disable_cell_populate FALSE
_gc_disable_s_lock_brr_ping_check TRUE
_gc_down_convert_after_keep TRUE
_gc_down_convert_after_write TRUE
_gc_drm_windows 8
_gc_dump_remote_lock TRUE
_gc_element_percent 105
_gc_enable_cr_bypass TRUE
_gc_fast_index_split_timeout 100
_gc_fast_index_split_wait 0
_gc_fg_merge TRUE
_gc_fg_rollback TRUE
_gc_fg_spin_time 0
_gc_first_dirty_merge TRUE
_gc_first_dirty_pi_merge_switch_current TRUE
_gc_flush_during_affinity TRUE
_gc_fusion_compression 1024
_gc_global_checkpoint_scn TRUE
_gc_global_lru AUTO
_gc_global_lru_touch_count 5
_gc_global_lru_touch_time 60
_gc_integrity_checks 1
_gc_interconnect_checksum FALSE
_gc_interrupt_wait_time 1
_gc_keep_recovery_buffers TRUE
_gc_keep_undo_recovery_buffers TRUE
_gc_latches 32
_gc_lease_time 10000
_gc_log_flush TRUE
_gc_max_downcvt 4096
_gc_max_reg_sz 274877906944
_gc_msgq_buffers 0
_gc_no_fairness_for_clones TRUE
_gc_numa_lock_elements FALSE
_gc_object_queue_max_length 0
_gc_override_force_cr TRUE
_gc_partial_cleanout TRUE
_gc_persistent_read_mostly TRUE
_gc_policy_ckpt_minimum 50
_gc_policy_minimum 15000
_gc_policy_rm_dirty_percent 1
_gc_policy_time 20
_gc_rdma_checkpoint_check TRUE
_gc_rdma_connections 8000
_gc_read_mostly_flush_check TRUE
_gc_read_mostly_locking TRUE
_gc_sanity_check_cr_buffers FALSE
_gc_save_cleanout FALSE
_gc_serve_from_flash_cache FALSE
_gc_skip_undo_disk_read TRUE
_gc_spin_time 32
_gc_statistics TRUE
_gc_temp_affinity FALSE
_gc_timestamps 0
_gc_trace_blocking_pins FALSE
_gc_trace_freelist_empty FALSE
_gc_transfer_ratio 75
_gc_try_to_skip_imc_flush TRUE
_gc_undo_affinity TRUE
_gc_undo_header_rdma_read TRUE
_gc_undo_rdma_read FALSE
_gc_vector_read TRUE
_gcr_change_cached_types TRUE
_gcr_ckptmon_stall_time 900
_gcr_ckptmon_trace_time 0
_gcr_cpu_consumer_dump_level 0
_gcr_cpu_min_free 10
_gcr_cpu_min_hard_limit 0
_gcr_css_group_large
_gcr_css_group_query_boost
_gcr_css_group_try_lock_delay
_gcr_css_group_update2_interval
_gcr_css_group_update_interval
_gcr_css_use_2group_lock TRUE
_gcr_disabled_actions
_gcr_disabled_metrics
_gcr_dump_cpu_consumers FALSE
_gcr_enable_async_helpers TRUE
_gcr_enable_high_cpu_kill FALSE
_gcr_enable_high_cpu_rm TRUE
_gcr_enable_high_cpu_rt TRUE
_gcr_enable_high_memory_kill FALSE
_gcr_enable_kill_inst_diags FALSE
_gcr_enable_ktfbue_gather_stats TRUE
_gcr_enable_new_drm_check TRUE
_gcr_enable_pdb_abort FALSE
_gcr_enable_statistical_cpu_check TRUE
_gcr_ges_cachedres_mult 20
_gcr_ges_longchain_mult 5
_gcr_ges_res_cache_percent_threshold 40
_gcr_high_cpu_threshold 10
_gcr_high_cpwt_threshold 30
_gcr_high_fbwt_threshold 300
_gcr_high_hashlist_latch_nowait_misses 10000
_gcr_high_hashlist_latch_wait_misses 10000
_gcr_high_lfsci_threshold 1800
_gcr_high_memory_threshold 10
_gcr_inst_termination_action auto
_gcr_max_rt_procs
_gcr_max_used_swap 75
_gcr_mem_min_free 10
_gcr_min_cache_reuse 50
_gcr_min_free_memory_hard_limit 1073741824
_gcr_smf FALSE
_gcr_terminate_on_swap FALSE
_gcr_tick
_gcr_use_css TRUE
_gcs_check_closed_lock 0
_gcs_cluster_flash_cache_mode 0
_gcs_cluster_flash_cache_persistency FALSE
_gcs_cr_master_ping_remote TRUE
_gcs_crslave_check_time 10
_gcs_crslave_longq_cnt 2000
_gcs_crslave_longq_us 1000
_gcs_current_rdma 1
_gcs_current_rdma_grant_global TRUE
_gcs_disable_imc_preallocation FALSE
_gcs_disable_remote_handles FALSE
_gcs_disable_skip_close_remastering FALSE
_gcs_dynamic_sga FALSE
_gcs_dynamic_sga_preference 0
_gcs_dynamic_slaves TRUE
_gcs_enable_private_iterator TRUE
_gcs_fast_reconfig TRUE
_gcs_flash_cache_mode 0
_gcs_freelists_alloc_percent 0
_gcs_integrity_checks 1
_gcs_kjbdump_threshold 60
_gcs_latches 128
_gcs_lsr_frequency 60
_gcs_max_antilocks_unmount_inst 10000
_gcs_min_cr_slaves 0
_gcs_min_slaves 0
_gcs_partial_open_mode 5
_gcs_pkey_history 16384
_gcs_process_in_recovery TRUE
_gcs_recoverable_asserts 0
_gcs_res_freelists 1
_gcs_res_hash_buckets
_gcs_res_per_bucket 4
_gcs_reserved_resources 64
_gcs_reserved_shadows 400
_gcs_resources 0
_gcs_shadow_locks 0
_gcs_spin_check_instance_threshold 60
_gcs_spin_check_threshold 4096
_gcs_spin_check_time_interval 300
_gcs_testing 0
_gcs_trace_bucket FALSE
_gcs_trace_bucket_size LMS:1048576-RMV:1048576-CRV:1048576-DBW:524288
_gcs_track_reliable_block_sends FALSE
_gcs_verify_antilock FALSE
_gdr_clear_active_only FALSE
_gdr_clear_inactive_only FALSE
_gdr_control_flags 0
_gds_allow_nullkey 0
_gds_chunk_num 0
_gds_lddlid 0
_gds_max_chunk_num 0
_gds_shardgroup_id 0
_generalized_pruning_enabled TRUE
_ges_aggr_cache_clnup_intvl 25
_ges_bidirectional_chaining 0
_ges_dd_debug 1
_ges_debug_acks FALSE
_ges_default_lmds *
_ges_designated_master TRUE
_ges_diagnostics TRUE
_ges_diagnostics_asm_dump_level 11
_ges_direct_free FALSE
_ges_direct_free_res_type
_ges_dump_open_locks FALSE
_ges_fggl TRUE
_ges_freeable_res_chunk_free FALSE
_ges_freeable_res_chunk_free_interval 180
_ges_gather_res_reuse_stats TRUE
_ges_hash_groups *
_ges_health_check 0
_ges_lmd_mapping *
_ges_max_avg_hash_chainlen 6
_ges_max_hash_resizes 0
_ges_mseq_demo 0
_ges_nres_divide 0
_ges_num_aggr_cache_clnup 5
_ges_num_blockers_to_kill 1
_ges_optimizations 7
_ges_resource_memory_opt 36
_ges_server_processes 1
_ges_vbfreelists 0
_global_hang_analysis_interval_secs 5
_globaldict_analyzer_pct 100
_globaldict_chain_limit 32
_globaldict_check 0
_globaldict_chunk_minalloc FALSE
_globaldict_dbg 0
_globaldict_enable 2
_globaldict_max_gdsize 1073741824
_globaldict_reprobe_limit 1
_globaldict_use_ndv TRUE
_globalindex_pnum_filter_enabled TRUE
_grant_read_instead_of_select FALSE
_grant_secure_role FALSE
_grant_unlimited_tablespace_role FALSE
_granularity_last_successful_login_time 0
_group_leader FALSE
_group_membership_bucket_batch_size 8
_group_membership_bucket_scan_timeout 5
_group_membership_entries_per_bucket 100
_groupby_nopushdown_cut_ratio 3
_groupby_orderby_combine 5000
_gs_anti_semi_join_allowed TRUE
_gsm
_gsm_config_vers 0
_gsm_cpu_thresh 75
_gsm_drv_interval 30
_gsm_local_users FALSE
_gsm_max_instances_per_db 8
_gsm_max_num_regions 10
_gsm_pool_size 134217728
_gsm_region_list
_gsm_srlat_thresh 20
_gsm_srvctl_diag_time 0
_gsm_srvctl_timeout 0
_gsm_svcrgnmax 100
_gsm_thresh_respct 50
_gsm_thresh_zone 10
_guid_dblink_data_share TRUE
_gwm_autoons_ha_subscription
_gwm_autoons_rlb_subscription
_gwm_database_flags
_gwm_db_unique_name
_gwm_disable_ra FALSE
_gwm_enable_ioft FALSE
_gwm_force_sync_duptab FALSE
_gwm_int_dbnum 0
_gwm_lagtype
_gwm_max_start_catddlid 0
_gwm_spare1
_gwm_spare2 0
_gwm_spare3 0
_gwm_sr_ddlsync_enabled TRUE
_gwm_sys_ddl 0
_gwm_use_srvctl 0
_gws_cache_version 0
_gws_catalog_wallet 0
_gws_deployed 0
_gws_directory_sharding 0
_gws_encddl 0
_gws_sharding_method 0
_hang_aggressive_cloud_mode_enabled FALSE
_hang_allow_resolution_on_single_nonrac DBRM
_hang_analysis_num_call_stacks 3
_hang_analyze_dump_session_summary FALSE
_hang_analyze_elapsed_time_limit 1800
_hang_analyze_oradebug_time_limit 900
_hang_analyze_session_summary_interval 60
_hang_appl_issue_session_threshold 0
_hang_application_hang_resolution_enabled FALSE
_hang_asm_hang_resolution_enabled FALSE
_hang_base_file_count 5
_hang_base_file_space_limit 100000000
_hang_blocked_session_percent_threshold 20
_hang_bool_spare1 TRUE
_hang_bool_spare2 TRUE
_hang_bool_spare3 TRUE
_hang_bool_spare4 TRUE
_hang_cpu_hung_thresh_sec 120
_hang_cross_boundary_hang_detection_enabled TRUE
_hang_cross_boundary_ssd_flood_control_interval 300
_hang_cross_cluster_hang_detection_enabled TRUE
_hang_deadlock_resolution_enabled TRUE
_hang_delay_lsr_hang_resolution_enabled TRUE
_hang_delay_resolution_for_libcache TRUE
_hang_detection_enabled TRUE
_hang_enable_processstate FALSE
_hang_fast_track_critical_database_processes_enabl TRUE
ed
_hang_fast_track_progressing_sessions TRUE
_hang_fast_tracked_hang_verification_interval 10
_hang_fb_high_wait_count_percentage 30
_hang_ft_min_degrading_samples_percent_threshold 60
_hang_hang_analyze_output_hang_chains TRUE
_hang_hang_blocked_session_delta_percent_threshold 20
_hang_hiload_promoted_ignored_hang_count 2
_hang_hiprior_session_attribute_list
_hang_hs_hang_metrics_enabled TRUE
_hang_hung_session_ewarn_percent 34
_hang_ignore_hngmtrc_interval 150
_hang_ignored_hang_count 1
_hang_ignored_hangs_interval 300
_hang_int_spare1 0
_hang_int_spare2 0
_hang_int_spare3 0
_hang_int_spare4 0
_hang_intersecting_chains_scanning_enabled TRUE
_hang_log_high_load_to_alert FALSE
_hang_log_important_hangs_to_alert TRUE
_hang_log_io_hung_sessions_to_alert FALSE
_hang_log_verified_hangs_to_alert FALSE
_hang_low_wait_time_cutoff 6
_hang_lsr_trigger_enabled TRUE
_hang_lws_file_count 5
_hang_lws_file_space_limit 100000000
_hang_mark_some_idle_waits_terminal FALSE
_hang_max_instance_allow_node_eviction 1
_hang_max_local_db_clients_allowed 0
_hang_max_session_hang_time 96
_hang_metrics_older_bitmap_threshold 25
_hang_metrics_recent_bitmap_threshold 50
_hang_monitor_archiving_related_hang_interval 300
_hang_msg_checksum_enabled TRUE
_hang_nested_wait_handling_enabled TRUE
_hang_parsing_hangs_resolution_interval 0
_hang_prog_ft_critical_db_proc_verification_interv 900
al
_hang_promote_process_termination_interval 70
_hang_px_resolution_on_asm_enabled TRUE
_hang_resolution_allow_archiving_issue_termination TRUE
_hang_resolution_confidence_promotion FALSE
_hang_resolution_global_hang_confidence_promotion FALSE
_hang_resolution_partial_hangs_on_asm_enabled TRUE
_hang_resolution_partial_hangs_on_db_enabled TRUE
_hang_resolution_percent_hung_sessions_threshold 300
_hang_resolution_percent_hung_sessions_threshold2 5000
_hang_resolution_policy HIGH
_hang_resolution_promote_process_termination TRUE
_hang_resolution_scope INSTANCE
_hang_root_ha_phase_trigger_time 300
_hang_running_in_lrg FALSE
_hang_sess_enq_wait_blocked_session_threshold 5
_hang_sess_enq_wait_resltn_trig_time 0
_hang_session_scan_update_hb_interval 6000
_hang_short_stacks_output_enabled TRUE
_hang_signature_list_match_output_frequency 10
_hang_singleton_detection_rw_enabled FALSE
_hang_singleton_resolution_rw_enabled FALSE
_hang_statistics_collection_interval 15
_hang_statistics_collection_ma_alpha 30
_hang_statistics_high_io_percentage_threshold 25
_hang_terminate_session_replay_enabled TRUE
_hang_trace_interval 32
_hang_verification_interval 46
_hanganalyze_strip_offset TRUE
_hard_protection FALSE
_hash_join_enabled TRUE
_hash_multiblock_io_count 0
_hashops_prefetch_size 4
_hb_redo_interval 1000
_hb_redo_msg_interval 100
_hcs_disable_all_prune FALSE
_hcs_disable_all_qry_optz FALSE
_hcs_disable_av_jback_opt FALSE
_hcs_disable_av_sql_hint FALSE
_hcs_disable_basetbl_transform FALSE
_hcs_disable_bd_agg_opt FALSE
_hcs_disable_calc_dtm_to_out_opt FALSE
_hcs_disable_calc_opt FALSE
_hcs_disable_calc_union_opt FALSE
_hcs_disable_cell_qry_atr_prune_opt FALSE
_hcs_disable_cell_qry_lvl_prune_opt FALSE
_hcs_disable_cell_qry_mv_cache_opt FALSE
_hcs_disable_cell_qry_no_calc_nav_opt FALSE
_hcs_disable_cell_qry_no_out_data_opt FALSE
_hcs_disable_col_prune_optz FALSE
_hcs_disable_dt_opt_cell_qry FALSE
_hcs_disable_dtmall_opt FALSE
_hcs_disable_dup_nav_calc_opt FALSE
_hcs_disable_dup_src_tbl_opt FALSE
_hcs_disable_exists_distinct FALSE
_hcs_disable_filter_hierarchies FALSE
_hcs_disable_fltr_below_fltr_star_opt FALSE
_hcs_disable_fltr_fact_opt FALSE
_hcs_disable_fltr_hier_star_opt FALSE
_hcs_disable_hier_join_map_nonnull FALSE
_hcs_disable_inline_tmpl_opt FALSE
_hcs_disable_latest_compat_check FALSE
_hcs_disable_level_ord FALSE
_hcs_disable_level_prune FALSE
_hcs_disable_level_prune_calc_data_joins FALSE
_hcs_disable_level_prune_hier_join FALSE
_hcs_disable_level_prune_hier_qry FALSE
_hcs_disable_level_prune_hierarchize FALSE
_hcs_disable_level_prune_in_qry FALSE
_hcs_disable_level_prune_mbr_lookup FALSE
_hcs_disable_lvl_vis_lvs_no_tgts_opt FALSE
_hcs_disable_materialize FALSE
_hcs_disable_mdx_cache_hint FALSE
_hcs_disable_merge_fltr_star_opt FALSE
_hcs_disable_mv_dense_join_opt FALSE
_hcs_disable_mv_reparse_opt FALSE
_hcs_disable_mv_rewrite_check FALSE
_hcs_disable_no_bdfltrd_opt FALSE
_hcs_disable_obj_cache_name FALSE
_hcs_disable_opt_cell_qry FALSE
_hcs_disable_opt_estimate FALSE
_hcs_disable_prune_unslvd_star_opt FALSE
_hcs_disable_remoteaggr_opt FALSE
_hcs_disable_result_cache_hint FALSE
_hcs_disable_rm_agg_tgt_n_mdxqry_opt FALSE
_hcs_disable_rm_like_withs_optz FALSE
_hcs_disable_rm_unused_withs_optz FALSE
_hcs_disable_smooth_descendants FALSE
_hcs_disable_smooth_drill_all FALSE
_hcs_disable_smooth_hierarchize FALSE
_hcs_disable_smooth_noop_descendants FALSE
_hcs_disable_smooth_remove_all FALSE
_hcs_disable_unnest FALSE
_hcs_disable_use_cache_star_opt FALSE
_hcs_disable_vector_transform FALSE
_hcs_disable_view_merge FALSE
_hcs_disable_vis_totals FALSE
_hcs_disable_xform_gby FALSE
_hcs_disable_xjoin_tgt_depths_opt FALSE
_hcs_enable_aggr_opt_estimate FALSE
_hcs_enable_all_distinct FALSE
_hcs_enable_av_auto_cache TRUE
_hcs_enable_code_trc_call_stack FALSE
_hcs_enable_cube_join FALSE
_hcs_enable_expose_with_expr FALSE
_hcs_enable_fusion_code FALSE
_hcs_enable_in_mem_cdt_hint FALSE
_hcs_enable_listagg_order FALSE
_hcs_enable_mdx_cache_name_col FALSE
_hcs_enable_mdx_mv_gen FALSE
_hcs_enable_mdx_sleep_after_pin FALSE
_hcs_enable_mem_code_trc FALSE
_hcs_enable_multi_parent_opt FALSE
_hcs_enable_no_expand FALSE
_hcs_enable_parallel_hint FALSE
_hcs_enable_pred_push TRUE
_hcs_enable_time_code_trc FALSE
_hcs_enable_unref_top_chk FALSE
_hcs_enable_unsupported_calcs FALSE
_hcs_log_max_segments 1000
_hcs_log_segment_size 10
_hcs_logging SUMMARY
_hcs_max_mdx_cursors 100
_hcs_mdx_sim_sga_alloc_err NONE
_hcs_mdx_sim_so_fail FALSE
_hcs_mdx_sleep_loc NONE
_hcs_purge_dims_hiers FALSE
_hcs_query_hint
_hcs_sim_no_chgtrck FALSE
_hcs_sim_no_cont_obj FALSE
_hcs_sim_no_dense FALSE
_hcs_sim_no_joinrel FALSE
_hcs_sim_pga_expr_parse_err FALSE
_hcs_sim_sqlopt_err FALSE
_hcs_stats_max_card 2000000
_heap_dump_timeout 60
_heartbeat_config NONE
_heartbeat_period_multiplier 0
_heatmap_format_1block FALSE
_heatmap_min_maxsize 0
_heur_deadlock_resolution_secs 0
_hidden_parameter_check_control WARNING
_high_intrinsic_scn_growth_alert 1440
_high_priority_node_instcnt_cap FALSE
_high_priority_processes |LM*|LCK0|CKPT|DBRM|RMS0|CR*
_high_threshold_delta 65535
_highest_priority_processes VKTM|LGWR|LMS*|LM1*|LM2*|LM3*|LM4*|LM5*|LM6*|LM7*|
LM8*|LM9*|RS0*|RS1*|RS2*|CTWR|LGWR|LMHB|LMS*|LM1*|
LM2*|RS0*|RS1*|RS2*
_highres_drift_allowed_sec 1
_highthreshold_undoretention 31536000
_hj_bit_filter_threshold 50
_hm_analysis_oradebug_sys_dump_level 0
_hm_xm_enabled TRUE
_hnsw_post_filter_multiply_factor 0
_hnsw_post_filter_selectivity 0
_honor_maxfsize_autoextend_on FALSE
_host_internal_gateway
_hpk_compression_range 5
_hpk_project_cost_weighting 20
_hpk_throughput_range 5
_hstpr_prediction_interval 10080
_hstpr_use_linear_prediction TRUE
_hstpr_use_periodic_prediction TRUE
_http_db_service FALSE
_http_port 0
_hugetlbfs_SGA_directory @
_hugetlbfs_mount_point_for_sga
_hw_watchpoint_on TRUE
_hwm_sync_threshold 10
_hybrid_table_hidden_column FALSE
_iat_frequency_short FALSE
_idle_session_kill_enabled TRUE
_idle_session_scan_frequency 60
_idxrb_rowincr 100000000
_if_not_exists_enabled TRUE
_ignore_desc_in_index FALSE
_ignore_edition_enabled_for_EV_creation FALSE
_ignore_fg_deps
_ignore_pdb_listener FALSE
_ignore_svc_name_conv_mismatch FALSE
_ilm_mem_limit 10
_ilmflush_stat_limit 0
_ilmset_stat_limit 0
_ilmstat_memlimit 5
_im_graph_table off
_im_graph_table_exec_control 0
_im_graph_table_max_num_threads 0
_imado_cdbmem_threshold 95
_imado_diagtasks_log_period 5
_imado_diagtasks_purge_period 30
_imado_disable_bg FALSE
_imado_disable_cdbaim FALSE
_imado_dml_const 100
_imado_enable_coloptim TRUE
_imado_enable_imadv TRUE
_imado_enhancements 0
_imado_evict_sf 2
_imado_mem_threshold 98
_imado_optim_algo GREEDY
_imado_optimize_period 0
_imado_sysaux_usage_limit 90
_imado_verification 0
_image_redo_gen_delay 0
_imcu_debug_mode 0
_imga_batch_size 1024
_imga_disable FALSE
_imgt_enabled FALSE
_imgt_suppress_gc FALSE
_immediate_commit_propagation TRUE
_implicit_ssl_wallet TRUE
_improved_outerjoin_card TRUE
_improved_row_length_enabled TRUE
_imr1_slave 1
_imr_active TRUE
_imr_avoid_double_voting TRUE
_imr_check_css_incarnation_number TRUE
_imr_controlfile_access_wait_time 10
_imr_dd_slave_wait_time 30
_imr_device_type controlfile
_imr_disk_voting_interval 3
_imr_diskvote_implementation auto
_imr_evicted_member_kill TRUE
_imr_evicted_member_kill_wait 20
_imr_extra_reconfig_wait 10
_imr_highload_threshold
_imr_largest_hub_membership TRUE
_imr_max_reconfig_delay 75
_imr_mount_retry_wait_time 20
_imr_non_blocking_device_driver TRUE
_imr_remount_retry_wait_time 60
_imr_rim_mount_device FALSE
_imr_rr_holder_kill_time 300
_imr_slave_debug 0
_imr_splitbrain_res_wait 0
_imr_systemload_check TRUE
_imtxn_table_enable TRUE
_imtxn_table_flags 3
_imtxn_table_max_inc_per_slt 1
_imtxn_table_max_slts_per_seg 34
_imtxn_table_max_undo_segs 1024
_imtxnrma_table_enable FALSE
_imtxnrma_table_flags 0
_imu_pools 3
_in_memory_cdt LIMITED
_in_memory_cdt_maxpx 4
_in_memory_cleanup_wait_timeout 10000
_in_memory_memory_threshold 40
_in_memory_tbs_search TRUE
_in_memory_ts_only OFF
_in_memory_undo TRUE
_increase_lmd_process 0
_increase_lms_process 0
_incremental_purge_size 200
_incremental_recovery_ckpt_min_batch 500
_index_branch_block_check TRUE
_index_coalesce_delete_block_only FALSE
_index_coalesce_max_redo_size_target 0
_index_debug_mode 0
_index_join_enabled TRUE
_index_load_analysis_frequency 4
_index_load_block_check FALSE
_index_load_buf_oltp_over_retry 0
_index_load_buf_oltp_sacrifice_pct 10
_index_load_buf_oltp_under_pct 85
_index_load_last_leaf_comp 85
_index_load_min_key_count 10
_index_max_inc_trans_pct 20
_index_mvi_oltp_advanced_high FALSE
_index_partition_large_extents FALSE
_index_partition_shrink_opt TRUE
_index_pk_using_nonunique FALSE
_index_prefetch_factor 100
_index_relax_unique_const FALSE
_index_scan_check_skip_corrupt FALSE
_index_scan_check_stopkey FALSE
_index_split_chk_cancel 5
_indexable_con_id TRUE
_indoubt_pdb_transactions_force_outcome COMMIT
_inet_cluster_interconnects
_influx_scn_wait_timeout 1
_influx_scn_waits 100000
_init_granule_interval 10
_init_sql_file ?/rdbms/admin/sql.bsq
_inject_simulated_error_period 131072
_inject_startup_fault 0
_inline_sql_in_plsql FALSE
_inmemory_64k_percent 30
_inmemory_adg_batched_flush TRUE
_inmemory_adg_journal_quota FALSE
_inmemory_adg_parallel_flush TRUE
_inmemory_adg_periodic_sort FALSE
_inmemory_adg_quiesce_timeout 2
_inmemory_adjust_overprovisioning 1
_inmemory_analyzer_optimize_for 0
_inmemory_area_autotune TRUE
_inmemory_auto_distribute TRUE
_inmemory_autodist_2safe FALSE
_inmemory_bf_disable_threshold 0
_inmemory_bg_max_growstep 134217728
_inmemory_bg_resize_frequency 4
_inmemory_bg_resize_limit 64
_inmemory_bg_resize_target_sga_percent 50
_inmemory_buffer_waittime 100
_inmemory_check_prot_meta FALSE
_inmemory_checksum FALSE
_inmemory_crclone_buffer_size 131072
_inmemory_crclone_min_clones 6
_inmemory_crclone_min_space_percent 50
_inmemory_crclone_threshold_rows 100
_inmemory_credential 0
_inmemory_cu_checksum FALSE
_inmemory_cudrop_timeout 1000
_inmemory_dbg_retry_ext FALSE
_inmemory_dbg_scan 0
_inmemory_deepvec_transform DISABLED
_inmemory_default_flags 8459
_inmemory_default_new FALSE
_inmemory_default_svc 0
_inmemory_default_svcname
_inmemory_delta_population 0
_inmemory_direct_reads 1
_inmemory_disable_alter_imco_cycle FALSE
_inmemory_disable_selective_vircols FALSE
_inmemory_distribute_ondemand_timeout 300
_inmemory_distribute_timeout 300
_inmemory_drcancel_cu_percent 80
_inmemory_dynamic_scan_disable_threshold 20
_inmemory_dynamic_scans AUTO
_inmemory_dynamic_scans_analyze_batch_size 5
_inmemory_dynamic_scans_batch_size 500
_inmemory_dynamic_scans_dbg 0
_inmemory_dynamic_scans_result_buffers 5000
_inmemory_enable_bg_resize 0
_inmemory_enable_bg_step_grow 0
_inmemory_enable_population_verify 1
_inmemory_enable_readonly TRUE
_inmemory_enable_shrink 1
_inmemory_enable_stat_alert FALSE
_inmemory_enable_sys FALSE
_inmemory_enable_tiny_im FALSE
_inmemory_enabled FALSE
_inmemory_exclto_timeout 100
_inmemory_expression_count 20
_inmemory_expressions_area_percent 10
_inmemory_expressions_mark_unused FALSE
_inmemory_ext_roarea 0
_inmemory_ext_rwarea 0
_inmemory_external_table TRUE
_inmemory_faststart_control_flags 0
_inmemory_force_fs FALSE
_inmemory_force_fs_tbs SYSAUX
_inmemory_force_fs_tbs_size 1073741824
_inmemory_force_jgca_resizing 0
_inmemory_force_non_engineered FALSE
_inmemory_format_compatible 23.7.0.0.0
_inmemory_fs_blk_inv_blk_percent 50
_inmemory_fs_blk_inv_blkcnt
_inmemory_fs_dmlverify_read_ahead_cnt 10
_inmemory_fs_enable TRUE
_inmemory_fs_enable_blk_lvl_inv TRUE
_inmemory_fs_imco_timeout 120000
_inmemory_fs_nodml FALSE
_inmemory_fs_prune_pct 10
_inmemory_fs_raise_error FALSE
_inmemory_fs_tbsmaxsz
_inmemory_fs_test_flags 0
_inmemory_fs_verify FALSE
_inmemory_fsdw_cnt 2147483647
_inmemory_fsdw_enable TRUE
_inmemory_fsdw_inline FALSE
_inmemory_fsdw_maxcnt 10
_inmemory_fsdw_maxmem 104755200
_inmemory_fsdw_on_populate TRUE
_inmemory_fsdw_penalty_threshold 20
_inmemory_fsdw_populate_threshold_multiplier 10
_inmemory_fsdw_priority_penalty_percent 10
_inmemory_fsdw_priority_population_percent 100
_inmemory_fsdw_priority_repopulation_percent 90
_inmemory_fsdw_schedlrtm 1
_inmemory_fsdw_scheduler_dedicated FALSE
_inmemory_fsdw_task_timeout 20
_inmemory_fsdw_threshold 300
_inmemory_gd_sym_dict_flags 1
_inmemory_granule_size 134217728
_inmemory_graph_pop_fg FALSE
_inmemory_grpcolinv_buffer_size 131072
_inmemory_grpcolinv_granularity 1
_inmemory_hpk4sql_debug 0
_inmemory_hpk4sql_filter_threshold 1
_inmemory_hpk4sql_flags 0
_inmemory_hpk4sql_kv_seg_size 21
_inmemory_hpk4sql_partbuf_maxrow 1024
_inmemory_hpk4sql_partbuf_minrow 8
_inmemory_hpk4sql_pushdown_level 65535
_inmemory_hwm_expand_percent 20
_inmemory_hwm_expansion 1
_inmemory_hwm_expansion_rac 0
_inmemory_hwm_inv_blocks_threshold 64
_inmemory_hybrid_selectivity_threshold 37
_inmemory_hybridexa_enable TRUE
_inmemory_imco_cycle 120
_inmemory_imcu_align TRUE
_inmemory_imcu_populate_minbytes 5242880
_inmemory_imcu_source_analyze_bytes 134217728
_inmemory_imcu_source_blocks 0
_inmemory_imcu_source_extents 0
_inmemory_imcu_source_maxbytes 0
_inmemory_imcu_source_minbytes 1048576
_inmemory_imcu_target_bytes 0
_inmemory_imcu_target_maxrows 8388608
_inmemory_imcu_target_rows 0
_inmemory_ime_increpop_threshold 1
_inmemory_incremental_repopulation TRUE
_inmemory_invalidate_cursors TRUE
_inmemory_jgbvt_slotsz 6
_inmemory_journal_check 0
_inmemory_journal_cla_stride 4
_inmemory_journal_format 1
_inmemory_journal_row_logging FALSE
_inmemory_journal_scan 0
_inmemory_journal_scan_format TRUE
_inmemory_lock_for_smucreate FALSE
_inmemory_log_level 0
_inmemory_max_delta 5
_inmemory_max_expressions_table 50
_inmemory_max_pga_usage_percent 50
_inmemory_max_pga_usage_percol 20
_inmemory_max_populate_retry 3
_inmemory_max_queued_tasks 0
_inmemory_memprot FALSE
_inmemory_metadata_pct 0
_inmemory_min_delta_blocks 50
_inmemory_min_delta_rows 255
_inmemory_min_ima_defersize 0
_inmemory_num_hash_latches 256
_inmemory_opaque_contig_space_percent 80
_inmemory_optimized_date_options 6
_inmemory_parallel_jghj_enabled TRUE
_inmemory_parallel_load_ext TRUE
_inmemory_partrowlock_threshold 10
_inmemory_patch_background_blocks 200
_inmemory_patch_commit_path FALSE
_inmemory_patch_threshold_blocks 25
_inmemory_pct_inv_blocks_invalidate_imcu 100
_inmemory_pct_inv_rows_invalidate_imcu 50
_inmemory_pga_per_server 536870912
_inmemory_pin_hist_mode 16
_inmemory_populate_blocks_threshold 8
_inmemory_populate_fg FALSE
_inmemory_populate_grow_trigger_percent 10
_inmemory_populate_task_self_exec 0
_inmemory_populate_test_flags 0
_inmemory_populate_wait FALSE
_inmemory_populate_wait_max 600
_inmemory_prefer_xmem_memcompress
_inmemory_prefer_xmem_priority
_inmemory_prefix_encode_dsbs FALSE
_inmemory_prepopulate TRUE
_inmemory_prepopulate_fg 0
_inmemory_private_journal_aonumbkts 16
_inmemory_private_journal_dynamic TRUE
_inmemory_private_journal_grplen 64
_inmemory_private_journal_maxexts 5000000
_inmemory_private_journal_numbkts 2048
_inmemory_private_journal_numgran 32
_inmemory_private_journal_quota 100
_inmemory_private_journal_sharedpool_quota 20
_inmemory_pruning ON
_inmemory_query_check 0
_inmemory_query_fetch_by_rowid FALSE
_inmemory_query_scan TRUE
_inmemory_racgd_flags 0
_inmemory_racgd_msg_threshold 60
_inmemory_racgd_verify_populate FALSE
_inmemory_relimcusz_thresh 25
_inmemory_repopulate_disable 2
_inmemory_repopulate_flags 2
_inmemory_repopulate_invalidate_rate_percent 0
_inmemory_repopulate_optimize TRUE
_inmemory_repopulate_priority_scale_factor 100
_inmemory_repopulate_priority_threshold_block 320
_inmemory_repopulate_priority_threshold_row 160
_inmemory_repopulate_threshold_blocks
_inmemory_repopulate_threshold_blocks_percent 10
_inmemory_repopulate_threshold_mintime 0
_inmemory_repopulate_threshold_mintime_factor 5
_inmemory_repopulate_threshold_rows
_inmemory_repopulate_threshold_rows_percent 5
_inmemory_repopulate_threshold_scans 0
_inmemory_retention_time 120
_inmemory_rows_check_interrupt 1000
_inmemory_rw_pool 5
_inmemory_scan_invalid_percent 30
_inmemory_scan_override FALSE
_inmemory_servers_throttle_pgalim_percent 55
_inmemory_shared_journal_maxexts 1024
_inmemory_shared_journal_minexts_repop 256
_inmemory_shrink 0
_inmemory_shrink_cleanout_timeout 180
_inmemory_shrink_control_flags 0
_inmemory_shrink_gc_retries 3
_inmemory_shrink_test_flags 0
_inmemory_size_enable_shrink TRUE
_inmemory_small_segment_threshold 65536
_inmemory_smu_patch_options 7
_inmemory_strdlxid_timeout 0
_inmemory_subcu_histsize 0
_inmemory_subcusize 512
_inmemory_succesive_bg_rsz_interval 9000
_inmemory_suppress_vsga_ima FALSE
_inmemory_test_verification 0
_inmemory_transaction_options 10998
_inmemory_trickle_populate TRUE
_inmemory_trickle_repopulate TRUE
_inmemory_trickle_repopulate_fg 0
_inmemory_trickle_repopulate_min_interval 300
_inmemory_trickle_repopulate_threshold_dirty_ratio 0
_inmemory_txn_checksum 0
_inmemory_txnpjrnl_debug 0
_inmemory_validate_fetch FALSE
_inmemory_vector_encode_override FALSE
_inmemory_waitinvis_count 8
_inmemory_xmem_size 0
_inmemory_xt_virtual_columns DISABLE
_inplace_update_retry TRUE
_inquiry_retry_interval 3
_insert_enable_hwm_brokered TRUE
_inst_locking_period 5
_instance_dbnest_name
_instance_recovery_bloom_filter_buffer_size 4096
_instance_recovery_bloom_filter_fprate 0.01
_instance_recovery_bloom_filter_size 1048576
_instance_recovery_bloom_size_ratio 0.0003
_instant_file_create FALSE
_instant_file_create_exascale FALSE
_intra_cdb_dblink FALSE
_intrapart_pdml_enabled TRUE
_intrapart_pdml_randomlocal_enabled TRUE
_invalidate_upon_revoke TRUE
_io_internal_test 0
_io_osd_param 1
_io_outlier_threshold 500
_io_resource_manager_always_on FALSE
_io_shared_pool_size 4194304
_io_slaves_disabled FALSE
_io_statistics TRUE
_iocalibrate_init_ios 2
_iocalibrate_max_ios 0
_ioq_fanin_multiplier 2
_ior_serialize_fault 0
_iorm_tout 1000
_ios_root_directory IOS
_ioslave_batch_count 1
_ioslave_issue_count 500
_iot_overflow_tblspace_user_default FALSE
_ipacl_feature_control_flags 1
_ipc_aggr_limit_percentage 40
_ipc_config_opts_dyn 0
_ipc_config_opts_stat 0
_ipc_emu_aop_timeout 0
_ipc_fail_network 0
_ipc_switch_reconfig_needed FALSE
_ipc_test_failover 0
_ipc_test_mult_nets 0
_ipc_trace_limit
_iut_enable TRUE
_iut_max_entries 30000
_iut_stat_collection_type SAMPLED
_j0_deq_maxwait_time 0
_job_notification_handler_owners
_job_queue_interval 5
_jobs_allowed_for_common_user FALSE
_json_qryovergen_rewrite TRUE
_k2q_latches 0
_ka_allow_reenable FALSE
_ka_compatibility_requirement all
_ka_doorbell 0
_ka_enabled FALSE
_ka_grant_policy AUTO
_ka_lma_msg_wait_count 100
_ka_lma_wait_time 200
_ka_locks_per_sector 12
_ka_max_wait_delay 1000
_ka_mode 0
_ka_msg_reap_count 40
_ka_msg_wait_count 20
_ka_pbatch_messages TRUE
_ka_scn_accel_shrmem TRUE
_ka_scn_enabled FALSE
_ka_scn_use_ka_msgs TRUE
_kcb_reused_max 16384
_kcbl_assert_reset_slot TRUE
_kcc_aging_cool_count 1
_kcc_aging_freeze_cr FALSE
_kcc_aging_hot_criteria 2
_kcc_aging_stay_count 0
_kcc_aging_touch_time 3
_kcc_percent_hot_default 50
_kcfis_automem_level 1
_kcfis_block_dump_level 0
_kcfis_byteswap_opt_disabled FALSE
_kcfis_caching_enabled TRUE
_kcfis_cell_passthru_dataonly TRUE
_kcfis_cell_passthru_enabled FALSE
_kcfis_cell_passthru_fromcpu_enabled TRUE
_kcfis_cellcache_disabled FALSE
_kcfis_celloflsrv_passthru_enabled FALSE
_kcfis_celloflsrv_usage_enabled TRUE
_kcfis_control1 0
_kcfis_control2 0
_kcfis_control3 0
_kcfis_control4 0
_kcfis_control5 0
_kcfis_control6 0
_kcfis_disable_platform_decryption FALSE
_kcfis_dump_corrupt_block TRUE
_kcfis_fast_response_enabled TRUE
_kcfis_fast_response_initiosize 2
_kcfis_fast_response_iosizemult 4
_kcfis_fast_response_threshold 1048576
_kcfis_fastfileinit_disabled FALSE
_kcfis_fault_control 0
_kcfis_io_prefetch_size 8
_kcfis_ioreqs_throttle_enabled TRUE
_kcfis_ivfscan_fd_max_num_reuse 50
_kcfis_ivfscan_opt_enabled TRUE
_kcfis_kept_in_cellfc_enabled TRUE
_kcfis_large_payload_enabled FALSE
_kcfis_largemd_bfquota_kb 16384
_kcfis_largemd_compressed_kb 20480
_kcfis_largemd_enabled TRUE
_kcfis_max_cached_sessions 10
_kcfis_max_ioctl_buffers 100
_kcfis_max_out_translations 5000
_kcfis_nonkept_in_cellfc_enabled FALSE
_kcfis_oss_io_size 0
_kcfis_pmem_enabled TRUE
_kcfis_qm_prioritize_sys_plan TRUE
_kcfis_qm_user_plan_name
_kcfis_rdbms_blockio_enabled FALSE
_kcfis_read_buffer_limit 0
_kcfis_spawn_debugger FALSE
_kcfis_stats_level 0
_kcfis_storageidx_diag_mode 0
_kcfis_storageidx_disabled FALSE
_kcfis_storageidx_set_membership_disabled FALSE
_kcfis_storageidx_xtss_disabled FALSE
_kcfis_test_control1 0
_kcfis_trace_bucket_size 131072
_kcfis_xtgran_prefetch_count 1
_kcl_debug TRUE
_kcl_index_split TRUE
_kcmi_debug 0
_kcrfwrma_flags 0
_kd_dbg_control 0
_kd_rows_chk TRUE
_kd_symtab_chk TRUE
_kdbl_enable_post_allocation FALSE
_kdfip_bufl_nbkt 128
_kdfip_cmap_nbkt 16
_kdfip_debug 0
_kdfip_drain_sleeps 60
_kdfip_elem_nclatch 64
_kdfip_flush_nrows 2147483647
_kdfip_flush_rowsz 1048576
_kdfip_flush_rowtm 60
_kdfip_iga_adpt_amm_intr 30
_kdfip_iga_adpt_dec_ldpr 50
_kdfip_iga_adpt_dec_pr 5
_kdfip_iga_adpt_inc_ldpr 75
_kdfip_iga_adpt_inc_pr 25
_kdfip_iga_adpt_maxsz 0
_kdfip_iga_adpt_mem_ret 3
_kdfip_iga_bufsz 1048576
_kdfip_iga_maxsz 2147483648
_kdfip_iga_minsz 268435456
_kdfip_par_flush TRUE
_kdfip_trace FALSE
_kdfs_fix_control 0
_kdfs_timer_dmp FALSE
_kdfs_trace 1
_kdfs_trace_size 131072
_kdi_avoid_block_checking FALSE
_kdic_segarr_sz 0
_kdis_reject_level 24
_kdis_reject_limit 5
_kdis_reject_ops FALSE
_kdis_split_xid_prune TRUE
_kdivcc_test_flags 0
_kdivs_test_null_hnsw_snaphot FALSE
_kdizoltp_uncompsentinal_freq 16
_kdkv_fg_drop_memopt TRUE
_kdkv_fg_no_memopt FALSE
_kdkv_fg_populate FALSE
_kdkv_fg_repopulate FALSE
_kdkv_force_fastpath FALSE
_kdkv_force_samehash FALSE
_kdkv_index_lossy TRUE
_kdkv_index_relocate FALSE
_kdkv_indexinvalid FALSE
_kdkv_trace FALSE
_kdlf_direct_inode_path TRUE
_kdlf_fast_move_compressed_lob TRUE
_kdlf_layers_cache TRUE
_kdlf_new_compression_adv TRUE
_kdlf_read_flag 0
_kdlf_track_itrcnt 200
_kdli_STOP_bsz 0
_kdli_STOP_dba 0
_kdli_STOP_fsz 0
_kdli_STOP_nio 0
_kdli_STOP_tsn 0
_kdli_adaptive_cache_inode TRUE
_kdli_adpt_sio_mem TRUE
_kdli_allow_corrupt FALSE
_kdli_buffer_inject TRUE
_kdli_cache_hless_limit 4
_kdli_cache_inode TRUE
_kdli_cache_inode_off_limit 8192
_kdli_cache_read_threshold 0
_kdli_cache_size 8
_kdli_cache_verify FALSE
_kdli_cache_write_threshold 0
_kdli_cacheable_length 0
_kdli_checkpoint_flush FALSE
_kdli_dbc none
_kdli_delay_flushes TRUE
_kdli_descn_adj FALSE
_kdli_flush_cache_reads FALSE
_kdli_flush_injections TRUE
_kdli_force_cr TRUE
_kdli_force_cr_meta TRUE
_kdli_force_storage none
_kdli_full_readahead_threshold 0
_kdli_full_vll FALSE
_kdli_icache_entries 3
_kdli_inject_assert 0
_kdli_inject_batch 0
_kdli_inject_crash 0
_kdli_inline_xfm TRUE
_kdli_inode_preference data
_kdli_inplace_overwrite 0
_kdli_itree_entries 0
_kdli_memory_protect FALSE
_kdli_mts_so TRUE
_kdli_oneblk FALSE
_kdli_preallocation_mode length
_kdli_preallocation_pct 0
_kdli_ralc_length 10485760
_kdli_ralc_rounding 1048576
_kdli_rci_lobmap_entries 255
_kdli_readahead_limit 0
_kdli_readahead_strategy contig
_kdli_recent_scn FALSE
_kdli_reshape FALSE
_kdli_safe_callbacks TRUE
_kdli_sio_async TRUE
_kdli_sio_backoff FALSE
_kdli_sio_bps 0
_kdli_sio_chkpt TRUE
_kdli_sio_dop 2
_kdli_sio_fbwrite_pct 35
_kdli_sio_fileopen none
_kdli_sio_flush FALSE
_kdli_sio_free TRUE
_kdli_sio_min_read 0
_kdli_sio_min_write 0
_kdli_sio_nbufs 8
_kdli_sio_niods 8
_kdli_sio_on TRUE
_kdli_sio_pga FALSE
_kdli_sio_pga_top FALSE
_kdli_sio_strategy extent
_kdli_sio_write_pct 100
_kdli_small_append_redo TRUE
_kdli_small_cache_limit 32
_kdli_sort_dbas FALSE
_kdli_space_cache_limit 2048
_kdli_space_cache_segments 16
_kdli_squeeze TRUE
_kdli_timer_dmp FALSE
_kdli_timer_trc FALSE
_kdli_trace 0
_kdli_vll_direct TRUE
_kdlu_integrated_bucket TRUE
_kdlu_max_bucket_size 6291456
_kdlu_max_bucket_size_mts 131072
_kdlu_timer_dmp FALSE
_kdlu_trace_layer 0
_kdlu_trace_system 0
_kdlw_enable_ksi_locking FALSE
_kdlw_enable_write_gathering TRUE
_kdlwp_flush_threshold 4194304
_kdlwp_memory_check TRUE
_kdlwp_multi_wgc TRUE
_kdlxp_cmp_subunit_size 262144
_kdlxp_cmpappopt TRUE
_kdlxp_dedup_flush_threshold 8388608
_kdlxp_dedup_hash_algo SHA1
_kdlxp_dedup_inl_pctfree 5
_kdlxp_dedup_prefix_threshold 1048576
_kdlxp_dedup_wapp_len 0
_kdlxp_lobcmpadp FALSE
_kdlxp_lobcmplevel 2
_kdlxp_lobcmprciver 1
_kdlxp_lobcompress FALSE
_kdlxp_lobdeduplicate FALSE
_kdlxp_lobdedupvalidate TRUE
_kdlxp_lobencrypt FALSE
_kdlxp_lz4zstdcmpalgos TRUE
_kdlxp_mincmp 20
_kdlxp_mincmplen 200
_kdlxp_minxfm_size 32768
_kdlxp_no_dedup_on_insert FALSE
_kdlxp_spare1 0
_kdlxp_uncmp FALSE
_kdlxp_xfmcache TRUE
_kdmado_aim_imelig_eval_interval 60
_kdmado_disable_async TRUE
_kdmado_disable_imelig_aim TRUE
_kdmado_im_txn_mntn_wt_per_row 1
_kdmado_partial_pop_backoff_mb 64
_kdmado_st_txn_test 0
_kdmado_wt_txn_test 0
_kdmimadv_constant_speed FALSE
_kdt_buffering TRUE
_kdtgsp_retries 1024
_kdu_array_depth 16
_kdz_clear_analysis_percent 60
_kdz_hcc_flags 0
_kdz_hcc_track_upd_rids FALSE
_kdz_pcode_flags 0
_kdz_pred_nrows 32767
_kdz_proj_nrows 1024
_kdzado_postdm_mode 0
_kdzf_columnar_cache default
_kdzk_enable_init_trace FALSE
_kdzk_load_specialized_library 3
_kdzk_specialized_library_name
_kdzk_trace_level 0
_kebm_autotask_cont_resource_schedule FALSE
_kebm_autotask_nstrikes 3
_kebm_max_parallel_autotasks AUTO
_kebm_nstrikes 3
_kebm_preshut_act_enabled TRUE
_kebm_sanity_check_enabled FALSE
_kebm_suspension_time 104400
_kecap_cache_size 10240
_keep_19907_during_recovery FALSE
_keep_mutables_automatic TRUE
_keep_relocated_source_pdb FALSE
_keep_remote_column_size FALSE
_kerberos_debug 0
_kerberos_per_pdb TRUE
_kerberos_service_host
_kerberos_service_name
_kerberos_unique_cache_name FALSE
_kes_parse_model 2
_keusp_max_num_alloc_buf DEFAULT
_keusp_stream_batch_size DEFAULT
_kewm_simulate_oer4031 0
_kewm_trace_sga FALSE
_key_vector_alternate_dictionary TRUE
_key_vector_create_pushdown_threshold 20000
_key_vector_double_enabled TRUE
_key_vector_force_alternate_dictionary FALSE
_key_vector_inlist_max_size 10240
_key_vector_inlist_min_values 0
_key_vector_join_pushdown_enabled TRUE
_key_vector_max_size 524288
_key_vector_offload predicate
_key_vector_predicate_enabled TRUE
_key_vector_predicate_threshold 0
_key_vector_shared_dgk_ht TRUE
_key_vector_timestamp_enabled TRUE
_kffmap_hash_size 1024
_kffmlk_hash_size 512
_kffmof_fprate 1
_kffmof_size 1048576
_kffmop_chunks 128
_kffmop_hash_size 2048
_kffmop_list_check FALSE
_kffmspw_hash_size 128
_kfi_software_patchmap
_kfi_version_patchmap
_kfm_disable_set_fence FALSE
_kgh_free_list_min_effort 12
_kgh_restricted_subheaps 180
_kgh_restricted_trace 0
_kghdsidx_count 1
_kghdsidx_lp_count 1
_kghdsidx_numa_count 1
_kghdsidx_sp_count 1
_kghdsidx_streams_count 1
_kgl_4021_assert_on_oso FALSE
_kgl_assert_x_pin FALSE
_kgl_bucket_bitvector TRUE
_kgl_bucket_bitvector_clear TRUE
_kgl_bucket_count 9
_kgl_cluster_lock TRUE
_kgl_cluster_lock_read_mostly FALSE
_kgl_cluster_pin TRUE
_kgl_debug
_kgl_final_blocker_kill_begin_time 2
_kgl_fixed_extents TRUE
_kgl_hash_collision FALSE
_kgl_heap_size 4096
_kgl_hot_object_copies 0
_kgl_iterator_action SKIP
_kgl_kill_final_blocker FALSE
_kgl_kqr_cap_so_stacks 0
_kgl_large_heap_assert_threshold 524288000
_kgl_large_heap_warning_threshold 52428800
_kgl_latch_count 0
_kgl_max_hot_cursors_factor 25
_kgl_max_wait_time_during_kill 15
_kgl_min_cached_so_count 1
_kgl_time_to_wait_for_locks 15
_kglpgmtx_cap_uol_stack FALSE
_kglsim_maxmem_percent 5
_kgrk_configs
_kgsb_threshold_size 16777216
_kgx_latches 1024
_kill_controlfile_enqueue_blocker TRUE
_kill_diagnostics_timeout 60
_kill_enqueue_blocker 2
_kill_java_threads_on_eoc FALSE
_kill_session_alert 5
_kill_session_dump FALSE
_kill_session_force FALSE
_kjac_direct_path_enabled TRUE
_kjac_force_outcome_current_session FALSE
_kjac_purge_limit 50000
_kjac_purge_timeout 3600
_kjdd_call_stack_dump_enabled FALSE
_kjdd_wfg_dump_cntrl 0
_kjltmaxgt 1000
_kjltmaxht 1000
_kjlton FALSE
_kkfi_trace FALSE
_kkpap_cache_plsql_result TRUE
_kkpap_zm_pruning_cache TRUE
_kkpod_flush_validation LOW
_kkpod_load_tolerance FULL
_kkpogpi_nocpy 1
_kkporesetdn_multiplier 2
_kkporesetdn_threshold 2100000
_kks_always_check_bind_equivalence FALSE
_kks_cached_parse_errors 0
_kks_max_open_cursors_dup_limit 5
_kks_obsolete_dump_threshold 1
_kks_open_cursors_dump_summary_threshold 100
_kks_parse_error_warning 100
_kks_parse_failure_time_period 3600
_kks_reuse_ful_child_cursor 3
_kksfra_cap_stacks FALSE
_kktAllowInsteadOfDDLTriggeronDDL 0
_kokli_cache_size 128
_kokln_current_read FALSE
_kolfuseslf FALSE
_kpdb_log_errors 0
_kpdb_perf_diag_subop_list 0
_kpdb_perf_diag_subop_max_exec_time 30
_kqdsn_cpu_digits 3
_kqdsn_instance_digits 2
_kql_clientlocks_enabled 15
_kql_disable_auto_commit FALSE
_kql_dump_deptable_in_errorstack TRUE
_kql_max_hang_time_for_lck1 180
_kql_subheap_trace 0
_kql_verify_dependency_timestamps 0
_kqr_enable_conservative_logging TRUE
_kqr_hot_copy_sample_size 1000000
_kqr_hot_copy_sleep_limit 500
_kqr_max_hot_copies 16
_kqr_optimistic_reads TRUE
_kqr_trace_options 0
_kra_cfile_compaction TRUE
_kra_obsolete_rule TRUE
_kra_trace_buffer_size 131072
_krb_check_osd_block_endianess TRUE
_krb_trace_buffer_size 131072
_krbabr_trace_buffer_size 131072
_krc_trace_buffer_size 131072
_ksb_restart_clean_time 30000
_ksb_restart_policy_times 0, 60, 120, 240
_ksd_test_param 999
_ksdx_charset_ratio 0
_ksdxdocmd_default_timeout_ms 30000
_ksdxdocmd_enabled TRUE
_ksdxw_cini_flg 0
_ksdxw_nbufs 1000
_ksdxw_num_pgw 10
_ksdxw_num_sgw 10
_ksdxw_stack_depth 4
_ksdxw_stack_readable FALSE
_kse_alt_stack_sig_syms 25
_kse_auto_core FALSE
_kse_die_timeout 60000
_kse_pc_table_size 256
_kse_signature_entries 0
_kse_signature_limit 7
_kse_snap_ring_disable FALSE
_kse_snap_ring_record_min
_kse_snap_ring_record_stack FALSE
_kse_snap_ring_size 100
_kse_snap_ring_suppress 942 1403
_kse_ssnt FALSE
_kse_trace_int_msg_clear FALSE
_ksfd_fob_pct 0
_ksfd_verify_write FALSE
_ksfdx_tests
_ksfqp_row_count 0
_ksgl_ltchs_held_ctxt 8
_ksgl_max_dyn_latches 1024
_ksi_clientlocks_enabled TRUE
_ksi_disable_sopt TRUE
_ksi_pdb_checks TRUE
_ksi_trace
_ksi_trace_bucket SHARED
_ksi_trace_bucket_size LCK1:1048576-REST:8192
_ksim_group_ops_req_async_mode auto
_ksim_group_ops_req_async_procsz 10
_ksim_group_ops_req_async_procsz_dyn_adjustment TRUE
_ksim_group_ops_req_opmode async
_ksim_time_monitor auto
_ksipc_aspc_enabled FALSE
_ksipc_cksum_level
_ksipc_common_sl
_ksipc_ctrl_threshold_cnt
_ksipc_ctrl_threshold_ms
_ksipc_efchecks 3
_ksipc_group_sz 1024
_ksipc_heap_extent 1048576
_ksipc_ipclw_cksum_enable 0
_ksipc_ipclw_conn_dump 0
_ksipc_ipclw_enable_param
_ksipc_ipclw_library_path
_ksipc_ipclw_rcvbuf_mb 0
_ksipc_ipclw_spare_param2
_ksipc_ipclw_spare_param3
_ksipc_ipclw_spare_param4
_ksipc_ipclw_spare_param5
_ksipc_ipclw_spare_param6
_ksipc_ipclw_spare_param7
_ksipc_ipclw_spare_param8
_ksipc_ipclw_wait_diag_ms 0
_ksipc_ipclw_xrc_conn_diag 0
_ksipc_ipclw_xrc_pflags 0
_ksipc_libipc_path
_ksipc_loopback_ips
_ksipc_mga_segment_size 268435456
_ksipc_mode 0
_ksipc_netintr_timeout ipq.KSMSQ_UDP_TRANS=30
_ksipc_rds_delay_ms 1000
_ksipc_service_level
_ksipc_service_mask 1
_ksipc_skgxp_compat_library_path
_ksipc_skgxp_library_path
_ksipc_spare_param1 0
_ksipc_spare_param2
_ksipc_spare_param3 0
_ksipc_spare_param4 0
_ksipc_spare_param5 0
_ksipc_vnic_attach_limit 512
_ksipc_wait_flags 0
_ksipc_window_size
_ksipclnt_ep_mode 0
_ksipcsnsrv
_ksm_post_sga_init_notif_delay_secs 0
_ksm_pre_sga_init_notif_delay_secs 0
_ksm_shared_pool_stats_minsz 524288
_ksm_shared_pool_stats_num_pdb 8
_ksm_sp_rcr_hits 10
_ksmb_debug 0
_ksmd_protect_mode off
_ksmd_trace 0
_ksmg_granule_size 16777216
_ksmlsaf 0
_ksmsq_conn_per_epoch 0
_ksmsq_hintmaxinst 1024
_ksmsq_hintmaxproc 320
_ksnmon_int_param_1 0
_ksnmon_int_param_2 0
_ksnmon_int_param_3 0
_ksnmon_int_param_4 0
_ksnmon_int_param_5 0
_ksnmon_int_param_6 0
_ksnmon_max_flow 65535
_ksnmon_min_stats_interval_ms 5000
_ksnmon_service_enable_bitmask 2147483647
_ksnmon_str_param_1
_ksnmon_str_param_2
_kspmx_enabled FALSE
_kspmxs_flush_cache_size 1
_kspmxs_latch_freelists 2
_kspmxs_latch_usid_map_size 256
_kspmxs_max_regions 64
_kspmxs_max_waits 4
_kspmxs_txn_freelists 32
_kspmxs_upgrade_mutexes 64
_kspmxs_usid_map_size 1024
_kspmxs_wait_buckets 1024
_kspol_tac_timeout 5
_ksr_control_dyn_flags 0
_ksr_control_flags 0
_ksr_unit_test_processes 0
_ksrk_dedicated_io_threads_pct 50
_ksrk_max_io_threads_pct 40
_ksrk_pdbmax_io_thread_pct 100
_ksrk_pga_limit_pct 40
_ksrk_pga_reclaim_pct 50
_ksrk_sga_limit_pct 10
_ksrma_enabled AUTO
_ksrma_gsm_base_addr
_kss_callstack_type
_kss_quiet TRUE
_kstrc_archiver disk://localhost
_kstrc_bucket_max_size 2097152
_kstrc_max_operations 4096
_kstrc_service_mask 1
_ksu_diag_kill_time 5
_ksu_proc_percent_target 50
_ksu_proc_percent_threshold 70
_ksuitm_addon_trccmd
_ksuitm_dont_kill_dumper FALSE
_ksv_dynamic_flags1 0
_ksv_max_spawn_fail_limit 5
_ksv_pool_hang_kill_to 0
_ksv_pool_wait_timeout 600
_ksv_slave_exit_timeout 120
_ksv_spawn_control_all FALSE
_ksv_static_flags1 0
_ksvppktmode 0
_ksws_alb_block_service FALSE
_ksws_alb_session_age 120
_ksws_alb_suspend_duration 300
_ksws_alb_test_delta_override 0
_ksws_alb_test_drain_timeout 300
_ksws_alb_test_load_balance_frequency 300
_ksws_alb_test_load_percent 106
_ksws_alb_test_selection_bias 100
_ksws_child_service_override FALSE
_ksws_clb_storm_count 15
_ksws_clb_storm_interval 500
_ksws_coloc_control 1
_ksws_enable_alb TRUE
_ksws_enable_goodness_for_singleton_primary_with_t TRUE
c_service
_ksws_fallback_to_root FALSE
_ksws_goodness_control 1
_ksws_java_patching 0
_ksws_live_migration 1
_ksws_lm_drain TRUE
_ksws_lm_interval 100
_ksws_lm_max_time 6000
_ksws_modsvc_call_out_enabled TRUE
_ksws_perf_control 29
_ksws_perf_tracing 0
_ksws_rlb_cpu_busy_scope TRUE
_ksws_smart 29
_ksws_smart_frequency 900
_ksws_use_placement_template_attribute FALSE
_kswsas_close_pdb_on_lstsvc TRUE
_kswsas_db_svc_mapping
_kswsas_drain_kill_batch_size 5
_kswsas_ht_log_size 7
_kswsas_num_jp_slaves 0
_kswsas_pdb_auto_close_timeout 600
_ksxp_allow_ksxr_rolling_migration TRUE
_ksxp_compat_flags 0
_ksxp_control_flags 0
_ksxp_diagmode OFF
_ksxp_disable_clss 0
_ksxp_disable_dynamic_loading FALSE
_ksxp_disable_ipc_stats FALSE
_ksxp_dump_timeout 20
_ksxp_dynamic_skgxp_param
_ksxp_exa_ip_config 0
_ksxp_if_config 0
_ksxp_init_stats_bkts 0
_ksxp_ipclw_enabled 1
_ksxp_ipclw_ptswinsz 8
_ksxp_ksmsq_ip_config 0
_ksxp_lw_post_flags 0
_ksxp_max_stats_bkts 0
_ksxp_ping_enable TRUE
_ksxp_ping_polling_time 0
_ksxp_poll_netintr_timeout 3600
_ksxp_reaping 50
_ksxp_reporting_process LMD0
_ksxp_save_sockets 0
_ksxp_save_sockets_pattern *
_ksxp_send_timeout 300
_ksxp_skgxp_ant_options
_ksxp_skgxp_ctx_flags1 0
_ksxp_skgxp_ctx_flags1mask 0
_ksxp_skgxp_dynamic_protocol 4096
_ksxp_skgxp_inets
_ksxp_skgxp_rgn_ports 0
_ksxp_skgxp_spare_param1
_ksxp_skgxp_spare_param2
_ksxp_skgxp_spare_param3
_ksxp_skgxp_spare_param4
_ksxp_skgxpg_last_parameter 27
_ksxp_spare_param1
_ksxp_stats_mem_lmt 0
_ksxp_testing 0
_ksxp_unit_test_byte_transformation FALSE
_ksxp_validate_cnh_life_cycle 0
_ksxp_wait_flags 0
_ksz_dummy_parameter
_ksz_dummy_parameter2
_ksz_fake_mga_check_range 10
_ksz_fake_mga_mode FALSE
_ktb_debug_flags 8
_ktc_debug 0
_ktc_latches 0
_ktf_copy_mapping_freq HIGH
_ktilm_min_num_dml_trckrs_to_flush_each_flush 100
_ktilm_min_time_sec_bfr_dml_stat_flush 300
_ktilm_pct_of_dml_trckrs_to_flush_each_flush 25
_ktilm_uga_off FALSE
_ktilmsc_exp 600
_kts_dbg 0
_ktsl_dbg 0
_ktslj_segext_max_mb 0
_ktslj_segext_retry 5
_ktslj_segext_warning 10
_ktslj_segext_warning_mb 0
_ktsls_autoshrink_seg_idle_seconds 86400
_ktsls_autoshrink_seg_pen_seconds 86400
_ktsls_autoshrink_trickle_mb 1024
_ktspsrch_maxsc 1024
_ktspsrch_maxskip 5
_ktspsrch_scchk 60
_ktspsrch_scexp 60
_ktst_dbg 0
_ktst_rss_max 1000
_ktst_rss_min 100
_ktst_rss_retry 5
_ktt_tsid_reuse_threshold 60000
_ktte_ts_shrink_group 6
_ktte_ts_shrink_interval 3600
_kttets_ignore_free_space FALSE
_kttext_warning 1285
_ktu_latches 0
_ku_trace none
_kxdbio_ctx_init_count 32
_kxdbio_disable_offload_opcode 0
_kxdbio_enable_ds_opcode 0
_kxdbio_hca_loadavg_thresh 74
_kxdbio_offena_timeout 7200000
_kxdbio_ut_ctl 0
_kxs_library_cache_stats TRUE
_kxscio_cap_stacks FALSE
_large_pool_min_alloc 65536
_largepage_retry_max_count 3
_last_allocation_period 5
_latch_class_0
_latch_class_1
_latch_class_2
_latch_class_3
_latch_class_4
_latch_class_5
_latch_class_6
_latch_class_7
_latch_classes
_latch_miss_stat_sid 0
_latch_pause_count 0
_latch_pause_mode static
_latch_wait_list_pri_sleep_secs 1
_lazy_mount_nfs FALSE
_ldap_adaptive_to_no_nested_group_search TRUE
_ldap_config_force_sync_up FALSE
_ldap_config_ssl_for_sasl_md5 TRUE
_ldap_no_nested_group_search FALSE
_ldap_password_oneway_auth FALSE
_ldap_reset_user_account_flc TRUE
_ldap_use_all_direct_groups_only TRUE
_ldap_warning_on_multi_shared_mappings FALSE
_ldr_io_size 1048576
_ldr_pga_lim 0
_ldr_pga_proc_lim 0
_ldr_tempseg_threshold 8388608
_leader_pdb FALSE
_leader_pdb_guid
_leader_pdb_guid_int_app FALSE
_left_nested_loops_random TRUE
_lgwr_delay_slave_write FALSE
_lgwr_delay_write FALSE
_lgwr_delay_write_csec 300
_lgwr_delay_write_interval 10
_lgwr_io_outlier 0
_lgwr_io_slaves 0
_lgwr_max_ns_wt 1
_lgwr_ns_nl_max 1000
_lgwr_ns_nl_min 500
_lgwr_ns_sim_err 0
_lgwr_posts_for_pending_bcasts FALSE
_lgwr_ta_sim_err 0
_lgwr_thick_mode_config 1:2:1536:8192:1500
_lgwr_thin_mode_config 1:256:256:100:750
_library_cache_advice TRUE
_library_cache_dump_cooling_period 10
_library_cache_dump_interval 0
_light_work_rule_debug FALSE
_lightweight_hdrs TRUE
_like_with_bind_as_equality FALSE
_link_to_leader_pdb
_link_ts_force_online TRUE
_link_ts_name
_listener_registration_retry_secs 60
_lm_activate_lms_threshold 100
_lm_adrm_interval 300
_lm_adrm_options 3
_lm_adrm_scan_timeout 50
_lm_adrm_time_out 120
_lm_asm_enq_hashing TRUE
_lm_async_da FALSE
_lm_async_pdb_open 0
_lm_batch_compression_threshold 0
_lm_better_ddvictim TRUE
_lm_big_cluster_optimizations TRUE
_lm_broadcast_res enable_broadcast
_lm_cache_allocated_res_ratio 50
_lm_cache_enqueue
_lm_cache_lvl0_cleanup 0
_lm_cache_res_cleanup 25
_lm_cache_res_cleanup_tries 10
_lm_cache_res_options 0
_lm_cache_res_skip_cleanup 20
_lm_cache_res_type TMHWDI
_lm_check_ges_resource 0
_lm_checksum_batch_msg 0
_lm_chk_inv_domenq_ops TRUE
_lm_comm_batch_size_option 2
_lm_comm_channel msgq
_lm_comm_direct_return_free_multiple 2
_lm_comm_direct_return_hwm_add 60
_lm_comm_direct_return_retnq_trigger 1000
_lm_comm_ipclw_connect_trigger 75
_lm_comm_ipclw_wait_enable 150
_lm_comm_ipclw_wait_trigger 100
_lm_comm_monitor_pending_sends 0
_lm_comm_msgq_bufr_multiple 8
_lm_comm_msgq_busywait 0
_lm_comm_msgq_copy_buffers FALSE
_lm_comm_msgq_fixed_buffers FALSE
_lm_comm_rcv_msg_history_slots 50
_lm_comm_reap_count 1
_lm_comm_receive_buffer_multiple 2
_lm_comm_send_proxy_bufr_return_mode 1
_lm_comm_send_proxy_nr_delay 10
_lm_comm_send_proxy_send_comp_wait 100
_lm_comm_send_proxy_send_wait 50
_lm_comm_send_proxy_tkt_return TRUE
_lm_comm_send_trace_trigger 500
_lm_comm_slow_op_loop_threshold 15
_lm_comm_slow_op_spx_loop_threshold 30000
_lm_comm_slow_op_stat_dump_threshold 5
_lm_comm_sync_seq_on_send_failure TRUE
_lm_comm_tkts_adaptive TRUE
_lm_comm_tkts_adpt_rsv 1
_lm_comm_tkts_calc_period_length 100000
_lm_comm_tkts_max_add 5
_lm_comm_tkts_max_periods 10
_lm_comm_tkts_min_decrease_wait 120
_lm_comm_tkts_min_increase_wait 10
_lm_comm_tkts_mult_factor 1
_lm_comm_tkts_nullreq_threshold 1
_lm_comm_tkts_sub_factor 10
_lm_comm_wait_diag_trigger 30
_lm_compression_scheme zlib
_lm_contiguous_res_count 128
_lm_da_win_enable TRUE
_lm_da_window 1
_lm_da_window_interval 0
_lm_db_rank 6
_lm_db_ranks
_lm_dd_ignore_nodd FALSE
_lm_dd_interval 10
_lm_dd_max_search_time 180
_lm_dd_maxdump 50
_lm_dd_scan_interval 5
_lm_dd_search_cnt 3
_lm_default_failure_action 0
_lm_deferred_msg_timeout 163
_lm_domain_hash_buckets 64
_lm_drm_banned_objs
_lm_drm_batch_time 10
_lm_drm_disable 0
_lm_drm_disable_kjfc FALSE
_lm_drm_duration_limit 60
_lm_drm_duration_limit_type 1
_lm_drm_filter_history_window 60
_lm_drm_filter_history_window_type 1
_lm_drm_filters 7
_lm_drm_hiload_percentage 200
_lm_drm_lowload_percentage 200
_lm_drm_max_banned_objs 10
_lm_drm_max_requests 100
_lm_drm_min_interval 600
_lm_drm_object_scan TRUE
_lm_drm_pdb_on TRUE
_lm_drm_test_duration_limit 5
_lm_drm_we_interval 60
_lm_drm_we_size 2000
_lm_drm_window 0
_lm_drm_xlatch 0
_lm_drmopt12 184
_lm_dump_null_lock FALSE
_lm_dynamic_lms FALSE
_lm_dynamic_load TRUE
_lm_dynamic_sga_target
_lm_enable_aff_benefit_stats FALSE
_lm_enable_pdb_abort 1
_lm_enable_translation FALSE
_lm_enq_iso_enabled TRUE
_lm_enq_lock_freelist
_lm_enq_rcfg TRUE
_lm_enqueue_blocker_dump_timeout 120
_lm_enqueue_blocker_dump_timeout_cnt 30
_lm_enqueue_blocker_kill_timeout 0
_lm_enqueue_freelist 3
_lm_enqueue_timeout 360
_lm_exadata_fence_type TRUE
_lm_fdrm_stats FALSE
_lm_file_affinity
_lm_file_read_mostly
_lm_free_queue_threshold 0
_lm_freeze_kill_time 30
_lm_gcs_rht_alloc_size 4096
_lm_ges_rht_alloc_size 4096
_lm_ges_rht_mem_pct 15
_lm_gl_hash_scheme 1
_lm_global_posts TRUE
_lm_hash_control 5
_lm_hashtable_bkt_high 5
_lm_hashtable_bkt_low 3
_lm_hashtable_bkt_thr 70
_lm_hb_acceptable_hang_condition default
_lm_hb_callstack_collect_time 5
_lm_hb_callstack_collect_time_long 60
_lm_hb_cfio_timeout 70
_lm_hb_disable_check_list ARC*
_lm_hb_enable_acl_check TRUE
_lm_hb_exponential_hang_time_factor 2
_lm_hb_lgio_timeout 70
_lm_hb_maximum_hang_report_count 20
_lm_hb_per_proc_behavior default
_lm_hb_per_proc_timeout default
_lm_hb_timeout_extension
_lm_high_load_sysload_percentage 90
_lm_high_load_threshold 5
_lm_hist_bucket_trigger 500
_lm_hist_dump_trigger 100
_lm_hist_opcode_trigger 0
_lm_hvenqid4_opt 1
_lm_hwc_disabled FALSE
_lm_idle_connection_action kill
_lm_idle_connection_check TRUE
_lm_idle_connection_check_interval 140
_lm_idle_connection_instance_check_callout TRUE
_lm_idle_connection_kill TRUE
_lm_idle_connection_kill_max_skips 1
_lm_idle_connection_load_check TRUE
_lm_idle_connection_max_ignore_kill_count 2
_lm_idle_connection_quorum_threshold 50
_lm_inherited_max_requests 100
_lm_kill_fg_on_timeout TRUE
_lm_killproc_timeout 120
_lm_kjbdomlzdomscn_interval 1
_lm_lazy_domain_timeout 600
_lm_lazy_recovery_member_timeout 300
_lm_lhupd_interval 5
_lm_lmd_waittime 8
_lm_lmon_nowait_latch TRUE
_lm_lms 0
_lm_lms_hipri_yield_spincount 10
_lm_lms_no_yield FALSE
_lm_lms_opt_priority TRUE
_lm_lms_priority_check_frequency 60000
_lm_lms_priority_dynamic TRUE
_lm_lms_rt_threshold
_lm_lms_spin FALSE
_lm_lms_waittime 3
_lm_local_hp_enq TRUE
_lm_locks 12000
_lm_low_load_percentage 75
_lm_master_weight 1
_lm_max_lms 0
_lm_max_lms_block_time 5
_lm_mp_additional_big_buffers 20
_lm_mp_additional_reg_buffers 20
_lm_mp_avail_queue_threshold 0
_lm_mp_bulk_mbuf_free FALSE
_lm_mp_bulk_trigger_divisor 2
_lm_mp_expand_big_pool_percent 1
_lm_mp_expand_reg_pool_percent 5
_lm_mp_latch_trigger 4000
_lm_mp_latch_trigger_soft 40000
_lm_mp_share_lms_pools TRUE
_lm_mp_small_lms_pools TRUE
_lm_msg_batch_size 0
_lm_msg_cleanup_interval 3000
_lm_msg_pool_dump_threshold 20000
_lm_msg_pool_user_callstack_dump FALSE
_lm_mwin_req_queue_max_size 4000
_lm_new_esm 1
_lm_no_lh_check FALSE
_lm_no_sync TRUE
_lm_node_join_opt FALSE
_lm_nodrm_service_pct 95
_lm_non_fault_tolerant FALSE
_lm_nonisolated_restype TOTTUL
_lm_num_bnft_stats_buckets 1
_lm_num_msg_pools_per_type 1
_lm_num_proc_frz_dump 5
_lm_num_pt_buckets 8192
_lm_num_pt_latches 128
_lm_omni_ack_timeout 60
_lm_optmode_switch 0
_lm_pdb_domains_enable 7
_lm_pdb_preopen TRUE
_lm_pdb_preopen_timeout 1800
_lm_pdb_wait_all_gone FALSE
_lm_pdb_weight_opts 90
_lm_postevent_buffer_size 256
_lm_preregister_css_restype CF
_lm_proactive_rcvinst_opts 3
_lm_proc_freeze_timeout 70
_lm_proc_frz_dump_timeout 500
_lm_process_batching TRUE
_lm_process_lock_q_scan_limit 100
_lm_procs 1088
_lm_psrcfg TRUE
_lm_rac_spare_dp1 0
_lm_rac_spare_dp10
_lm_rac_spare_dp11 0
_lm_rac_spare_dp12 0
_lm_rac_spare_dp13 0
_lm_rac_spare_dp14 0
_lm_rac_spare_dp15 0
_lm_rac_spare_dp16 0
_lm_rac_spare_dp17 0
_lm_rac_spare_dp18 0
_lm_rac_spare_dp19 0
_lm_rac_spare_dp2 0
_lm_rac_spare_dp20 0
_lm_rac_spare_dp21 0
_lm_rac_spare_dp22 0
_lm_rac_spare_dp23 0
_lm_rac_spare_dp24 0
_lm_rac_spare_dp25 0
_lm_rac_spare_dp26 0
_lm_rac_spare_dp27 0
_lm_rac_spare_dp28 0
_lm_rac_spare_dp29 0
_lm_rac_spare_dp3 0
_lm_rac_spare_dp30 0
_lm_rac_spare_dp4 0
_lm_rac_spare_dp5 0
_lm_rac_spare_dp6
_lm_rac_spare_dp7
_lm_rac_spare_dp8
_lm_rac_spare_dp9
_lm_rac_spare_p1 0
_lm_rac_spare_p10
_lm_rac_spare_p11 0
_lm_rac_spare_p12 0
_lm_rac_spare_p13 0
_lm_rac_spare_p14
_lm_rac_spare_p15
_lm_rac_spare_p16
_lm_rac_spare_p2 0
_lm_rac_spare_p3 0
_lm_rac_spare_p4 0
_lm_rac_spare_p5 0
_lm_rac_spare_p6
_lm_rac_spare_p7
_lm_rac_spare_p8
_lm_rac_spare_p9
_lm_rcfg_kjcdump_time 60
_lm_rcfg_timeout 489
_lm_rcvinst TRUE
_lm_rcvinst_atp_opt TRUE
_lm_rcvinst_sga_threshold 85
_lm_rcvr_hang_allow_time 70
_lm_rcvr_hang_cfio_kill FALSE
_lm_rcvr_hang_check_frequency 20
_lm_rcvr_hang_check_system_load TRUE
_lm_rcvr_hang_kill TRUE
_lm_rcvr_hang_systemstate_dump_level 0
_lm_receiver_type 0
_lm_recovery_pdbw_reduction 4
_lm_recovery_set 1
_lm_reloc_use_mhint FALSE
_lm_remount_check_interval 100
_lm_req_max_life 36000
_lm_res_hash_bucket 0
_lm_res_part 128
_lm_res_tm_hash_bucket 0
_lm_resend_open_convert_timeout 30
_lm_resource_behchng 3
_lm_resource_recycle_cnt 4
_lm_ress 6000
_lm_rm_object_bypass TRUE
_lm_rm_slaves 1
_lm_rs_priority_reset_delay 30
_lm_send_mode auto
_lm_send_queue_batching TRUE
_lm_send_queue_length 5000
_lm_sendproxy_reserve 25
_lm_share_lock_opt TRUE
_lm_share_lock_pdbisolation TRUE
_lm_share_lock_restype
_lm_share_opt_async_open_pdb TRUE
_lm_single_inst_affinity_lock FALSE
_lm_singleton_pdb_opt TRUE
_lm_sndq_flush_int 5
_lm_sp_slave_mode 0
_lm_sp_slaves 0
_lm_spare_threads 0
_lm_spare_undo 0
_lm_sq_batch_factor 2
_lm_sq_batch_type auto
_lm_sq_batch_waittick 3
_lm_sq_batch_waittick_worker 10
_lm_sync_timeout 163
_lm_throttle_time_interval 60
_lm_ticket_active_sendback 50
_lm_ticket_check_inject FALSE
_lm_ticket_low_limit_warning 10
_lm_ticket_min 50
_lm_tickets 1000
_lm_timed_statistics_level 0
_lm_tkt_leak_check_count 5
_lm_tkt_leak_check_seconds 300
_lm_tx_delta 16
_lm_uid_default_lookup_value TRUE
_lm_use_gcr TRUE
_lm_use_new_defmsgtmo_action TRUE
_lm_use_tx_tsn TRUE
_lm_use_us_timer FALSE
_lm_validate_pbatch FALSE
_lm_wait_for_hub_rcv_timeout 300000
_lm_wait_pending_send_queue TRUE
_lm_watchpoint_kjmddp
_lm_watchpoint_maximum 3
_lm_watchpoint_timeout 3600
_lm_worker_mode 0
_lm_worker_threads 0
_lm_xids 1196
_lmhb_aggressive_termination FALSE
_lmhb_max_dynamic_hb 10
_lmhb_min_pct_hbcnt 0
_lmhb_minimum_idle_cpu_pct_for_action 10
_lmhb_procstate_dump_cputime_limit 60
_lmhb_procstate_dump_runtime_limit 60
_lmhb_select_final_blkr FALSE
_lmn_invalidlkr_enabled TRUE
_lms_rollbacks 0
_load_without_compile none
_lob_use_locator_varying_width FALSE
_local_arc_assert_on_wait FALSE
_local_communication_costing_enabled TRUE
_local_communication_ratio 50
_local_hang_analysis_interval_secs 3
_lock_get_soft_assert_timeout 900
_lock_next_constraint_count 3
_lock_ref_constraint_count 50
_lock_ref_descendants_count 50
_lockdown_error_ignore_user_type LOCAL
_lockdown_error_logging_mode LOG_WHEN_IGNORE_ERROR
_lockdown_exec_skip_invalidation FALSE
_lockdown_execution_check FALSE
_log_archive_buffers 10
_log_archive_dest_force_async FALSE
_log_archive_network_redo_size 10
_log_archive_prot_auto_demote FALSE
_log_archive_strong_auth TRUE
_log_archive_trace_pids
_log_blocks_during_backup TRUE
_log_buffer_coalesce FALSE
_log_buffers_corrupt FALSE
_log_buffers_debug FALSE
_log_checkpoint_recovery_check 0
_log_client_ip_address_to_alert FALSE
_log_committime_block_cleanout TRUE
_log_deletion_policy mandatory
_log_file_sync_timeout 10
_log_max_optimize_threads 128
_log_parallelism_dynamic TRUE
_log_parallelism_max 2
_log_private_mul 5
_log_private_parallelism_mul 10
_log_read_buffer_size 8
_log_read_buffers 8
_log_segment_dump_parameter TRUE
_log_segment_dump_patch TRUE
_log_silicon_secured_memory TRUE
_log_simultaneous_copies 8
_log_space_errors TRUE
_log_switch_timeout 0
_log_switch_tracing_iterations 5
_log_switch_tracing_timeout 200
_log_write_info_size 4096
_log_write_worker_post_spinwait 0
_log_write_worker_task_prefetch EARLY
_log_write_worker_task_spinwait 0
_log_writer_worker_dlm_hearbeat_update_freq 5000
_logminer_parallel_read TRUE
_logout_storm_rate 0
_logout_storm_retrycnt 600
_logout_storm_timeout 5
_long_bcast_ack_warning_threshold 500
_long_log_write_warning_threshold 500
_longops_enabled TRUE
_longops_per_latch 64
_lookup_versioned_profile FALSE
_lost_write_parallelism_change_tracking 2
_low_min_lwt_lt 4
_low_priority_processes
_low_scn_headroom_warning_threshold_days 90
_low_server_threshold 0
_lowest_priority_processes
_lowres_drift_allowed_sec 5
_lreg_max_update_history 3600
_lreg_significant_change 3
_lreg_update_lag_mins 10
_lrgdbcz6_ignore_restrictions FALSE
_ltc_trace 0
_lthread_cleanup_intv_secs 1
_lthread_clnup_hk_wait_secs 3
_lthread_clnup_pmon_softkill_wait_secs 1
_lthread_clnup_spawner_sk_wait_secs 30
_lthread_debug FALSE
_lthread_enabled TRUE
_lthread_idle_timeout_secs 600
_lthread_max_spawn_time_csecs 12000
_lthread_spawn_check_intv_ms 10
_lthread_step_debugging FALSE
_main_dead_process_scan_interval 0
_map_service_name FALSE
_master_direct_sends 63
_mav_refresh_consistent_read TRUE
_mav_refresh_double_count_prevented FALSE
_mav_refresh_opt 0
_mav_refresh_unionall_tables 3
_max_aq_persistent_queue_memory 10
_max_async_wait_for_catch_up 20
_max_clients_per_emon 8
_max_cr_rollbacks 1000
_max_data_transfer_cache_size 536870912
_max_def_granule_size 67108864
_max_defer_gran_xfer_atonce 10
_max_dist_bt_chains 8
_max_dynamic_processes 320
_max_dynamic_sessions 504
_max_exponential_sleep 0
_max_filestat_tries 10
_max_flashback_shrink_size 1048576
_max_fsu_exptime 7200
_max_fsu_segments 1024
_max_fsu_sgapcent 10
_max_fsu_stale_time 600
_max_gg_extracts 65535
_max_incident_file_size 10G
_max_io_size 1048576
_max_ios_per_worker 512
_max_jsimt_autodumps 1
_max_kcnibr_ranges 1048576
_max_large_io 0
_max_largepage_alloc_time_secs 10
_max_library_cache_dumps 1000
_max_lns_shutdown_archival_time 30
_max_log_write_parallelism 1
_max_lwt_cpu_ratio 0
_max_outstanding_log_writes 2
_max_pdb_services 0
_max_pending_scn_bcasts 9
_max_physmem_perc_mmt 90
_max_physmem_perc_sga 80
_max_physmem_perc_um 90
_max_protocol_support 10000
_max_queued_report_requests 300
_max_reasonable_scn_rate 32768
_max_remote_tool_requests 10
_max_report_flushes_percycle 0
_max_row_cache_dumps 1000
_max_rwgs_groupings 8192
_max_services 25000
_max_shrink_obj_stats 0
_max_shutdown_abort_secs 10
_max_sleep_holding_latch 4
_max_small_io 0
_max_small_page_sga_size 34359738368
_max_spacebg_msgs_percentage 50
_max_spacebg_slaves 1024
_max_spacebg_tasks 8192
_max_sql_binds 65535
_max_sql_stmt_length 0
_max_stmt_tries_sync 2
_max_string_size_bypass 0
_max_sys_next_extent 0
_maxrpop_files_inst 4
_maxrpop_instances 8
_maxval_job_queue_processes
_mdapi_transform_engine LPX
_media_recovery_read_batch 32
_mem_annotation_pr_lev 0
_mem_annotation_scale 1
_mem_annotation_sh_lev 0
_mem_annotation_store FALSE
_mem_std_extent_size 4096
_memoptimize_write_shrink_minsize TRUE
_memoptimize_writes_allow_fk DISABLE
_memoptimize_writes_no_wait FALSE
_memoptimize_xmem_pool_size 0
_memory_adi_bytes_per_alloc 0
_memory_adi_enabled TRUE
_memory_adi_extend FALSE
_memory_adi_heap_mask 610
_memory_adi_module_mask 0
_memory_adi_precise_errors FALSE
_memory_broker_log_stat_entries 5
_memory_broker_marginal_utility_bc 12
_memory_broker_marginal_utility_imc 6
_memory_broker_marginal_utility_sp 7
_memory_broker_sga_grow_split TRUE
_memory_broker_sga_grow_splitif_size 20
_memory_broker_sga_shrink_chunk_size 20
_memory_broker_sga_shrink_chunked TRUE
_memory_broker_shrink_heaps 15
_memory_broker_shrink_imc 15
_memory_broker_shrink_java_heaps 900
_memory_broker_shrink_streams_pool 900
_memory_broker_shrink_timeout 60000000
_memory_broker_stat_interval 30
_memory_checkinuse_timeintv 30
_memory_imm_mode_without_autosga TRUE
_memory_initial_sga_split_perc 60
_memory_management_tracing 0
_memory_max_tgt_inc_cnt 0
_memory_mgmt_fail_immreq FALSE
_memory_mgmt_immreq_timeout 150
_memory_nocancel_defsgareq FALSE
_memory_per_cpu_count 0
_memory_sanity_check 0
_merge_monitor_threshold 10000
_messages 640
_mga_large_page_path
_mga_pid_root_head_count 16
_mgd_rcv_handle_orphan_datafiles FALSE
_midtier_affinity_cluswait_prc_threshold 6
_midtier_affinity_goodness_threshold 2000
_min_autotask_percentage
_min_lwt_lt 10
_min_spacebg_slaves 2
_min_sys_percentage
_min_sys_process 2
_min_time_between_psp0_diag_secs 300
_min_undosegs_for_parallel_fptr 100
_minact_timeout 180
_minfree_plus 0
_minimal_stats_aggregation TRUE
_minimum_blocks_to_shrink 0
_minimum_db_flashback_retention 60
_minimum_extents_to_shrink 1
_minmax_spacebg_slaves 2
_mira_free_unused_buffers TRUE
_mira_mark_archivelog_timeout 60
_mira_num_local_buffers 25
_mira_num_receive_buffers 25
_mira_preferred_threads_to_recover 0
_mira_rcv_catchup_buffers 5
_mira_rcv_max_buffers 500
_mira_sender_process 2
_mirror_redo_buffers FALSE
_mle_compilation_dump_graph_on_crash FALSE
_mle_compilation_errors_are_fatal FALSE
_mle_compilation_sync FALSE
_mle_compile_immediately FALSE
_mle_cross_context_statement_cache TRUE
_mle_enable_compilation TRUE
_mle_enable_compilation_isolates TRUE
_mle_enable_mpk off
_mle_enable_recursion TRUE
_mle_max_heap_size 1000
_mle_regexp_accelerator SQL
_mle_session_statement_cache_size 30
_mmv_query_rewrite_enabled TRUE
_modify_column_index_unusable FALSE
_modify_other_app_object FALSE
_modify_protected_profile_parameters
_monitor_sql_stmt_length FALSE
_monitor_workload_interval 24
_mpmt_enabled FALSE
_mpmt_enabled_backgrounds *
_mpmt_fg_enabled FALSE
_mpmt_fthread_mode 0
_mpmt_prefer_enabled TRUE
_mpmt_procs_per_osp 100
_mpmt_single_process_instance FALSE
_mpmt_use_fthread FALSE
_mt_redo_log_record_wakeup_interval 1440
_mt_rfs_flush_header_interval 5
_mt_rfs_gap_interval 720
_mt_rfs_register_lag_seq 24
_mttr_stat_cf_update_freq 120
_multi-statement_pdml_support PDML
_multi_instance_pmr TRUE
_multi_join_key_table_lookup TRUE
_multi_transaction_optimization_enabled TRUE
_multiple_char_set_cdb TRUE
_multiple_instance_recovery FALSE
_multiple_name_convert_patterns FALSE
_mutex_skip_spin_waiter_count 20
_mutex_spin_count 255
_mutex_wait_scheme 2
_mutex_wait_time 1
_mv_access_compute_fresh_data ON
_mv_add_log_placeholder TRUE
_mv_cleanup_orphaned_metadata TRUE
_mv_complete_refresh_conventional FALSE
_mv_deferred_no_log_age_val TRUE
_mv_expression_extend_size 4096
_mv_generalized_oj_refresh_opt TRUE
_mv_master_lock_timeout 3
_mv_refresh_ana 0
_mv_refresh_costing rule
_mv_refresh_delta_fraction 10
_mv_refresh_enhanced_dml_detection ON_RC
_mv_refresh_eut TRUE
_mv_refresh_force_parallel_query 0
_mv_refresh_insert_no_append TRUE
_mv_refresh_new_setup_disabled FALSE
_mv_refresh_no_idx_rebuild FALSE
_mv_refresh_pipe_timeout 600
_mv_refresh_pkfk_data_units_opt auto
_mv_refresh_pkfk_relationship_opt TRUE
_mv_refresh_rebuild_percentage 10
_mv_refresh_selections TRUE
_mv_refresh_shrink_log TRUE
_mv_refresh_truncate_log FALSE
_mv_refresh_update_analysis TRUE
_mv_refresh_use_hash_sj TRUE
_mv_refresh_use_no_merge TRUE
_mv_refresh_use_stats FALSE
_mv_refsched_timeincr 300000
_mv_rolling_inv FALSE
_mwin_schedule TRUE
_nameservice_consistency_check TRUE
_nameservice_request_batching TRUE
_nanovos_library
_nanovos_name
_nanovos_type
_nbr_recovery_max_request_size 8
_nbr_recovery_target_bufs 0
_nbr_recovery_timeout 60
_nchar_imp_cnv TRUE
_nchar_imp_conv TRUE
_ncmb_readahead_enabled 0
_ncmb_readahead_tracing 0
_ncomp_shared_objects_dir
_ndb_enable FALSE
_need_administer_fine_grained_audit_policy_for_fga TRUE
_need_administer_redaction_policy_for_redact TRUE
_need_administer_row_level_security_policy_for_rls TRUE
_need_create_table_privilege_for_redact FALSE
_nested_loop_fudge 100
_nested_mv_fast_oncommit_enabled TRUE
_netldp_common_users_as_local
_new_initial_join_orders TRUE
_new_sort_cost_estimate TRUE
_newdev_service_sim FALSE
_newsort_enabled TRUE
_newsort_ordered_pct 63
_newsort_type 0
_next_constraint_cache_size 5
_next_pdbid 3
_nineteenth_spare_parameter
_nineteenth_spare_pdb_parameter
_ninetieth_spare_parameter
_ninety-eighth_spare_parameter
_ninety-fifth_spare_parameter
_ninety-first_spare_parameter
_ninety-fourth_spare_parameter
_ninety-ninth_spare_parameter
_ninety-second_spare_parameter
_ninety-seventh_spare_parameter
_ninety-sixth_spare_parameter
_ninety-third_spare_parameter
_ninth_spare_parameter
_ninth_spare_pdb_parameter
_nlj_batching_ae_flag 2
_nlj_batching_enabled 1
_nlj_batching_misses_enabled 1
_nls_binary TRUE
_nls_parameter_sync_enabled TRUE
_no_catalog
_no_objects FALSE
_no_or_expansion FALSE
_no_recovery_through_resetlogs FALSE
_no_small_file FALSE
_no_snapshot_root_clone FALSE
_no_stale_joinback_rewrite FALSE
_node_instcnt_average_interval 1800
_node_instcnt_sample_frequency 60
_node_instcnt_update_frequency 300
_nologging_apply_stall_time 1000
_nologging_block_cleanout_delay 300
_nologging_fetch_demote_count 10
_nologging_fetch_initial_interval 2
_nologging_fetch_retry_interval_cold 1800
_nologging_fetch_retry_interval_hot 60
_nologging_fetch_slv_wt 600
_nologging_kcnbuf_hash_buckets 1024
_nologging_kcnbuf_hash_latches 256
_nologging_load_slotsz 1048576
_nologging_mode_override 0
_nologging_progress_keep_alive 10
_nologging_sdcl_append_wait 200
_nologging_sendbuf_ratio 90
_nologging_slots 20
_nologging_standby_cold_buffer_timeout 500
_nologging_standby_dtc_expire 600
_nologging_standby_fetch_disable FALSE
_nologging_standby_hot_buffer_timeout 500
_nologging_standby_refetch_disable FALSE
_nologging_txn_cmt_wait 1500
_nologging_txn_history_to_sessions_percent 100
_non_app_cross_con_collection FALSE
_non_app_ignore_errors TRUE
_non_blocking_hard_parse_min_extend_time 2
_nonce_history_buffer_size 0
_nonfatalprocess_redo_dump_time_limit 3600
_noseg_for_unusable_index_enabled TRUE
_not_waiting_significant_CPU 10
_notify_crs FALSE
_ns_max_flush_wt 1
_ns_max_send_delay 15
_num_longop_child_latches 4
_num_rlslaves 8
_num_undostat_intervals 576
_numa_buffer_cache_stats 0
_numa_shift_enabled TRUE
_numa_shift_value 0
_numa_trace_level 0
_number_cached_attributes 10
_number_cached_group_memberships 2048
_number_group_memberships_per_cache_line 6
_number_ksim_group_req_threshold 64
_number_of_undo_blocks_to_prefetch 8
_numgrans_per_file 64
_nusa_data_containers
_nusa_metadata_store
_nusa_remote_data_containers
_nvm_asm_dispatchers 1
_nvm_dbw_dispatchers 1
_nvm_dispatcher_bind_policy 1
_nvm_dispatchers 1
_nvmeof_zcopy_enable FALSE
_obj_ckpt_tracing 0
_object_activity_control 0
_object_activity_disable 0
_object_activity_tracking TRUE
_object_link_fixed_enabled TRUE
_object_linked_remote FALSE
_object_number_cache_size 5
_object_reuse_bast 2
_object_statistics TRUE
_object_stats_max_entries 3072
_objectstore_odm_segment_size 0
_obsolete_result_cache_mode MANUAL
_odci_aggregate_save_space FALSE
_odci_index_pmo_rebuild FALSE
_offline_rollback_segments
_ofs_read_buffer_size 1031680
_ofs_write_buffer_size 1048576
_ogg_online_ddl TRUE
_ogms_home
_olap_adv_comp_stats_cc_precomp 20
_olap_adv_comp_stats_max_rows 100000
_olap_aggregate_buffer_size 1048576
_olap_aggregate_flags 0
_olap_aggregate_function_cache_enabled TRUE
_olap_aggregate_max_thread_tuples 5000
_olap_aggregate_min_buffer_size 1024
_olap_aggregate_min_thread_status 64
_olap_aggregate_multipath_hier FALSE
_olap_aggregate_statlen_thresh 1024
_olap_aggregate_work_per_thread 1024
_olap_aggregate_worklist_max 5000
_olap_allocate_errorlog_format %8p %8y %8z %e (%n)
_olap_allocate_errorlog_header Dim Source Basis
%-8d %-8s %-8b Description
-------- -------- -------- -----------
_olap_analyze_max 10000
_olap_continuous_trace_file false
_olap_dbgoutfile_echo_to_eventlog FALSE
_olap_dimension_corehash_force FALSE
_olap_dimension_corehash_large 50000
_olap_dimension_corehash_pressure 90
_olap_dimension_corehash_size 30
_olap_disable_loop_optimized FALSE
_olap_eif_export_lob_size 2147483647
_olap_lmgen_dim_size 100
_olap_lmgen_meas_size 1000
_olap_object_hash_class 3
_olap_page_pool_expand_rate 20
_olap_page_pool_hi 50
_olap_page_pool_hit_target 100
_olap_page_pool_low 262144
_olap_page_pool_pressure 90
_olap_page_pool_shrink_rate 50
_olap_parallel_update_server_num 0
_olap_parallel_update_small_threshold 1000
_olap_parallel_update_threshold 1000
_olap_row_load_time_precision DEFAULT
_olap_sesscache_enabled TRUE
_olap_sort_buffer_pct 10
_olap_sort_buffer_size 262144
_olap_statbool_corebits 20000000
_olap_statbool_threshold 8100
_olap_table_function_statistics FALSE
_olap_wrap_errors FALSE
_olapi_history_retention FALSE
_olapi_iface_object_history 1000
_olapi_iface_object_history_retention FALSE
_olapi_iface_operation_history_retention FALSE
_olapi_interface_operation_history 1000
_olapi_memory_operation_history 1000
_olapi_memory_operation_history_pause_at_seqno 0
_olapi_memory_operation_history_retention FALSE
_olapi_session_history 300
_olapi_session_history_retention FALSE
_old_connect_by_enabled FALSE
_old_extent_scheme FALSE
_ols_cleanup_task TRUE
_oltp_comp_dbg_scan 0
_oltp_compress_dbg 0
_oltp_compression TRUE
_oltp_compression_gain 10
_oltp_spill FALSE
_omf enabled
_omni_enqueue_enable 1
_one-hundred-and-eighteenth_spare_parameter
_one-hundred-and-eighth_spare_parameter
_one-hundred-and-eightieth_spare_parameter FALSE
_one-hundred-and-eighty-eighth_spare_parameter FALSE
_one-hundred-and-eighty-fifth_spare_parameter FALSE
_one-hundred-and-eighty-first_spare_parameter FALSE
_one-hundred-and-eighty-fourth_spare_parameter FALSE
_one-hundred-and-eighty-ninth_spare_parameter FALSE
_one-hundred-and-eighty-second_spare_parameter FALSE
_one-hundred-and-eighty-seventh_spare_parameter FALSE
_one-hundred-and-eighty-sixth_spare_parameter FALSE
_one-hundred-and-eighty-third_spare_parameter FALSE
_one-hundred-and-eleventh_spare_parameter
_one-hundred-and-fifteenth_spare_parameter
_one-hundred-and-fifth_spare_parameter
_one-hundred-and-fiftieth_spare_parameter FALSE
_one-hundred-and-fifty-eighth_spare_parameter FALSE
_one-hundred-and-fifty-fifth_spare_parameter FALSE
_one-hundred-and-fifty-first_spare_parameter FALSE
_one-hundred-and-fifty-fourth_spare_parameter FALSE
_one-hundred-and-fifty-ninth_spare_parameter FALSE
_one-hundred-and-fifty-second_spare_parameter FALSE
_one-hundred-and-fifty-seventh_spare_parameter FALSE
_one-hundred-and-fifty-sixth_spare_parameter FALSE
_one-hundred-and-fifty-third_spare_parameter FALSE
_one-hundred-and-first_spare_parameter
_one-hundred-and-fortieth_spare_parameter
_one-hundred-and-forty-eighth_spare_parameter FALSE
_one-hundred-and-forty-fifth_spare_parameter FALSE
_one-hundred-and-forty-first_spare_parameter FALSE
_one-hundred-and-forty-fourth_spare_parameter FALSE
_one-hundred-and-forty-ninth_spare_parameter FALSE
_one-hundred-and-forty-second_spare_parameter FALSE
_one-hundred-and-forty-seventh_spare_parameter FALSE
_one-hundred-and-forty-sixth_spare_parameter FALSE
_one-hundred-and-forty-third_spare_parameter FALSE
_one-hundred-and-fourteenth_spare_parameter
_one-hundred-and-fourth_spare_parameter
_one-hundred-and-nineteenth_spare_parameter
_one-hundred-and-ninetieth_spare_parameter FALSE
_one-hundred-and-ninety-eighth_spare_parameter FALSE
_one-hundred-and-ninety-fifth_spare_parameter FALSE
_one-hundred-and-ninety-first_spare_parameter FALSE
_one-hundred-and-ninety-fourth_spare_parameter FALSE
_one-hundred-and-ninety-ninth_spare_parameter FALSE
_one-hundred-and-ninety-second_spare_parameter FALSE
_one-hundred-and-ninety-seventh_spare_parameter FALSE
_one-hundred-and-ninety-sixth_spare_parameter FALSE
_one-hundred-and-ninety-third_spare_parameter FALSE
_one-hundred-and-ninth_spare_parameter
_one-hundred-and-second_spare_parameter
_one-hundred-and-seventeenth_spare_parameter
_one-hundred-and-seventh_spare_parameter
_one-hundred-and-seventieth_spare_parameter FALSE
_one-hundred-and-seventy-eighth_spare_parameter FALSE
_one-hundred-and-seventy-fifth_spare_parameter FALSE
_one-hundred-and-seventy-first_spare_parameter FALSE
_one-hundred-and-seventy-fourth_spare_parameter FALSE
_one-hundred-and-seventy-ninth_spare_parameter FALSE
_one-hundred-and-seventy-second_spare_parameter FALSE
_one-hundred-and-seventy-seventh_spare_parameter FALSE
_one-hundred-and-seventy-sixth_spare_parameter FALSE
_one-hundred-and-seventy-third_spare_parameter FALSE
_one-hundred-and-sixteenth_spare_parameter
_one-hundred-and-sixth_spare_parameter
_one-hundred-and-sixtieth_spare_parameter FALSE
_one-hundred-and-sixty-eighth_spare_parameter FALSE
_one-hundred-and-sixty-fifth_spare_parameter FALSE
_one-hundred-and-sixty-first_spare_parameter FALSE
_one-hundred-and-sixty-fourth_spare_parameter FALSE
_one-hundred-and-sixty-ninth_spare_parameter FALSE
_one-hundred-and-sixty-second_spare_parameter FALSE
_one-hundred-and-sixty-seventh_spare_parameter FALSE
_one-hundred-and-sixty-sixth_spare_parameter FALSE
_one-hundred-and-sixty-third_spare_parameter FALSE
_one-hundred-and-tenth_spare_parameter
_one-hundred-and-third_spare_parameter
_one-hundred-and-thirteenth_spare_parameter
_one-hundred-and-thirtieth_spare_parameter
_one-hundred-and-thirty-eighth_spare_parameter
_one-hundred-and-thirty-fifth_spare_parameter
_one-hundred-and-thirty-first_spare_parameter
_one-hundred-and-thirty-fourth_spare_parameter
_one-hundred-and-thirty-ninth_spare_parameter
_one-hundred-and-thirty-second_spare_parameter
_one-hundred-and-thirty-seventh_spare_parameter
_one-hundred-and-thirty-sixth_spare_parameter
_one-hundred-and-thirty-third_spare_parameter
_one-hundred-and-twelfth_spare_parameter
_one-hundred-and-twentieth_spare_parameter
_one-hundred-and-twenty-eighth_spare_parameter
_one-hundred-and-twenty-fifth_spare_parameter
_one-hundred-and-twenty-first_spare_parameter
_one-hundred-and-twenty-fourth_spare_parameter
_one-hundred-and-twenty-ninth_spare_parameter
_one-hundred-and-twenty-second_spare_parameter
_one-hundred-and-twenty-seventh_spare_parameter
_one-hundred-and-twenty-sixth_spare_parameter
_one-hundred-and-twenty-third_spare_parameter
_one-hundredth_spare_parameter
_oneside_colstat_for_equijoins TRUE
_onl_ddl_progress 3
_onl_pmo_wait_query 0
_onl_pmo_wait_timeout 0
_online_ctas_diag 0
_online_ddl_delay 200
_online_ddl_domain_index_flags 1
_online_direct_load 2
_online_file_conversion_aiolimit 8
_online_file_conversion_batchsize 64
_online_patch_disable_stack_check FALSE
_online_pmo_global_index_flags 0
_online_pmo_global_index_method CLEANUP ONLY
_ops_per_semop
_optim_adjust_for_part_skews TRUE
_optim_dict_stats_at_db_cr_upg TRUE
_optim_enhance_nnull_detection TRUE
_optim_new_default_join_sel TRUE
_optim_peek_user_binds TRUE
_optimize_dvconfig_cloudpdb FALSE
_optimize_tbsquota_ddl TRUE
_optimizefsio
_optimizer_adaptive_cursor_sharing TRUE
_optimizer_adaptive_plan_control 0
_optimizer_adaptive_plans_continuous FALSE
_optimizer_adaptive_plans_iterative FALSE
_optimizer_adaptive_random_seed 0
_optimizer_adjust_for_nulls TRUE
_optimizer_ads_for_pq FALSE
_optimizer_ads_max_table_count 0
_optimizer_ads_result_cache_life 3600
_optimizer_ads_spd_cache_owner_limit 64
_optimizer_ads_time_limit 0
_optimizer_ads_use_partial_results TRUE
_optimizer_ads_use_result_cache TRUE
_optimizer_ads_use_spd_cache TRUE
_optimizer_aggr_groupby_elim TRUE
_optimizer_allow_all_access_paths TRUE
_optimizer_ansi_join_lateral_enhance TRUE
_optimizer_ansi_rearchitecture TRUE
_optimizer_answering_query_using_stats FALSE
_optimizer_autostats_job TRUE
_optimizer_aw_join_push_enabled TRUE
_optimizer_aw_stats_enabled TRUE
_optimizer_band_join_aware TRUE
_optimizer_batch_table_access_by_rowid TRUE
_optimizer_better_inlist_costing ALL
_optimizer_block_size 8192
_optimizer_bushy_cost_factor 100
_optimizer_bushy_fact_dim_ratio 20
_optimizer_bushy_fact_min_size 100000
_optimizer_bushy_join off
_optimizer_cache_stats FALSE
_optimizer_cartesian_enabled TRUE
_optimizer_cbqt_factor 50
_optimizer_cbqt_no_size_restriction TRUE
_optimizer_cbqt_or_expansion ON
_optimizer_ceil_cost TRUE
_optimizer_cluster_by_rowid TRUE
_optimizer_cluster_by_rowid_batch_size 100
_optimizer_cluster_by_rowid_batched TRUE
_optimizer_cluster_by_rowid_control 129
_optimizer_coalesce_subqueries TRUE
_optimizer_compare_plans_control 0
_optimizer_complex_pred_selectivity TRUE
_optimizer_compute_index_stats TRUE
_optimizer_connect_by_cb_whr_only FALSE
_optimizer_connect_by_combine_sw TRUE
_optimizer_connect_by_cost_based TRUE
_optimizer_connect_by_elim_dups TRUE
_optimizer_control_shard_qry_processing 65280
_optimizer_correct_sq_selectivity TRUE
_optimizer_cost_based_transformation LINEAR
_optimizer_cost_filter_pred FALSE
_optimizer_cost_hjsmj_multimatch TRUE
_optimizer_cost_model CHOOSE
_optimizer_cube_join_enabled TRUE
_optimizer_db_blocks_buffers 0
_optimizer_degree 0
_optimizer_diag_stats TRUE
_optimizer_dim_subq_join_sel TRUE
_optimizer_disable_strans_sanity_checks 0
_optimizer_distinct_agg_transform TRUE
_optimizer_distinct_elimination TRUE
_optimizer_distinct_placement TRUE
_optimizer_dsdir_usage_control 0
_optimizer_dyn_smp_blks 32
_optimizer_eliminate_filtering_join TRUE
_optimizer_eliminate_subquery TRUE
_optimizer_enable_density_improvements TRUE
_optimizer_enable_extended_stats TRUE
_optimizer_enable_plsql_stats TRUE
_optimizer_enable_table_lookup_by_nl TRUE
_optimizer_enhanced_filter_push TRUE
_optimizer_enhanced_join_elimination TRUE
_optimizer_exists_to_any_rewrite TRUE
_optimizer_extend_jppd_view_types TRUE
_optimizer_extended_cursor_sharing UDO
_optimizer_extended_cursor_sharing_rel SIMPLE
_optimizer_extended_stats_usage_control 192
_optimizer_false_filter_pred_pullup TRUE
_optimizer_fast_access_pred_analysis TRUE
_optimizer_fast_pred_transitivity TRUE
_optimizer_feedback_control
_optimizer_filter_pred_pullup TRUE
_optimizer_filter_pushdown TRUE
_optimizer_fkr_index_cost_bias 10
_optimizer_force_CBQT
_optimizer_force_error_CBQT
_optimizer_force_error_hash
_optimizer_force_error_state
_optimizer_free_transformation_heap TRUE
_optimizer_full_outer_join_to_outer TRUE
_optimizer_gather_feedback TRUE
_optimizer_gather_stats_on_conventional_config 0
_optimizer_gather_stats_on_conventional_dml FALSE
_optimizer_gather_stats_on_load TRUE
_optimizer_gather_stats_on_load_all FALSE
_optimizer_gather_stats_on_load_hist FALSE
_optimizer_gather_stats_on_load_index TRUE
_optimizer_generate_ptf_implied_preds TRUE
_optimizer_generate_transitive_pred TRUE
_optimizer_group_by_placement TRUE
_optimizer_hll_entry 4096
_optimizer_hybrid_fpwj_enabled TRUE
_optimizer_improve_selectivity TRUE
_optimizer_inmemory_access_path TRUE
_optimizer_inmemory_autodop TRUE
_optimizer_inmemory_bloom_filter TRUE
_optimizer_inmemory_capture_stored_stats TRUE
_optimizer_inmemory_cluster_aware_dop TRUE
_optimizer_inmemory_gen_pushable_preds TRUE
_optimizer_inmemory_minmax_pruning TRUE
_optimizer_inmemory_pruning_ratio_rows 100
_optimizer_inmemory_quotient 0
_optimizer_inmemory_table_expansion TRUE
_optimizer_inmemory_use_stored_stats AUTO
_optimizer_instance_count 0
_optimizer_interleave_jppd TRUE
_optimizer_interleave_or_expansion TRUE
_optimizer_invalidation_period 18000
_optimizer_join_elimination_enabled TRUE
_optimizer_join_factorization TRUE
_optimizer_join_order_control 3
_optimizer_join_sel_sanity_check TRUE
_optimizer_key_vector_aggr_factor 75
_optimizer_key_vector_payload TRUE
_optimizer_key_vector_payload_dim_aggs TRUE
_optimizer_key_vector_pruning_enabled TRUE
_optimizer_key_vector_use_max_size 1048576
_optimizer_max_permutations 300
_optimizer_min_cache_blocks 10
_optimizer_mjc_enabled TRUE
_optimizer_mode_force TRUE
_optimizer_multi_level_push_pred TRUE
_optimizer_multi_table_outerjoin TRUE
_optimizer_multicol_join_elimination TRUE
_optimizer_multiple_cenv
_optimizer_multiple_cenv_report result
_optimizer_multiple_cenv_stmt query
_optimizer_native_full_outer_join FORCE
_optimizer_nested_loop_join on
_optimizer_nested_rollup_for_gset 100
_optimizer_new_join_card_computation TRUE
_optimizer_nlj_hj_adaptive_join TRUE
_optimizer_non_blocking_hard_parse TRUE
_optimizer_null_accepting_semijoin TRUE
_optimizer_null_aware_antijoin TRUE
_optimizer_or_expansion DEPTH
_optimizer_or_expansion_subheap TRUE
_optimizer_order_by_elimination_enabled TRUE
_optimizer_outer_join_to_inner TRUE
_optimizer_outer_to_anti_enabled TRUE
_optimizer_partial_join_eval TRUE
_optimizer_percent_parallel 101
_optimizer_performance_feedback OFF
_optimizer_proc_rate_level BASIC
_optimizer_proc_rate_source DEFAULT
_optimizer_purge_stats_iteration_row_count 10000
_optimizer_push_down_distinct 0
_optimizer_push_gby_into_union_all TRUE
_optimizer_push_pred_cost_based TRUE
_optimizer_random_plan 0
_optimizer_reduce_groupby_key TRUE
_optimizer_reuse_cost_annotations TRUE
_optimizer_rownum_bind_default 10
_optimizer_rownum_pred_based_fkr TRUE
_optimizer_save_stats TRUE
_optimizer_search_limit 5
_optimizer_secure_view_merging TRUE
_optimizer_self_induced_cache_cost FALSE
_optimizer_skip_scan_enabled TRUE
_optimizer_skip_scan_guess FALSE
_optimizer_sortmerge_join_enabled TRUE
_optimizer_sortmerge_join_inequality TRUE
_optimizer_squ_bottomup TRUE
_optimizer_star_tran_in_with_clause TRUE
_optimizer_star_trans_min_cost 0
_optimizer_star_trans_min_ratio 0
_optimizer_starplan_enabled TRUE
_optimizer_stats_on_conventional_dml_sample_rate 100
_optimizer_strans_adaptive_pruning TRUE
_optimizer_subsume_vw_sq ON
_optimizer_synopsis_min_size 2
_optimizer_system_stats_usage TRUE
_optimizer_table_expansion TRUE
_optimizer_trace none
_optimizer_track_hint_usage TRUE
_optimizer_transitivity_retain TRUE
_optimizer_try_st_before_jppd TRUE
_optimizer_undo_changes FALSE
_optimizer_undo_cost_change 23.1.0
_optimizer_union_all_gsets TRUE
_optimizer_unnest_all_subqueries TRUE
_optimizer_unnest_corr_set_subq TRUE
_optimizer_unnest_disjunctive_subq TRUE
_optimizer_unnest_scalar_sq TRUE
_optimizer_unnest_update_set_subq on
_optimizer_use_auto_indexes AUTO
_optimizer_use_cbqt_star_transformation TRUE
_optimizer_use_feedback TRUE
_optimizer_use_feedback_for_join FALSE
_optimizer_use_gtt_session_stats TRUE
_optimizer_use_histograms TRUE
_optimizer_use_stats_models FALSE
_optimizer_use_stats_on_conventional_config 0
_optimizer_use_stats_on_conventional_dml FALSE
_optimizer_use_subheap TRUE
_optimizer_use_table_scanrate HADOOP_ONLY
_optimizer_use_xt_rowid TRUE
_optimizer_vector_base_dim_fact_factor 200
_optimizer_vector_cost_adj 100
_optimizer_vector_fact_dim_ratio 10
_optimizer_vector_fact_payload_ratio 20
_optimizer_vector_index ON
_optimizer_vector_index_covering_columns TRUE
_optimizer_vector_min_fact_rows 10000000
_optimizer_vector_transformation TRUE
_optimizer_wc_filter_pushdown TRUE
_or_expand_nvl_predicate TRUE
_oracle_employee_testing FALSE
_oracle_script FALSE
_oracle_script_counter 0
_oracle_special_license_1_granted FALSE
_oradbg_pathname
_oradebug_cmds_at_startup
_oradebug_force FALSE
_ordered_nested_loop TRUE
_ordered_semijoin TRUE
_orph_cln_interval 1200
_os_nice_high 10
_os_nice_highest 0
_os_nice_low 30
_os_nice_lowest 39
_os_nice_normal 20
_os_sched_high_priority 1
_os_sched_highest_priority 1
_os_sched_low_priority 1
_os_sched_lowest_priority 1
_os_sched_normal_priority 1
_os_sched_use_nice TRUE
_oss_skgxp_udp_dynamic_credit_mgmt
_other_wait_event_exclusion
_other_wait_threshold 0
_outline_bitmap_tree TRUE
_override_datafile_encrypt_check FALSE
_parallel_adaptive_max_users 4
_parallel_blackbox_enabled TRUE
_parallel_blackbox_sga TRUE
_parallel_blackbox_size 16384
_parallel_broadcast_enabled TRUE
_parallel_cluster_cache_pct 80
_parallel_cluster_cache_policy ADAPTIVE
_parallel_conservative_queuing FALSE
_parallel_ctas_enabled TRUE
_parallel_default_max_instances 1
_parallel_execution_message_align FALSE
_parallel_fake_class_pct 0
_parallel_fault_tolerance_enabled FALSE
_parallel_fault_tolerance_threshold 3
_parallel_fixwrite_bucket 1000
_parallel_frz_step_reconfig 0
_parallel_heartbeat_snapshot_interval 2
_parallel_heartbeat_snapshot_max 128
_parallel_inmemory_min_time_threshold AUTO
_parallel_inmemory_time_unit 1
_parallel_lmd_reconfig 1
_parallel_load_bal_unit 0
_parallel_load_balancing TRUE
_parallel_load_publish_threshold 10
_parallel_log_write_cleanup TRUE
_parallel_min_message_pool 491520
_parallel_optimization_phase_for_local FALSE
_parallel_queuing_max_waitingtime
_parallel_recovery_stopat 32767
_parallel_replay_msg_limit 4000
_parallel_scalability 50
_parallel_server_idle_time 30000
_parallel_server_memory_threshold 0
_parallel_server_resiliency 0
_parallel_server_sleep_time 1
_parallel_slave_acquisition_wait 1
_parallel_statement_queuing FALSE
_parallel_syspls_obey_force TRUE
_parallel_time_unit 10
_parallel_txn_global FALSE
_parallelism_cost_fudge_factor 350
_parameter_spfile_sync FALSE
_parameter_table_block_size 2048
_parquet_max_int_file_size 33554432
_parquet_tot_int_file_size 536870912
_part_layer_performance_trace 0
_part_redef_global_index_update TRUE
_partial_comp_enabled TRUE
_partial_log_preserve_space TRUE
_partial_pwise_join_enabled TRUE
_partition_advisor_srs_active true
_partition_by_con_name FALSE
_partition_by_expression FALSE
_partition_cdb_view_enabled TRUE
_partition_key_errmsg_limit 128
_partition_key_errtrc_limit 16384
_partition_large_extents TRUE
_partition_read_only TRUE
_partition_view_enabled TRUE
_partn_blackbox_size 16384
_passwordfile_enqueue_timeout 900
_path_prefix_create_dir TRUE
_path_prefix_override_dir
_pbkdf2_sder_count 3
_pct_refresh_double_count_prevented TRUE
_pdb_auto_save_state FALSE
_pdb_auto_undots_create_off FALSE
_pdb_char_set_intconv FALSE
_pdb_clone_preserve_guid FALSE
_pdb_close_immediate_kill_batchsize 1000
_pdb_cluster_database TRUE
_pdb_component_violation_restricted
_pdb_create_use_sysoper_conn FALSE
_pdb_datapatch_violation_restricted TRUE
_pdb_failure_testing 0
_pdb_file_copy_affinitize FALSE
_pdb_file_copy_buffers 8
_pdb_first_script FALSE
_pdb_force_cfd FALSE
_pdb_hash_table_latches 16
_pdb_hash_table_size 255
_pdb_hybrid_read_only FALSE
_pdb_ignore_table_clauses TRUE
_pdb_inherit_cfd FALSE
_pdb_isolation_class NONE
_pdb_ktg_buffer_size 16
_pdb_ldp_cascade 0
_pdb_lifespan_callout
_pdb_local_undo_tablespace_init_size 100000000
_pdb_lockdown_bypass_sr 0
_pdb_lockdown_ddl_clauses 0
_pdb_lockdown_error_message FALSE
_pdb_lrg_auto_undots_create FALSE
_pdb_mask_cdb_info FALSE
_pdb_max_audit_size 0
_pdb_max_diag_size 0
_pdb_max_size_discount 10
_pdb_media_rcv_parallelism 0
_pdb_name_case_sensitive FALSE
_pdb_oper_trace_threshold 600
_pdb_oper_trace_threshold_softassert FALSE
_pdb_read_only_refresh FALSE
_pdb_refresh_apply_master_key_rekey TRUE
_pdb_refresh_log_info_callout
_pdb_refresh_remote_logs_baseuri
_pdb_refresh_remote_logs_path
_pdb_refresh_restrict_until_point FALSE
_pdb_refresh_scn_to_seq_exttbl
_pdb_refresh_use_dblink_to_catalog FALSE
_pdb_refresh_use_local_logs TRUE
_pdb_relocate_read_only_open TRUE
_pdb_replay_param_allowlist
_pdb_replay_param_blocklist
_pdb_replay_param_mode DISABLED
_pdb_seed_mcsc FALSE
_pdb_service_name_convert
_pdb_service_on_root_listener FALSE
_pdb_skiplist_apply_callout
_pdb_skiplist_redogen_callout
_pdb_small_table_threshold 20
_pdb_strict_plugin_compat FALSE
_pdb_transition_clean_bg_delay 0
_pdb_trigger_user
_pdb_use_sequence_cache TRUE
_pdb_vm_max_size
_pdbopen_fixedtablestats FALSE
_pdc_adaptive FALSE
_pdc_adaptive_evaluation_delta 10
_pdc_adaptive_evaluation_duration 10
_pdc_adaptive_evaluation_interval 60
_pdc_adaptive_evaluation_margin 5
_pdc_adaptive_evaluation_successes 2
_pdc_concurrency 16
_pdc_file_clear FALSE
_pdc_imu_pct 0
_pdc_imud_flush TRUE
_pdc_inst_bocs 1
_pdc_max_mirrors 2
_pdc_min_mirrors 2
_pdc_msrdma TRUE
_pdc_non_imu_pct 0
_pdc_plb_stealing TRUE
_pdc_ptn_unit_size 65536
_pdc_read_full_ptn FALSE
_pdc_reconfig_interval 30
_pdc_remove_all_files 0
_pdc_resilver TRUE
_pdc_resilver_single FALSE
_pdc_simulation FALSE
_pdc_test_hook 0
_pdc_txn_time 5
_pdc_units_per_ptn 4
_pdc_use_partnership_map TRUE
_pdml_gim_sampling 5000
_pdml_gim_staggered FALSE
_pdml_slaves_diff_part TRUE
_percent_flashback_buf_partial_full 50
_pga_aggregate_xmem_limit 0
_pga_auto_snapshot_percentage 20
_pga_auto_snapshot_threshold 524288000
_pga_in_sga_param1
_pga_in_sga_param2
_pga_in_sga_param3
_pga_in_sga_param4
_pga_in_sga_param5
_pga_incident_app_usage_perc 75
_pga_large_extent_size 1048576
_pga_limit_check_wait_time 1000000
_pga_limit_dump_summary TRUE
_pga_limit_interrupt_smaller FALSE
_pga_limit_min_req_size 4194304
_pga_limit_per_process_minimum 3145728
_pga_limit_physmem_perc 90
_pga_limit_simulated_physmem_size 0
_pga_limit_target_perc 200
_pga_limit_time_to_interrupt 2
_pga_limit_time_until_idle 15
_pga_limit_time_until_killed 30
_pga_limit_tracing 0
_pga_limit_use_immediate_kill TRUE
_pga_limit_watch_perc 50
_pga_limit_watch_size 104857600
_pga_max_size 245350400
_pgactx_cap_stacks FALSE
_pin_time_statistics FALSE
_pivot_implementation_method CHOOSE
_pkt_enable FALSE
_pkt_pmon_interval 50
_pkt_start FALSE
_plan_outline_data TRUE
_plan_verify_absolute_margin 100000
_plan_verify_improvement_margin 150
_plcmnt_template_svc_name
_plsql_anon_block_code_type INTERPRETED
_plsql_bypass_strict_semantics FALSE
_plsql_cache_enable TRUE
_plsql_dump_buffer_events
_plsql_icd_arg_dump FALSE
_plsql_max_frame_count 0
_plsql_max_stack_size 0
_plsql_minimum_cache_hit_percent 20
_plsql_native_frame_threshold 4294967294
_plsql_nvl_optimize FALSE
_plsql_share_instantiation TRUE
_pluggable_database_debug 0
_pmem_exchange_cold_victim_threshold 0
_pmem_small_table_threshold 20
_pmemfs_alloc_dataptrs 1
_pmemfs_enable_spacetracking FALSE
_pmemfs_shrink_level 0
_pmemfs_smallfile_threshold 1024
_pmon_cleanup_max_dfs 100
_pmon_dead_blkrs_alive_chk_rate_secs 3
_pmon_dead_blkrs_max_blkrs 50
_pmon_dead_blkrs_max_cleanup_attempts 5
_pmon_dead_blkrs_scan_rate_secs 3
_pmon_enable_dead_blkrs TRUE
_pmon_exitnfy_enabled FALSE
_pmon_idle_scan_interval 60
_pmon_incr_slaves 3
_pmon_load_constants 300,192,64,3,10,10,0,0
_pmon_max_consec_posts 5
_pmon_max_slaves 10
_pmon_min_slaves 1
_pmon_mutex_cleanup 1
_pmon_new_slave_secs 30
_pmon_slave_stop_secs 60
_pmon_slaves_arr_size 160
_pmon_trees_per_slave 10
_port_internal_gateway 0
_posix_spawn_enabled TRUE
_post_multiple_shared_waiters TRUE
_post_run_job_evaluation FALSE
_post_wait_queues_num_per_class
_pq_numa_working_set_affinity TRUE
_pqq_debug_txn_act FALSE
_pqq_enabled TRUE
_pqq_pdb_load_publish_threshold 0
_pre_rewrite_push_pred TRUE
_precompute_gid_values TRUE
_pred_move_around TRUE
_pred_push_cdb_view_enabled TRUE
_predicate_elimination_enabled TRUE
_predicate_validity_execution FALSE
_prefer_local_temp FALSE
_prefered_standby
_preformat_tempfile_bmbs TRUE
_preplugin_backup enabled
_prescomm FALSE
_preshut_action_max_time 5
_prespawn_batch_count 20
_prespawn_bg_init_count 0
_prespawn_enabled FALSE
_prespawn_fg_init_count 0
_prespawn_level
_prespawn_max_count 50
_prespawn_min_count 10
_primary_guard_wait_timeout 120
_print_inmem_heatmap 0
_print_inmem_srmap 0
_print_refresh_schedule false
_print_stat_segment 0
_priv_for_set_current_schema FALSE
_private_memory_address
_proc_grp_enabled 3
_proc_grp_numa_map
_process_allocation_slots 100
_process_heartbeat_range 3
_process_max_pred_increase 20000
_process_percent_rampup_end 320
_process_percent_rampup_start 320
_process_prediction_failover_buffer 1
_process_save_prediction FALSE
_process_so_max_inc 20000
_profile_sensitive_users
_project_view_columns TRUE
_projection_pushdown TRUE
_projection_pushdown_debug 0
_prop_old_enabled FALSE
_propogate_restore_point TRUE
_protect_frame_heaps FALSE
_protect_pga_extents FALSE
_proxy_connect_after_set_container TRUE
_psdclog_enable FALSE
_psdclog_threshold 10
_pseudo_bootstrap FALSE
_pseudo_redo_dump FALSE
_psr_opt enable feature
_ptf_enable_objects FALSE
_ptf_max_rows 1024
_ptn_cache_threshold 1
_ptt_max_num 16
_ptt_rec_max_num 200
_purge_idcs_access_token FALSE
_push_join_predicate TRUE
_push_join_union_view TRUE
_push_join_union_view2 TRUE
_pwise_distinct_enabled TRUE
_px_adaptive_dist_bypass_enabled TRUE
_px_adaptive_dist_bypass_optimization 1
_px_adaptive_dist_method CHOOSE
_px_adaptive_dist_method_threshold 0
_px_adaptive_dist_nij_enabled ON
_px_adaptive_offload_percentage 30
_px_adaptive_offload_threshold 10
_px_autodop_pq_overhead TRUE
_px_back_to_parallel OFF
_px_bind_peek_sharing TRUE
_px_broadcast_fudge_factor 100
_px_buf_subheap_size 4096
_px_buffer_ttl 30
_px_cdb_view_enabled TRUE
_px_cdb_view_join_enabled TRUE
_px_chunk_size 1000000
_px_chunklist_count_ratio 32
_px_compilation_debug 0
_px_compilation_trace 0
_px_concurrent TRUE
_px_cpu_autodop_enabled TRUE
_px_cpu_operator_bandwidth
_px_cpu_process_bandwidth 200
_px_dist_agg_partial_rollup_pushdown ADAPTIVE
_px_dp_array_size 32767
_px_dump_12805_source TRUE
_px_dynamic_granules TRUE
_px_dynamic_granules_adjust 10
_px_dynamic_opt TRUE
_px_dynamic_sample_size 50
_px_execution_services_enabled TRUE
_px_extended_join_skew_handling TRUE
_px_external_table_default_stats TRUE
_px_filter_parallelized TRUE
_px_filter_skew_handling TRUE
_px_freelist_latch_divisor 2
_px_gim_factor 100
_px_granule_alignment 1024
_px_granule_batch_size 26
_px_granule_randomize TRUE
_px_granule_size 1000000
_px_groupby_pushdown FORCE
_px_hold_time 0
_px_hybrid_TSM_HWMB_load TRUE
_px_hybrid_partition_execution_enabled TRUE
_px_hybrid_partition_skew_threshold 10
_px_increase_join_frag_size TRUE
_px_index_sampling_objsize TRUE
_px_io_process_bandwidth 200
_px_io_system_bandwidth 0
_px_join_skew_handling TRUE
_px_join_skew_minfreq 30
_px_join_skew_null_handling TRUE
_px_join_skew_ratio 10
_px_join_skew_sampling_percent 0
_px_join_skew_sampling_time_limit 50
_px_join_skew_use_histogram TRUE
_px_join_skewed_values_count 0
_px_kxib_tracing 0
_px_load_balancing_policy UNIFORM
_px_load_factor 300
_px_load_monitor_threshold 10000
_px_load_publish_interval 200
_px_loc_msg_cost 1000
_px_max_granules_per_slave 100
_px_max_map_val 32
_px_max_message_pool_pct 40
_px_message_compression TRUE
_px_min_granules_per_slave 13
_px_min_ndv_per_slave_perc_func 2
_px_minus_intersect TRUE
_px_net_msg_cost 10000
_px_nlj_bcast_rr_threshold 10
_px_no_granule_sort FALSE
_px_no_stealing FALSE
_px_nss_planb TRUE
_px_numa_stealing_enabled TRUE
_px_numa_support_enabled FALSE
_px_object_sampling 200
_px_object_sampling_enabled TRUE
_px_object_sampling_multiplier 2
_px_onepass_slave_acquisition TRUE
_px_oneslave_per_instance_parse TRUE
_px_overhead_exec_ctrlmesg 4
_px_overhead_init_endpoints 4
_px_overhead_init_slavealloc 1000
_px_overhead_teardown 600
_px_parallel_spawn_min_count 2
_px_parallelize_expression TRUE
_px_parallelize_non_native_datatype TRUE
_px_partial_rollup_pushdown ADAPTIVE
_px_partition_load_dist_threshold 64
_px_partition_load_skew_handling ON
_px_partition_load_skew_threshold 3
_px_partition_scan_enabled TRUE
_px_partition_scan_threshold 64
_px_partition_skew_threshold 80
_px_proactive_slave_alloc_threshold 8
_px_proactive_slave_release 1
_px_proc_constrain TRUE
_px_pwg_enabled TRUE
_px_pwise_wif_enabled TRUE
_px_pwmr_enabled TRUE
_px_replication_enabled TRUE
_px_reuse_server_groups MULTI
_px_round_robin_rowcnt 1000
_px_rownum_pd TRUE
_px_scalable_gby_invdist TRUE
_px_scalable_invdist TRUE
_px_scalable_invdist_mcol TRUE
_px_send_timeout 300
_px_shared_hash_join FALSE
_px_single_server_enabled TRUE
_px_slave_parse_first_with_outline_hints TRUE
_px_split_batches_per_slave 7
_px_split_multi_msg TRUE
_px_split_use_single_list TRUE
_px_tq_memcpy_threshold 100
_px_tq_rowhvs TRUE
_px_trace none
_px_ual_serial_input TRUE
_px_wif_dfo_declumping CHOOSE
_px_wif_extend_distribution_keys TRUE
_px_wif_min_ndv_per_slave 2
_px_window_skew_handling TRUE
_px_window_skew_sample_size 1000
_px_xtgranule_size 10000
_qa_control 0
_qa_lrg_type 0
_qc_oracle_script_counter TRUE
_qesma_access_count 1
_qesma_bo_lru_sz 25
_qesma_mvob_lru_sz 25
_qesma_mvob_pin_lru_sz 5
_qesma_rt_parallel_check 1
_qesmasc_trc 0
_qkgl_crit_pct_threshold 80
_qksfgi_disable_action_mask 0
_qksfgi_disable_oct_mask 0
_qksfgi_dix_val FALSE
_qksfgi_dynamic_partitions
_qksfgi_feature_level 0
_qkslvc_47510_sys 1
_qkslvc_47510_test 0
_qkslvc_diag_flags 0
_qkslvc_extended_bind_sz 1
_quantified_path_pattern_maximum_upper_bound 10
_quarantine_enabled TRUE
_quarantine_max_mem 1
_quarantine_max_objs 10000
_quarantine_per_hour 60
_query_cost_rewrite TRUE
_query_execution_cache_max_size 131072
_query_execution_time_limit 0
_query_mmvrewrite_maxcmaps 20
_query_mmvrewrite_maxdmaps 10
_query_mmvrewrite_maxinlists 5
_query_mmvrewrite_maxintervals 5
_query_mmvrewrite_maxpreds 10
_query_mmvrewrite_maxqryinlistvals 500
_query_mmvrewrite_maxregperm 512
_query_on_physical TRUE
_query_rewrite_1 TRUE
_query_rewrite_2 TRUE
_query_rewrite_drj FALSE
_query_rewrite_expression TRUE
_query_rewrite_fpc TRUE
_query_rewrite_fudge 90
_query_rewrite_jgmigrate TRUE
_query_rewrite_maxdisjunct 257
_query_rewrite_or_error FALSE
_query_rewrite_setopgrw_enable TRUE
_query_rewrite_use_on_query_computation TRUE
_query_rewrite_vop_cleanup TRUE
_queue_buffer_max_dump_len 65536
_rac_dbtype_reset FALSE
_rac_propagate_last_rba TRUE
_radm_enabled TRUE
_rbr_ckpt_tracing 0
_rc_sys_obj_enabled TRUE
_rce_dblink_hostname_transform FALSE
_rce_dns_suffix
_rcfg_disable_verify TRUE
_rcfg_parallel_fixwrite TRUE
_rcfg_parallel_replay TRUE
_rcfg_parallel_verify FALSE
_rdbms_compatibility 19.0
_rdbms_internal_fplib_enabled FALSE
_rdbms_internal_fplib_raise_errors FALSE
_rdbms_min_compatibility 19.0
_rds_congestion_timeout 0
_rds_congestion_type
_re_fast_sql_operator all
_re_independent_expression_cache_size 20
_re_max_sql_op_cache_lmt 7
_re_num_complex_operator 1000
_re_num_rowcache_load 2
_re_result_cache_keysiz 20
_re_result_cache_size 20
_read_delay_threshold 4294967294
_read_mostly_enable_logon FALSE
_read_mostly_instance FALSE
_read_mostly_instance_qa_control 0
_read_mostly_lock_mitigation TRUE
_read_mostly_slave_timeout 20
_read_only_slave_timeout 30
_read_only_violation_dump_to_trace FALSE
_read_only_violation_max_count 500
_read_only_violation_max_count_per_module 100
_read_optimized_table_lookup TRUE
_readable_standby_sync_interval 0
_readable_standby_sync_timeout 10
_reader_farm_isolation_enable FALSE
_reader_farm_isolation_time_threshold 200
_real_time_apply_sim 0
_realfree_heap_max_size 32768
_realfree_heap_mode 0
_realfree_heap_pagesize 65536
_realfree_pq_heap_pagesize 65536
_reclaim_lob_index_scan_limit 0
_reco_network_timeout 10
_reco_populate_mode 1
_reco_sessions_max_percentage 50
_reconfiguration_opt_level 493
_record_module_name TRUE
_recoverable_recovery_batch_percent 50
_recoverable_recovery_max_influx_buffers 100000
_recovery_asserts FALSE
_recovery_percentage 50
_recovery_read_limit 1024
_recovery_skip_cfseq_check FALSE
_recovery_test_kdivs 0
_recovery_verify_writes FALSE
_recursive_imu_transactions FALSE
_recursive_with_branch_iterations 7
_recursive_with_control 0
_recursive_with_max_recursion_level 0
_recursive_with_parallel TRUE
_recursive_with_using_temp_table FALSE
_recycle_con_cache_size 5
_redef_on_statement FALSE
_redo_compatibility_check FALSE
_redo_encryption_cipher_mode XTS
_redo_generation_max_kbytes_sec 0
_redo_indexes_apply DISABLE
_redo_log_check_backup 10
_redo_log_debug_config 0
_redo_log_key_reuse_count 0
_redo_log_record_life 168
_redo_read_from_memory TRUE
_redo_transport_async_mode 0
_redo_transport_compress_all TRUE
_redo_transport_evict_threshold 10
_redo_transport_max_kbytes_sec 0
_redo_transport_min_kbytes_sec 0
_redo_transport_redo_log_management
_redo_transport_resource_management FALSE
_redo_transport_sanity_check 0
_redo_transport_stall_time 360
_redo_transport_stall_time_long 3600
_redo_transport_stream_test TRUE
_redo_transport_stream_writes TRUE
_redo_transport_vio_size_req 1048576
_redo_write_coalesce_all_threshold 0
_redo_write_coalesce_slave_threshold 0
_redo_write_sync_single_io TRUE
_reduce_sby_log_scan TRUE
_ref_cons_sql_enforcement TRUE
_refclone_redirect FALSE
_refclone_source_connect_string
_refresh_clone_adg FALSE
_reg_cache_status FALSE
_region_name
_release_insert_threshold 5
_reliable_block_sends TRUE
_relocate_pdb FALSE
_relocation_commit_batch_size 8
_remessage_dbwrs 0
_remote_asm
_remote_awr_enabled FALSE
_remote_extproc_agent FALSE
_remote_http_port 0
_remote_sv_sequence 3
_remove_aggr_subquery TRUE
_remove_exf_component TRUE
_remove_hostname_from_module FALSE
_rep_base_path
_replace_virtual_columns TRUE
_report_capture_cycle_time 60
_report_capture_dbtime_percent_cutoff 50
_report_capture_recharge_window 10
_report_capture_timeband_length 1
_report_request_ageout_minutes 60
_request_boundaries 3
_request_deferral_enabled FALSE
_reset_increase_lmd_process TRUE
_reset_increase_lms_process TRUE
_resource_exhaustion_warning_thresholds 655361281
_resource_exhaustion_warnings 0
_resource_includes_unlimited_tablespace FALSE
_resource_manager_always_off FALSE
_resource_manager_plan
_restore_block0 on
_restore_create_directory TRUE
_restore_delayed_write FALSE
_restore_maxopenfiles 8
_restore_spfile
_restrict_become_user TRUE
_restrict_db_link_user_entries 10000
_restrict_local_user_dml TRUE
_restrict_operator_access FALSE
_restrict_pdb_gv FALSE
_result_cache_auto_blocklist_epsilon 10000
_result_cache_auto_blocklist_frequency 40000
_result_cache_auto_blocklist_threshold 1000
_result_cache_auto_broadcast_threshold 10000
_result_cache_auto_dml_monitoring_duration 15
_result_cache_auto_dml_monitoring_slots 4
_result_cache_auto_dml_threshold 16
_result_cache_auto_dml_trend_threshold 20
_result_cache_auto_execution_threshold 1
_result_cache_auto_ignore_list 0
_result_cache_auto_size_threshold 100
_result_cache_auto_time_distance 300
_result_cache_auto_time_threshold 1000
_result_cache_black_list
_result_cache_block_size 4096
_result_cache_copy_block_count 1
_result_cache_determ_salt FALSE
_result_cache_deterministic_plsql FALSE
_result_cache_do_recycle_period 300
_result_cache_global TRUE
_result_cache_global_send TRUE
_result_cache_history_size 0
_result_cache_latch_count 4
_result_cache_latch_free_reads ADMIN
_result_cache_load_rate 1
_result_cache_object_black_list 0
_result_cache_per_pdb TRUE
_result_cache_timeout 1
_result_cache_use_hash_table TRUE
_result_cache_white_list
_resumable_critical_alert 0
_retry_file_copy FALSE
_reuse_dropped_pdbid_time 180
_reuse_index_loop 5
_reuse_object_number_delay 0
_reuse_object_numbers 7
_reuse_object_numbers_qa 0
_reuse_object_numbers_reserve_days 60
_rf_blocks_per_entity 5
_right_outer_hash_enable TRUE
_rm_atp_cpu_cnt_scale 1
_rm_base_data_dg_sz 125566976
_rm_cell_cpu_scale 0
_rm_cluster_interconnects
_rm_exadata_disable_dbcpurm FALSE
_rm_exadata_fcsize_unit 1099511627776
_rm_exadata_partition_fc FALSE
_rm_exadata_pdb_cpu_cnt FALSE
_rm_exadata_pdb_cpu_cnt_mult 1
_rm_exadata_pdb_fcsz_scale 0
_rm_exadata_pdb_mult_storage 1
_rm_force_caging
_rm_numa_sched_enable TRUE
_rm_numa_simulation_cpus 0
_rm_numa_simulation_pgs 0
_rm_schedstat_off FALSE
_rm_sgllim 0
_rm_superlong_threshold 300000
_rm_tolerance_lwt 5
_rman_io_priority 3
_rman_roundrobin_placement
_rmt_for_table_redef_enabled TRUE
_rmv_dynamic_priority TRUE
_roi_first_open_wait 120
_rollback_segment_count 0
_rollback_segment_initial 1
_rollback_stopat 0
_rolling_patchlevel
_rolling_vsnnum
_rond_test_mode 0
_root_clone_skip_trigger TRUE
_root_clone_state_from_root TRUE
_router_current_user TRUE
_router_pdb FALSE
_row_cache_cursors 20
_row_cache_dump_cooling_period 10
_row_cache_dump_interval 0
_row_cr TRUE
_row_locking always
_row_shipping_explain FALSE
_row_shipping_threshold 100
_rowlen_for_chaining_threshold 1000
_rowsets_cdb_view_enabled TRUE
_rowsets_enabled TRUE
_rowsets_max_enc_rows 64
_rowsets_max_rows 256
_rowsets_target_maxsize 524288
_rowsets_use_encoding TRUE
_rowsets_use_work_heap_buffer TRUE
_rowsource_execution_statistics FALSE
_rowsource_profiling_statistics TRUE
_rowsource_statistics_sampfreq 128
_rowsrc_trace_level 0
_rq_shm_max_size 1024
_rsrc_cpu_count
_rta_sync_wait_timeout 10
_rtabnd_update_offload TRUE
_rtaddm_trigger_args
_rtaddm_trigger_enabled TRUE
_rtc_infeasible_threshold 25
_rule_max_dnfp_cnt 1024
_runtime_index_key_length_check 1
_runtime_limit_parallel_fptr 60
_saga_afterlra_interval 300
_saga_clear_interval 86400
_saga_timeout_interval 3600
_saga_timeout_operation_type rollback
_sage_block_checking FALSE
_sample_rows_per_block 4
_save_afns_on_subset_pdb_creation FALSE
_sbt_proxy_copy_buffer_size 0
_scalar_type_lob_storage_threshold 4000
_scatter_gcs_resources FALSE
_scatter_gcs_shadows FALSE
_sched_delay_max_samples 4
_sched_delay_measurement_sleep_us 1000
_sched_delay_os_tick_granularity_us 16000
_sched_delay_sample_collection_thresh_ms 200
_sched_delay_sample_interval_ms 1000
_scheduler_cjq0_buffer_size 1024
_scheduler_inmemory_trace_timeout 600
_scheduler_jnnn_buffer_size 32
_scheduler_ora_buffer_size 32
_schema_max_string_size 0
_scn_wait_interface_max_backoff_time_secs 600
_scn_wait_interface_max_timeout_secs 2147483647
_sdiag_crash NONE
_search_space_from_beginning 2147483647
_sec_enable_test_rpcs FALSE
_second_spare_parameter
_second_spare_pdb_parameter
_securefile_log_num_latches 0
_securefile_log_shared_pool_size 0
_securefile_shrink_enable_nowaitlck FALSE
_securefile_shrink_linked_list_limit 100
_securefile_timers FALSE
_securefiles_bgtimeout 0
_securefiles_breakreten_retry 5
_securefiles_bulkclnout TRUE
_securefiles_bulkinsert FALSE
_securefiles_concurrency_estimate 12
_securefiles_dealloc_cfs 0
_securefiles_fg_retry 100
_securefiles_forceflush FALSE
_securefiles_memory_percentofSGA 8
_securefiles_min_retention_override
_securefiles_spcutl FALSE
_seed_root_undo_ratio 30
_selectivity_for_srf_enabled FALSE
_selfjoin_mv_duplicates TRUE
_selftune_checkpoint_write_pct 3
_selftune_checkpointing_lag 300
_sem_per_semid
_send_ast_to_foreground AUTO
_send_close_with_block TRUE
_send_requests_to_pi TRUE
_sensitive_common_as_local FALSE
_sensitive_common_users
_sensitive_fixed_invalidate
_sequence_scale_extend FALSE
_sequence_scale_noextend FALSE
_sequence_scalev2_feature AUTO
_serial_direct_read auto
_serial_log_write_worker_io FALSE
_serial_recovery FALSE
_serializable FALSE
_serialize_lgwr_sync_io FALSE
_service_cleanup_timeout 30
_service_internal_gateway
_sess_sign_num_pools 16
_sess_template_all_overflow FALSE
_sess_template_cache_buckets 128
_sess_template_enabled TRUE
_sess_template_max_cache_size 5
_sess_template_new_lists 16
_sess_template_purge_time_mins 60
_session_allocation_latches 4
_session_aware_replay TRUE
_session_cached_instantiations 60
_session_context_size 10000
_session_idle_bit_latches 0
_session_limit_percent_cap 25
_session_max_pred_increase 20000
_session_modp_list 2
_session_page_extent 2048
_session_percent_rampup_end 504
_session_percent_rampup_start 504
_session_prediction_failover_buffer 1
_session_preserve_logon_container FALSE
_session_save_prediction FALSE
_session_so_max_inc 20000
_session_wait_history 10
_set_con_data_share FALSE
_set_container_service DEFAULT
_seventeenth_spare_parameter
_seventeenth_spare_pdb_parameter
_seventh_spare_parameter
_seventh_spare_pdb_parameter
_seventieth_spare_parameter
_seventieth_spare_pdb_parameter
_seventy-eighth_spare_parameter
_seventy-fifth_spare_parameter
_seventy-first_spare_parameter
_seventy-fourth_spare_parameter
_seventy-ninth_spare_parameter
_seventy-second_spare_parameter
_seventy-seventh_spare_parameter
_seventy-sixth_spare_parameter
_seventy-third_spare_parameter
_sf_default_enabled TRUE
_sga_alloc_slaves_term_timeout_secs 120
_sga_clear_dump FALSE
_sga_early_trace 0
_sga_grow_batch_size 2147483648
_sga_heap_chunk_alignment FALSE
_sga_heap_chunk_alignment_disabled FALSE
_sga_shrink_allow FALSE
_shadow_lost_write_found 118
_shadow_lost_write_tracing 0
_shard_cached_sessions 0
_shard_ddl_policy ASYNC
_shard_enable_serialized_ddl TRUE
_shard_foll_io_timeout_us 1000000
_shard_hb_loss 0
_shard_lcr_cksum TRUE
_shard_max_num_raft_logfile 10
_shard_native_repl_rf5 FALSE
_shard_raft_log_retention_time_mins
_shard_raft_partial_copy_block_count 256
_shard_raft_write_timeout 100000
_shard_reco_txn_test_mode 0
_shard_repl_max_iobuf 256
_shard_repl_queue_wait_us 1000
_shard_size_lcrs_per_transaction 100000
_shard_sql_use_chunk_ids 0
_shardgroup_name
_sharding_lockdown FALSE
_shardspace_name
_share_drcp_proxy_sessions TRUE
_shared_io_pool_buf_size 1048576
_shared_io_pool_debug_trc 0
_shared_io_pool_size 134217728
_shared_io_set_value FALSE
_shared_iop_max_size 134217728
_shared_pool_lru_bufs 200
_shared_pool_max_size 0
_shared_pool_max_sz 0
_shared_pool_minsize_on FALSE
_shared_pool_reserved_min_alloc 4400
_shared_pool_reserved_pct 7
_shared_server_load_balance 0
_shared_server_num_queues 2
_shared_server_sizing_coeff 1000
_shared_servers_performance 0
_shared_spfile_check
_shd_atomic_move 0
_shd_reptype 0
_shmprotect 0
_short_stack_timeout_ms 30000
_show_login_pdb_sessions FALSE
_shrd_que_tm_processes 1
_shrd_que_tm_statistics_duration 0
_shrunk_aggs_disable_threshold 60
_shrunk_aggs_enabled TRUE
_shutdown_abort_detach_wait_msec 3000
_shutdown_abort_timeout_mins 0
_shutdown_completion_timeout_mins 60
_shutdown_immediate_timeout 3600
_shutdown_sync_enable TRUE
_side_channel_batch_size 240
_side_channel_batch_timeout 6
_side_channel_batch_timeout_ms 500
_simple_view_merging TRUE
_simulate_dax_storage DISABLE
_simulate_disk_sectorsize 0
_simulate_io_wait 0
_simulate_logical_sectorsize 0
_simulate_mem_transfer FALSE
_simulated_log_write_usecs 0
_simulator_bucket_mindelta 8192
_simulator_internal_bound 10
_simulator_lru_rebalance_sizthr 5
_simulator_lru_rebalance_thresh 10240
_simulator_lru_scan_count 8
_simulator_pin_inval_maxcnt 16
_simulator_reserved_heap_count 4096
_simulator_reserved_obj_count 1024
_simulator_sampling_factor 2
_simulator_upper_bound_multiple 2
_single_process FALSE
_singleton_service_goodness_disabled TRUE
_siop_flashback_scandepth 20
_siop_init_mem_gradually TRUE
_siop_perc_of_bc_x100 625
_sixteenth_spare_parameter
_sixteenth_spare_pdb_parameter
_sixth_spare_parameter
_sixth_spare_pdb_parameter
_sixtieth_spare_parameter
_sixtieth_spare_pdb_parameter
_sixty-eighth_spare_parameter
_sixty-eighth_spare_pdb_parameter
_sixty-fifth_spare_parameter
_sixty-fifth_spare_pdb_parameter
_sixty-first_spare_parameter
_sixty-first_spare_pdb_parameter
_sixty-fourth_spare_parameter
_sixty-fourth_spare_pdb_parameter
_sixty-ninth_spare_parameter
_sixty-ninth_spare_pdb_parameter
_sixty-second_spare_parameter
_sixty-second_spare_pdb_parameter
_sixty-seventh_spare_parameter
_sixty-seventh_spare_pdb_parameter
_sixty-sixth_spare_parameter
_sixty-sixth_spare_pdb_parameter
_sixty-third_spare_parameter
_sixty-third_spare_pdb_parameter
_size_of_log_table 100
_skgxp_ant_options
_skgxp_ctx_flags1 0
_skgxp_ctx_flags1mask 0
_skgxp_dynamic_protocol 0
_skgxp_gen_ant_off_rpc_timeout_in_sec 30
_skgxp_gen_ant_ping_misscount 3
_skgxp_gen_rpc_no_path_check_in_sec 5
_skgxp_gen_rpc_timeout_in_sec 300
_skgxp_inets
_skgxp_min_rpc_rcv_zcpy_len 0
_skgxp_min_zcpy_len 0
_skgxp_reaping 1000
_skgxp_rgn_ports 0
_skgxp_spare_param1
_skgxp_spare_param2
_skgxp_spare_param3
_skgxp_spare_param4
_skgxp_spare_param5
_skgxp_udp_ach_reaping_time 120
_skgxp_udp_ack_delay 0
_skgxp_udp_enable_dynamic_credit_mgmt 0
_skgxp_udp_hiwat_warn 1000
_skgxp_udp_interface_detection_time_secs 60
_skgxp_udp_keep_alive_ping_timer_secs 300
_skgxp_udp_lmp_mtusize 0
_skgxp_udp_lmp_on FALSE
_skgxp_udp_timed_wait_buffering 1024
_skgxp_udp_timed_wait_seconds 5
_skgxp_udp_use_tcb TRUE
_skgxp_zcpy_flags 0
_skgxpg_last_parameter 27
_skip_acfs_checks FALSE
_skip_adding_plsql_negative_dep FALSE
_skip_app_object_check FALSE
_skip_app_unconverted_check FALSE
_skip_assume_msg TRUE
_skip_cursor_syspriv_rechecks FALSE
_skip_fixed_dependency_load_during_drop FALSE
_skip_multiple_svc_netname_convert_patterns FALSE
_skip_oradism_check FALSE
_skip_pdb_ddl_replay FALSE
_skip_pdb_recovery_if_keystore_not_open FALSE
_skip_pdbid
_skip_pset_col_chk 0
_skip_sequence_cache_close_immediate FALSE
_skip_trstamp_check TRUE
_skip_unconverted_change_vector FALSE
_skip_upg_prechecks_on_pdb_open FALSE
_skip_view_dependent_invalidation FALSE
_skippriv_emailserver_credential FALSE
_slave_mapping_enabled TRUE
_slave_mapping_group_size 0
_slave_mapping_skew_handling TRUE
_slave_mapping_skew_ratio 2
_slow_kill_on_pdb_close_immediate FALSE
_slow_kill_rate_on_pdb_close_immediate 5
_small_table_threshold 6539
_smart_scan_object_size_threshold 100
_smm_advice_enabled TRUE
_smm_advice_log_size 0
_smm_auto_cost_enabled TRUE
_smm_auto_max_io_size 248
_smm_auto_min_io_size 56
_smm_bound 0
_smm_control 0
_smm_freeable_retain 5120
_smm_isort_cap 102400
_smm_low_mem_bound_diag_threshold 0
_smm_max_size 119800
_smm_max_size_static 119800
_smm_min_size 1024
_smm_px_max_size 599040
_smm_px_max_size_static 599040
_smm_retain_size 0
_smm_trace 0
_smon_internal_errlimit 100
_smon_ofd_sleep_interval 300
_smon_sort_management 0
_smon_undo_seg_rescan_limit 10
_smu_debug_mode 0
_smu_error_simulation_site 0
_smu_error_simulation_type 0
_smu_timeouts
_snapshot_recovery_enabled TRUE
_so_percent_lower_bound_final 80
_so_percent_lower_bound_strt 60
_so_percent_upper_bound_final 90
_so_percent_upper_bound_strt 70
_sort_elimination_cost_ratio 0
_sort_multiblock_read_count 2
_sort_spill_threshold 0
_sort_sync_min_spill_threshold 90
_sort_sync_min_spillsize 262144
_space_align_size 1048576
_space_diag_test 0
_space_objd_mismatch 1
_spacebg_sync_segblocks TRUE
_spacereuse_track_memlimit 10
_spadr NO
_spare_ksp_ktucts1 0
_spare_test_parameter 0
_sparse_backing_file AVM
_spawn_diag_opts 0
_spawn_diag_thresh_secs 30
_spec_replace_locks_body TRUE
_spfdc OFF
_spfei
_spfile_comment_validation_mode DISABLE
_spfoc OFF
_spin_count 2000
_split_app_current_state TRUE
_split_file_copy TRUE
_split_partition_target_timeout 600
_spr_max_rules 10000
_spr_push_pred_refspr TRUE
_spr_use_AW_AS TRUE
_sql_alias_scope TRUE
_sql_analysis TRUE
_sql_analyze_enable_auto_txn FALSE
_sql_analyze_parse_model 2
_sql_compatibility 0
_sql_connect_capability_override 0
_sql_connect_capability_table
_sql_diag_repo_origin all
_sql_diag_repo_retain
_sql_error_mitigation_control 0
_sql_error_mitigation_patch_ems_threshold 2
_sql_error_mitigation_patch_validation_interval 30
_sql_error_mitigation_repeat_wait 86400
_sql_error_mitigation_retention 53
_sql_error_mitigation_time_limit 600
_sql_hash_debug 0
_sql_history_buffers 50
_sql_hvshare_debug 1
_sql_hvshare_threshold 0
_sql_model_unfold_forloops RUN_TIME
_sql_ncg_mode OFF
_sql_plan_directive_mgmt_control 67
_sql_plan_management_comp_metric 3
_sql_plan_management_control 0
_sql_show_expreval FALSE
_sqlexec_aggregation_settings 0
_sqlexec_bitmap_options 0
_sqlexec_bitmap_sparse_size 100
_sqlexec_cache_aware_hash_aggr_enabled TRUE
_sqlexec_cache_aware_hash_join_enabled TRUE
_sqlexec_disable_hash_based_distagg_tiv FALSE
_sqlexec_distagg_optimization_settings 0
_sqlexec_encoding_aware_hj_enabled TRUE
_sqlexec_encoding_aware_hj_min_compression_ratio 8
_sqlexec_hash_aggr_small_mem_blocks 2
_sqlexec_hash_based_distagg_enabled TRUE
_sqlexec_hash_based_distagg_ser_civ_enabled TRUE
_sqlexec_hash_based_distagg_ssf_enabled TRUE
_sqlexec_hash_based_set_operation_enabled TRUE
_sqlexec_hash_join_uses_xmem FALSE
_sqlexec_hash_rollup_enabled TRUE
_sqlexec_join_group_aware_hj_enabled TRUE
_sqlexec_join_group_aware_hj_unencoded_rowsets_tol 50
erated
_sqlexec_pwiseops_with_binds_enabled TRUE
_sqlexec_pwiseops_with_sqlfuncs_enabled TRUE
_sqlexec_reorder_wif_enabled TRUE
_sqlexec_sort_uses_xmem TRUE
_sqlexec_use_delayed_unpacking TRUE
_sqlexec_use_kgghash3 TRUE
_sqlexec_use_rwo_aware_expr_analysis TRUE
_sqlexec_window_function_settings 63
_sqlmon_all_rows_numpdb_threshold 10
_sqlmon_binds_xml_format default
_sqlmon_conitr_row_cache_size 50
_sqlmon_entry_cutoff_end_time 0
_sqlmon_entry_cutoff_start_time 3600
_sqlmon_max_active_idle 0
_sqlmon_max_plan 80
_sqlmon_max_planlines 1000
_sqlmon_max_recent_rows_per_pdb 0
_sqlmon_recent_query_max_time 2
_sqlmon_recycle_time 5
_sqlmon_threshold 5
_sqlset_hash_max_size 100000
_sqltune_category_parsed DEFAULT
_srvntfn_job_deq_timeout 60
_srvntfn_jobsubmit_interval 3
_srvntfn_max_concurrent_jobs 20
_srvntfn_max_job_time 180
_srvntfn_q_msgcount 50
_srvntfn_q_msgcount_inc 100
_sscr_dir
_sscr_osdir
_sta_control 0
_stack_guard_level 0
_standard_varchar_storage FALSE
_standby_auto_flashback TRUE
_standby_causal_heartbeat_timeout 2
_standby_flush_mode SLFLUSH
_standby_implicit_rcv_timeout 3
_standby_newkey_keystore_location
_standby_parse_limit_seconds 0
_standby_switchover_timeout 120
_standby_temp_file_management AUTO
_stat_aggs_one_pass_algorithm FALSE
_statement_redirect_host
_statement_redirect_routing_function
_static_backgrounds
_statistics_based_srf_enabled TRUE
_stats_encryption_enabled FALSE
_step_down_limit_in_pct 20
_streams_pool_max_size 0
_strict_dml_data_link FALSE
_strict_redaction_semantics TRUE
_strict_utl_http_smtp FALSE
_subname_for_object_patching
_subquery_pruning_cost_factor 20
_subquery_pruning_enabled TRUE
_subquery_pruning_flags 0
_subquery_pruning_mv_enabled FALSE
_subquery_pruning_reduction 50
_subseg_debug 0
_subseg_quiesce_threshold 10240
_suffix_for_object_patching
_super_shared_conversion_threshold 320
_super_shared_enable FALSE
_super_shared_max_exclusive_conversions 4
_suppress_identifiers_on_dupkey FALSE
_suppress_migration_errors TRUE
_suppress_pg_population FALSE
_suspend_4031_timeout 14400
_suspend_4036_timeout 14400
_suspended_session_timeout 300
_sv_waiters_cap 4294967294
_swat_ver_mv_knob 0
_switch_current_scan_scn TRUE
_switchover_through_cascade TRUE
_switchover_timeout 0
_switchover_to_standby_option OPEN_ALL_IGNORE_SESSIONS
_switchover_to_standby_switch_log FALSE
_swrf_metric_frequent_mode FALSE
_swrf_mmon_dbfus TRUE
_swrf_mmon_flush TRUE
_swrf_mmon_metrics TRUE
_swrf_on_disk_enabled TRUE
_swrf_test_action 0
_swrf_test_dbfus FALSE
_symbol_no_translation FALSE
_sync_app_pdb_first_open FALSE
_sync_error_handler
_sync_primary_wait_time 5
_synchronous_rewrap_rac_ts_keys FALSE
_synonym_repoint_tracing FALSE
_sys_logon_delay 1
_sysaux_test_param 1
_system_api_interception_debug FALSE
_system_index_caching 0
_system_memory_simulate FALSE
_system_parse_limit_seconds 120
_system_partition_with_default FALSE
_system_state_cputime_limit 4294967294
_system_state_runtime_limit 4294967294
_system_trig_enabled TRUE
_tabdict_background_update TRUE
_table_func_pred_pushdown FALSE
_table_lookup_prefetch_size 40
_table_lookup_prefetch_thresh 2
_table_scan_cost_plus_one TRUE
_tablespaces_per_transaction 10
_target_action_name
_target_log_write_size 0
_target_log_write_size_percent_for_poke 100
_target_log_write_size_spinwait 0
_target_log_write_size_timeout 0
_target_module_name
_target_offload FALSE
_target_offload_algorithm random
_target_offload_pdb
_target_rba_max_lag_percentage 81
_tcpinfo_statistics_save_atexit FALSE
_tdb_debug_mode 16
_temp_tran_block_threshold 100
_temp_tran_cache TRUE
_temp_undo_disable_adg FALSE
_temp_undo_disable_refresh_clone FALSE
_temp_undo_optimal_extents 0
_tempfile_monitor_interval 3600
_tempspace_prereuse_exts 1024
_tempspace_tsenq_timeout 600
_tenth_spare_parameter
_tenth_spare_pdb_parameter
_test_flashback_shrink 0
_test_hm_extent_map FALSE
_test_ksusigskip 5
_test_offload_pdb_sga_init FALSE
_test_param_1 25
_test_param_10
_test_param_10_bi 10
_test_param_10_i
_test_param_11_base 3
_test_param_11_dep 0_STARTUP, 1_STARTUP, 2_STARTUP
_test_param_12 0
_test_param_13 FALSE
_test_param_14
_test_param_15 50
_test_param_16 500
_test_param_17 0
_test_param_2
_test_param_3
_test_param_4
_test_param_4_1
_test_param_5 25
_test_param_6 0
_test_param_7 100, 1100, 2100, 3100, 4100
_test_param_8 20
_test_param_9
_test_param_9_1 0
_test_param_9_2 0_startup
_test_param_9_3 1_startup, 2_startup, 3_startup
_test_param_pdb_spare
_test_param_spare
_test_trans_hnsw_vector_scan FALSE
_test_trans_hnsw_vector_scan_user_id 0
_test_xmem_alloc_size 0
_text_batch_num 32
_text_batch_size 8
_text_datastore_access FALSE
_text_estat_purge 30
_text_event_sizing 3
_text_maintenance auto
_tgtt_single_segment FALSE
_third_spare_parameter
_third_spare_pdb_parameter
_thirteenth_spare_parameter
_thirteenth_spare_pdb_parameter
_thirtieth_spare_parameter
_thirtieth_spare_pdb_parameter
_thirty-eighth_spare_parameter
_thirty-eighth_spare_pdb_parameter
_thirty-fifth_spare_parameter
_thirty-fifth_spare_pdb_parameter
_thirty-first_spare_parameter
_thirty-first_spare_pdb_parameter
_thirty-fourth_spare_parameter
_thirty-fourth_spare_pdb_parameter
_thirty-ninth_spare_parameter
_thirty-ninth_spare_pdb_parameter
_thirty-second_spare_parameter
_thirty-second_spare_pdb_parameter
_thirty-seventh_spare_parameter
_thirty-seventh_spare_pdb_parameter
_thirty-sixth_spare_parameter
_thirty-sixth_spare_pdb_parameter
_thirty-third_spare_parameter
_thirty-third_spare_pdb_parameter
_thread_state_change_timeout_pnp 1800
_threaded_execution FALSE
_threshold_alerts_enable 1
_time_based_rcv_ckpt_target 180
_time_based_rcv_hdr_update_interval 180
_time_threshold_to_reboot_mmon_slv 86400
_timemodel_collection TRUE
_timeout_actions_enabled TRUE
_timer_precision 10
_tkh_in_fsc_per_ts 5
_total_large_extent_memory 0
_touch_sga_pages_during_allocation FALSE
_tq_dump_period 0
_trace_buffer_wait_timeouts 0
_trace_buffers ALL:256
_trace_dump_all_procs FALSE
_trace_dump_client_buckets TRUE
_trace_dump_cur_proc_only FALSE
_trace_dump_static_only FALSE
_trace_events
_trace_files_public FALSE
_trace_kqlidp FALSE
_trace_ktds FALSE
_trace_ktfs FALSE
_trace_ktfs_mem FALSE
_trace_logging_from_root FALSE
_trace_logging_uri
_trace_navigation_scope global
_trace_pin_time FALSE
_trace_pool_size
_trace_processes ALL
_trace_suppress
_trace_suppress_disable FALSE
_trace_temp FALSE
_trace_virtual_columns FALSE
_track_app_list
_track_app_sync FALSE
_track_metrics_memory TRUE
_track_space_reuse FALSE
_track_space_reuse_rac FALSE
_transaction_auditing TRUE
_transaction_recovery_servers 0
_transient_logical_clear_hold_mrp_bit FALSE
_tregex_compilation_dump_graph_on_crash FALSE
_tregex_compilation_errors_are_fatal FALSE
_tregex_enable_compilation TRUE
_true_cache_aff_hash_latches 16
_true_cache_block_fetch_abort_timeout 20000
_true_cache_block_fetch_latency_histogram TRUE
_true_cache_block_fetch_latency_limit 5000
_true_cache_block_fetch_latency_trace FALSE
_true_cache_block_fetch_timeout 300
_true_cache_chore_mask 3
_true_cache_config
_true_cache_dest
_true_cache_disable_caps 0
_true_cache_disc_time 86400
_true_cache_heartbeat_interval 60
_true_cache_lad_max_failure 20
_true_cache_lad_nettimeout 30
_true_cache_lad_reopen 15
_true_cache_latch_less_htab FALSE
_true_cache_max_block_fetch_requests 1024
_true_cache_max_payload 1048576
_true_cache_max_unapplied_logs 10
_true_cache_num_batch_requests 4
_true_cache_num_dsndr_process 2
_true_cache_num_fch_process 2
_true_cache_payload_size 65536
_true_cache_pdb_disc_time 3600
_true_cache_preallocate_num_request 1024
_true_cache_restart_timeout_secs 600
_true_cache_send_buffer 2
_true_cache_simulated_caps 1
_true_cache_temp_file_ext 10
_true_cache_temp_file_size 100
_true_cache_wait_pdbopen 0
_truecache_prewarm_enable TRUE
_truecache_prewarm_tracing 0
_truecache_pw_collect_pct 10
_truecache_pw_helpers 0
_truecache_pw_prefetch_count 8
_truncate_optimization_enabled TRUE
_tsenc_obfuscate_key NONE
_tsenc_tracing 0
_tsm_connect_string
_tsm_disable_auto_cleanup 1
_tsq_shared_enabled TRUE
_tstz_localtime_bypass FALSE
_ttc_annotations_level 0
_tts_allow_charset_mismatch FALSE
_tune_kctncv_diff_limit 134217728
_twelfth_spare_parameter
_twelfth_spare_pdb_parameter
_twentieth_spare_parameter
_twentieth_spare_pdb_parameter
_twenty-eighth_spare_parameter
_twenty-eighth_spare_pdb_parameter
_twenty-fifth_spare_parameter
_twenty-fifth_spare_pdb_parameter
_twenty-first_spare_parameter
_twenty-first_spare_pdb_parameter
_twenty-fourth_spare_parameter
_twenty-fourth_spare_pdb_parameter
_twenty-ninth_spare_parameter
_twenty-ninth_spare_pdb_parameter
_twenty-second_spare_parameter
_twenty-second_spare_pdb_parameter
_twenty-seventh_spare_parameter
_twenty-seventh_spare_pdb_parameter
_twenty-sixth_spare_parameter
_twenty-sixth_spare_pdb_parameter
_twenty-third_spare_parameter
_twenty-third_spare_pdb_parameter
_two-hundred-and-eighteenth_spare_parameter FALSE
_two-hundred-and-eighth_spare_parameter FALSE
_two-hundred-and-eleventh_spare_parameter FALSE
_two-hundred-and-fifteenth_spare_parameter FALSE
_two-hundred-and-fifth_spare_parameter FALSE
_two-hundred-and-first_spare_parameter FALSE
_two-hundred-and-fourteenth_spare_parameter FALSE
_two-hundred-and-fourth_spare_parameter FALSE
_two-hundred-and-nineteenth_spare_parameter FALSE
_two-hundred-and-ninth_spare_parameter FALSE
_two-hundred-and-second_spare_parameter FALSE
_two-hundred-and-seventeenth_spare_parameter FALSE
_two-hundred-and-seventh_spare_parameter FALSE
_two-hundred-and-sixteenth_spare_parameter FALSE
_two-hundred-and-sixth_spare_parameter FALSE
_two-hundred-and-tenth_spare_parameter FALSE
_two-hundred-and-third_spare_parameter FALSE
_two-hundred-and-thirteenth_spare_parameter FALSE
_two-hundred-and-twelfth_spare_parameter FALSE
_two-hundred-and-twentieth_spare_parameter FALSE
_two-hundredth_spare_parameter FALSE
_two_pass TRUE
_two_pass_reverse_polish_enabled TRUE
_two_phase_rac_rolling_prepare_timeout 60
_txeventq_init_cache_startup 1
_txeventq_lwm_msg_state_correction TRUE
_txeventq_test_flags 0
_txn_commit_tracking_bg_interval 10000
_txn_commit_tracking_minact_max_wait 10
_txn_commit_tracking_partition_capacity 750000
_txn_control_trace_buf_size 4096
_txn_max_quarantines 3
_txn_spare1 0
_txn_spare2 0
_txn_spare3 0
_txn_trace_bucket_size 16384
_txn_trace_buckets
_txn_tt_commit_ts
_ub4_audit_sessionid FALSE
_uga_cga_large_extent_size 262144
_ultrafast_latch_statistics TRUE
_um_huge_page_min_pct 60
_umf_remote_enabled FALSE
_umf_remote_target_dblink
_umf_test_action 0
_undo_autotune TRUE
_undo_block_compression TRUE
_undo_debug_mode 0
_undo_debug_usage 0
_undo_ofd_enabled TRUE
_undo_ofd_excess 10
_undo_ofd_reserve 30
_undo_tbs_slave_percent 0
_undotbs_regular_tables FALSE
_undotbs_stepdown_pcent 75
_unified_audit_policy_disabled FALSE
_unified_memory_heap_mask 0
_unified_memory_pga_lim_pct 40
_unified_memory_private_pct 20
_unified_memory_shared_pct 80
_unified_pdb_shared_pct 60
_unified_pga_alloc_wait_timeout 10000
_unified_pga_block_size 262144
_unified_pga_gran_free_timeout 3000
_unified_pga_gran_leak_timeout 180000
_unified_pga_list_count 16
_unified_pga_max_pool_size 0
_unified_pga_pool_size 0
_union_rewrite_for_gs YES_GSET_MVS
_uniq_cons_sql_enforcement TRUE
_unnest_subquery TRUE
_unused_block_compression TRUE
_update_datafile_headers_with_space_information FALSE
_upddel_dba_hash_mask_bits 0
_upgrade_capture_noops TRUE
_upgrade_optim TRUE
_upgrade_pdb_on_open TRUE
_usd_preload_blks 4
_usd_recent_read TRUE
_use_adaptive_log_file_sync TRUE
_use_aes128_redo_encryption FALSE
_use_best_fit FALSE
_use_cached_asm_free_space FALSE
_use_column_stats_for_function TRUE
_use_dynamic_shares 1
_use_external_data_cache TRUE
_use_fallocate_for_mga FALSE
_use_fips_mode FALSE
_use_futex_ipc FALSE
_use_hugetlbfs_for_SGA FALSE
_use_hugetlbfs_per_granule FALSE
_use_hybrid_encryption_mode FALSE
_use_ism TRUE
_use_ism_for_pga TRUE
_use_kradc_fetch FALSE
_use_large_pages_for_mga FALSE
_use_nosegment_indexes FALSE
_use_pdb_parselock TRUE
_use_platform_compression_lib TRUE
_use_platform_encryption_lib TRUE
_use_platform_hash_function TRUE
_use_pseudo_policy TRUE
_use_realfree_heap TRUE
_use_saga_qtyp 0
_use_seq_process_cache TRUE
_use_shared_capture FALSE
_use_single_log_writer ADAPTIVE
_use_stored_fgd TRUE
_use_text_large_pages TRUE
_use_vector_post TRUE
_use_zero_copy_io TRUE
_user_defined_sharding 0
_ut_fast_lrg_prediction FALSE
_utl32k_mv_query FALSE
_utlfile_buffer_putline FALSE
_utlfile_dirpath FALSE
_utlmmig_table_stats_gathering TRUE
_uts_disable_client_ip_trace FALSE
_uts_enable_alltrc_stats FALSE
_uts_first_segment_retain TRUE
_uts_first_segment_size 0
_uts_inc_inmem_trace 0
_uts_trace_buffer_size 0
_uts_trace_disk_threshold 1073741824
_uts_trace_files_nopurge FALSE
_uts_trace_segment_size 0
_uts_trace_segments 5
_uxt_cloud_delete_on_drop_table TRUE
_uxt_credential
_uxt_diag_flags 0
_uxt_uri_prefix
_validate_flashback_database FALSE
_validate_metric_groups FALSE
_validate_readmem_redo HEADER_ONLY
_vector_accuracy_report_sample_size 25
_vector_aggregation_max_size 0
_vector_dense_accum_max 100
_vector_distance_metric_default COSINE
_vector_encoding_mode MANUAL
_vector_hnsw_enable_heuristic TRUE
_vector_hnsw_force_seq_ingestion FALSE
_vector_hnsw_load_batch_size 500
_vector_hnsw_mem_overestimate_percent 10
_vector_index_cleanup_build BACKGROUND
_vector_index_cleanup_inline TRUE
_vector_index_compute_statistics TRUE
_vector_index_flush_batch_size 1024
_vector_index_hnsw_buffer_lvector FALSE
_vector_index_hnsw_checkpoint_enable TRUE
_vector_index_hnsw_checkpoint_rac_duplication TRUE
_vector_index_hnsw_checkpoint_refresh REPOPULATE
_vector_index_hnsw_checkpoint_reload_enable TRUE
_vector_index_hnsw_checkpoint_snapshot_threshold 1
_vector_index_hnsw_optimizations 1
_vector_index_hnsw_quiesce_readers_enable TRUE
_vector_index_hnsw_rac_duplication TRUE
_vector_index_hnsw_rac_poll_interval 30
_vector_index_hnsw_rac_retry_count 10
_vector_index_hnsw_refresh_rac_poll_retry_count
_vector_index_hnsw_repopulate_threshold_count 100000
_vector_index_hnsw_snapshot_rac_enable FALSE
_vector_index_hnsw_snapshot_threshold_count 10000
_vector_index_hnsw_test_flags 0
_vector_index_ivf_alert_threshold 10000
_vector_index_ivf_covering_columns TRUE
_vector_index_ivf_disk_format 1
_vector_index_ivf_enable_local_index TRUE
_vector_index_ivf_flashcache_format 1
_vector_index_ivf_im_centroids_in_dmls TRUE
_vector_index_ivf_im_centroids_in_queries TRUE
_vector_index_ivf_local_index_rewrite_level 3
_vector_index_ivf_partition_algorithm 0
_vector_index_ivf_partition_number 0
_vector_index_ivf_partition_size DEFAULT
_vector_index_ivf_pctfree 0
_vector_index_ivf_populate_im_centroids TRUE
_vector_index_ivf_sample_size 0
_vector_index_ivf_test_flags 0
_vector_index_journaling TRUE
_vector_index_minact_max_wait 10
_vector_index_neighbor_graph_refresh REPOPULATE
_vector_index_parallel_degree_limit 0
_vector_index_scan_use_hint TRUE
_vector_index_space_grow_threshold 80
_vector_index_stats_use_enabled FALSE
_vector_index_test_flags 0
_vector_memory_64k_percent 10
_vector_operations_control 0
_vector_query_capture_area_size 100
_vector_query_capture_interval 1
_vector_query_capture_retention_days 7
_vector_serialize_temp_threshold 1000
_vendor_lib_loc
_verify_db_blocks_after_encrypt FALSE
_verify_encrypted_tablespace_keys TRUE
_verify_fg_log_checksum FALSE
_verify_flashback_redo TRUE
_verify_undo_quota FALSE
_very_large_object_threshold 500
_virtual_column_access_control TRUE
_virtual_column_overload_allowed TRUE
_vkrm_schedule_interval 10
_vktm_assert_thresh 30
_wait_breakup_threshold_csecs 600
_wait_breakup_time_csecs 300
_wait_for_busy_session 10
_wait_for_sync TRUE
_wait_outlier_detection_enable OFF
_wait_outlier_dump_flags 0
_wait_outlier_event_names
_wait_outlier_lambda_x1000 1500
_wait_outlier_min_waits 10
_wait_outlier_num_outliers 600
_wait_samples_max_sections 40
_wait_samples_max_time_secs 120
_wait_stats_cpus_per_set 16
_wait_tracker_interval_secs 10
_wait_tracker_num_intervals 0
_wait_yield_hp_mode yield
_wait_yield_mode yield
_wait_yield_sleep_freq 100
_wait_yield_sleep_time_msecs 1
_wait_yield_yield_freq 20
_walk_insert_threshold 0
_watchpoint_on FALSE
_wcr_control 0
_wcr_grv_cache_size 65535
_wcr_seq_cache_size 65535
_wcr_test_action 0
_widetab_comp_enabled TRUE
_windowfunc_optimization_settings 0
_with_subquery OPTIMIZER
_worker_threads 0
_workload_attributes
_write_clones 3
_write_renamed_datafile_name FALSE
_xa_internal_retries 600
_xa_parameters
_xds_max_child_cursors 100
_xengem_devname DEFAULT
_xengem_diagmode OFF
_xengem_enabled TRUE
_xpl_peeked_binds_log_size 8192
_xpl_trace 0
_xs_cleanup_task TRUE
_xs_dispatcher_only FALSE
_xs_logon_grant FALSE
_xs_max_retries_lib_lock 30
_xs_sidp_allow_sha1 TRUE
_xsolapi_auto_materialization_bound 20
_xsolapi_auto_materialization_type PRED_AND_RC
_xsolapi_build_trace FALSE
_xsolapi_debug_output SUPPRESS
_xsolapi_densify_cubes TABULAR
_xsolapi_dimension_group_creation OVERFETCH
_xsolapi_dml_trace
_xsolapi_fetch_type PARTIAL
_xsolapi_fix_vptrs TRUE
_xsolapi_generate_with_clause FALSE
_xsolapi_hierarchy_value_type unique
_xsolapi_load_at_process_start NEVER
_xsolapi_materialization_rowcache_min_rows_for_use 1
_xsolapi_materialize_sources TRUE
_xsolapi_metadata_reader_mode DEFAULT
_xsolapi_odbo_mode FALSE
_xsolapi_opt_aw_position TRUE
_xsolapi_optimize_suppression TRUE
_xsolapi_precompute_subquery TRUE
_xsolapi_remove_columns_for_materialization TRUE
_xsolapi_set_nls TRUE
_xsolapi_share_executors TRUE
_xsolapi_source_trace FALSE
_xsolapi_sql_all_multi_join_non_base_hints
_xsolapi_sql_all_non_base_hints
_xsolapi_sql_auto_dimension_hints FALSE
_xsolapi_sql_auto_measure_hints TRUE
_xsolapi_sql_dimension_hints
_xsolapi_sql_enable_aw_join TRUE
_xsolapi_sql_enable_aw_qdr_merge TRUE
_xsolapi_sql_hints
_xsolapi_sql_measure_hints
_xsolapi_sql_minus_threshold 1000
_xsolapi_sql_optimize TRUE
_xsolapi_sql_prepare_stmt_cache_size 16
_xsolapi_sql_remove_columns TRUE
_xsolapi_sql_result_set_cache_size 32
_xsolapi_sql_symmetric_predicate TRUE
_xsolapi_sql_top_dimension_hints
_xsolapi_sql_top_measure_hints
_xsolapi_sql_use_bind_variables TRUE
_xsolapi_stringify_order_levels FALSE
_xsolapi_support_mtm FALSE
_xsolapi_suppression_aw_mask_threshold 1000
_xsolapi_suppression_chunk_size 4000
_xsolapi_use_models TRUE
_xsolapi_use_olap_dml TRUE
_xsolapi_use_olap_dml_for_rank TRUE
_xt_coverage none
_xt_def_compression_ratio 4
_xt_enable_columnar_fetch TRUE
_xt_http_wscl FALSE
_xt_hybrid_addl_hidden_column FALSE
_xt_legacy_debug_flags 0
_xt_load_data_share FALSE
_xt_pred_pushdown FALSE
_xt_preproc_timeout 100
_xt_sampling_scan_granules ON
_xt_sampling_scan_granules_min_granules 1
_xt_table_hidden_column FALSE
_xt_trace none
_xtbigdata_max_buffersize 10240
_xtbuffer_size 0
_xtts_allow_pre10 FALSE
_xtts_set_platform_info FALSE
_zonemap_auto_candidate_table_min_size 5000
_zonemap_auto_clustering_ratio 50
_zonemap_control 0
_zonemap_refresh_within_load TRUE
_zonemap_staleness_tracking 1
_zonemap_usage_tracking TRUE
_zonemap_use_enabled TRUE
adg_account_info_tracking LOCAL
adg_redirect_dml FALSE
allow_global_dblinks FALSE
allow_group_access_to_sga FALSE
allow_legacy_reco_protocol TRUE
allow_rowid_column_type FALSE
allow_weak_crypto TRUE
approx_for_aggregation FALSE
approx_for_count_distinct FALSE
approx_for_percentile NONE
aq_tm_processes 1
archive_lag_target 0
asm_diskgroups
asm_diskstring
asm_io_processes 20
asm_power_limit 1
asm_preferred_read_failure_groups
asm_unified_audit_destination SYSTEMLOG
asm_unified_audit_level BASIC
audit_file_dest /u01/app/oracle/product/23.0.0.0/dbhome_1/rdbms/au
dit
audit_sys_operations FALSE
audit_syslog_level
audit_trail NONE
auto_start_pdb_services FALSE
autotask_max_active_pdbs 2
awr_pdb_autoflush_enabled TRUE
awr_pdb_max_parallel_slaves 10
awr_snapshot_time_offset 0
background_core_dump partial
background_dump_dest /u01/app/oracle/product/23.0.0.0/dbhome_1/rdbms/lo
g
backup_tape_io_slaves FALSE
bitmap_merge_area_size 1048576
blank_trimming FALSE
blockchain_table_max_no_drop
blockchain_table_retention_threshold 16
buffer_pool_keep
buffer_pool_recycle
cdb_cluster FALSE
cdb_cluster_name
cell_offload_compaction ADAPTIVE
cell_offload_decryption TRUE
cell_offload_parameters
cell_offload_plan_display AUTO
cell_offload_processing TRUE
cell_offloadgroup_name
circuits
client_prefetch_rows 0
client_result_cache_lag 3000
client_result_cache_size 0
client_statistics_level TYPICAL
clonedb FALSE
clonedb_dir
cloud_table_commit_threshold 0
cluster_database FALSE
cluster_interconnects
commit_logging
commit_point_strength 1
commit_wait
commit_write
common_user_prefix C##
compatible 23.6.0
connection_brokers ((TYPE=DEDICATED)(BROKERS=1)), ((TYPE=EMON)(BROKER
S=1))
container_data ALL
containers_parallel_degree 65535
control_file_record_keep_time 7
control_files /oradata/CDB/control01.ctl, /oradata/CDB/control02
.ctl
control_management_pack_access DIAGNOSTIC+TUNING
core_dump_dest /u01/app/oracle/diag/rdbms/cdb/CDB/cdump
cpu_count 4
cpu_min_count 4
create_bitmap_area_size 8388608
create_stored_outlines
cursor_bind_capture_destination memory+disk
cursor_invalidation IMMEDIATE
cursor_sharing EXACT
cursor_space_for_time FALSE
data_guard_max_io_time 240
data_guard_max_longio_time 240
data_guard_sync_latency 0
data_transfer_cache_size 0
db_16k_cache_size 0
db_2k_cache_size 0
db_32k_cache_size 0
db_4k_cache_size 0
db_8k_cache_size 0
db_big_table_cache_percent_target 0
db_block_buffers 0
db_block_checking FALSE
db_block_checksum TYPICAL
db_block_size 8192
db_cache_advice ON
db_cache_size 0
db_create_file_dest
db_create_online_log_dest_1
db_create_online_log_dest_2
db_create_online_log_dest_3
db_create_online_log_dest_4
db_create_online_log_dest_5
db_domain
db_file_multiblock_read_count 128
db_file_name_convert
db_files 200
db_flash_cache_file
db_flash_cache_size 0
db_flashback_log_dest
db_flashback_log_dest_size 0
db_flashback_retention_target 1440
db_index_compression_inheritance NONE
db_keep_cache_size 0
db_lost_write_protect AUTO
db_name CDB
db_performance_profile
db_recovery_auto_rekey ON
db_recovery_file_dest
db_recovery_file_dest_size 0
db_recycle_cache_size 0
db_securefile PREFERRED
db_ultra_safe OFF
db_unique_name CDB
db_unrecoverable_scn_tracking TRUE
db_writer_processes 1
dbnest_enable NONE
dbnest_pdb_fs_conf
dbwr_io_slaves 0
ddl_lock_timeout 0
default_credential
default_sharing metadata
deferred_segment_creation TRUE
dg_broker_config_file1 /u01/app/oracle/product/23.0.0.0/dbhome_1/dbs/dr1C
DB.dat
dg_broker_config_file2 /u01/app/oracle/product/23.0.0.0/dbhome_1/dbs/dr2C
dg_broker_start FALSE
diagnostic_dest /u01/app/oracle
diagnostics_control IGNORE
disable_pdb_feature 0
disk_asynch_io TRUE
dispatchers (PROTOCOL=TCP) (SERVICE=CDBXDB)
distributed_lock_timeout 60
dml_locks 2216
dnfs_batch_size 4096
drcp_connection_limit 0
drcp_dedicated_opt NO
dst_upgrade_insert_conv TRUE
enable_automatic_maintenance_pdb TRUE
enable_ddl_logging FALSE
enable_dnfs_dispatcher FALSE
enable_goldengate_replication FALSE
enable_imc_with_mira FALSE
enable_per_pdb_drcp FALSE
enable_pluggable_database TRUE
enabled_PDBs_on_standby *
encrypt_new_tablespaces CLOUD_ONLY
error_message_details ON
event
external_keystore_credential_location
fal_client
fal_server
fast_start_io_target 0
fast_start_mttr_target 0
fast_start_parallel_rollback LOW
file_mapping FALSE
fileio_network_adapters
filesystemio_options none
fixed_date
forward_listener
gcs_server_processes 0
global_names FALSE
global_txn_processes 1
group_by_position_enabled FALSE
hash_area_size 131072
heartbeat_batch_size 5
heat_map OFF
hi_shared_memory_address 0
hs_autoregister TRUE
http_proxy
hybrid_read_only FALSE
identity_provider_config
identity_provider_type NONE
ifile
ignore_session_set_param_errors
inmemory_adg_enabled TRUE
inmemory_automatic_level OFF
inmemory_clause_default
inmemory_deep_vectorization TRUE
inmemory_expressions_usage ENABLE
inmemory_force DEFAULT
inmemory_graph_algorithm_execution DEFAULT
inmemory_max_populate_servers 0
inmemory_optimized_arithmetic DISABLE
inmemory_optimized_date DISABLE
inmemory_prefer_xmem_memcompress
inmemory_prefer_xmem_priority
inmemory_query ENABLE
inmemory_size 0
inmemory_trickle_repopulate_servers_percent 1
inmemory_virtual_columns MANUAL
inmemory_xmem_size 0
instance_abort_delay_time 0
instance_groups
instance_mode READ-WRITE
instance_name CDB
instance_number 0
instance_type RDBMS
instant_restore FALSE
iorm_limit_policy RM_PLAN
ipddb_enable FALSE
java_jit_enabled TRUE
java_max_sessionspace_size 0
java_pool_size 0
java_restrict none
java_soft_sessionspace_limit 0
job_queue_processes 80
json_behavior
json_expression_check off
kafka_config_file
large_pool_size 0
ldap_directory_access NONE
ldap_directory_sysauth no
license_max_sessions 0
license_max_users 0
license_sessions_warning 0
listener_networks
load_without_compile none
lob_signature_enable FALSE
local_listener LISTENER_CDB
lock_name_space
lock_sga FALSE
lockdown_errors RAISE
lockfree_reservation ON
log_archive_config
log_archive_dest
log_archive_dest_1
log_archive_dest_10
log_archive_dest_11
log_archive_dest_12
log_archive_dest_13
log_archive_dest_14
log_archive_dest_15
log_archive_dest_16
log_archive_dest_17
log_archive_dest_18
log_archive_dest_19
log_archive_dest_2
log_archive_dest_20
log_archive_dest_21
log_archive_dest_22
log_archive_dest_23
log_archive_dest_24
log_archive_dest_25
log_archive_dest_26
log_archive_dest_27
log_archive_dest_28
log_archive_dest_29
log_archive_dest_3
log_archive_dest_30
log_archive_dest_31
log_archive_dest_4
log_archive_dest_5
log_archive_dest_6
log_archive_dest_7
log_archive_dest_8
log_archive_dest_9
log_archive_dest_state_1 enable
log_archive_dest_state_10 enable
log_archive_dest_state_11 enable
log_archive_dest_state_12 enable
log_archive_dest_state_13 enable
log_archive_dest_state_14 enable
log_archive_dest_state_15 enable
log_archive_dest_state_16 enable
log_archive_dest_state_17 enable
log_archive_dest_state_18 enable
log_archive_dest_state_19 enable
log_archive_dest_state_2 enable
log_archive_dest_state_20 enable
log_archive_dest_state_21 enable
log_archive_dest_state_22 enable
log_archive_dest_state_23 enable
log_archive_dest_state_24 enable
log_archive_dest_state_25 enable
log_archive_dest_state_26 enable
log_archive_dest_state_27 enable
log_archive_dest_state_28 enable
log_archive_dest_state_29 enable
log_archive_dest_state_3 enable
log_archive_dest_state_30 enable
log_archive_dest_state_31 enable
log_archive_dest_state_4 enable
log_archive_dest_state_5 enable
log_archive_dest_state_6 enable
log_archive_dest_state_7 enable
log_archive_dest_state_8 enable
log_archive_dest_state_9 enable
log_archive_duplex_dest
log_archive_format %t_%s_%r.dbf
log_archive_max_processes 4
log_archive_min_succeed_dest 1
log_archive_trace 0
log_buffer 8486912
log_checkpoint_interval 0
log_checkpoint_timeout 1800
log_checkpoints_to_alert FALSE
log_file_name_convert
long_module_action TRUE
main_workload_type OLTP
mandatory_user_profile
max_auth_servers 25
max_columns STANDARD
max_datapump_jobs_per_pdb AUTO
max_datapump_parallel_per_job AUTO
max_dispatchers
max_dump_file_size 1G
max_idle_blocker_time 0
max_idle_time 0
max_iops 0
max_mbps 0
max_pdbs 4098
max_saga_duration 86400
max_shared_servers
max_string_size STANDARD
memoptimize_pool_size 0
memoptimize_write_area_size 0
memoptimize_writes HINT
memory_max_size 0
memory_max_target 0
memory_size 0
memory_target 0
min_auth_servers 1
mle_prog_languages all
multishard_query_data_consistency strong
multishard_query_partial_results not allowed
native_blockchain_features
nls_calendar
nls_comp BINARY
nls_currency
nls_date_format
nls_date_language
nls_dual_currency
nls_iso_currency
nls_language AMERICAN
nls_length_semantics BYTE
nls_nchar_conv_excp FALSE
nls_numeric_characters
nls_sort
nls_territory AMERICA
nls_time_format
nls_time_tz_format
nls_timestamp_format
nls_timestamp_tz_format
noncdb_compatible FALSE
object_cache_max_size_percent 10
object_cache_optimal_size 51200000
ofs_threads 4
olap_page_pool_size 0
one_step_plugin_for_pdb_with_tde FALSE
open_cursors 300
open_links 4
open_links_per_instance 4
optimizer_adaptive_plans TRUE
optimizer_adaptive_reporting_only FALSE
optimizer_adaptive_statistics FALSE
optimizer_capture_sql_plan_baselines FALSE
optimizer_capture_sql_quarantine FALSE
optimizer_cross_shard_resiliency FALSE
optimizer_dynamic_sampling 2
optimizer_features_enable 23.1.0
optimizer_ignore_hints FALSE
optimizer_ignore_parallel_hints FALSE
optimizer_index_caching 0
optimizer_index_cost_adj 100
optimizer_inmemory_aware TRUE
optimizer_mode ALL_ROWS
optimizer_real_time_statistics FALSE
optimizer_secure_view_merging
optimizer_session_type NORMAL
optimizer_use_invisible_indexes FALSE
optimizer_use_pending_statistics FALSE
optimizer_use_sql_plan_baselines TRUE
optimizer_use_sql_quarantine TRUE
os_authent_prefix ops$
os_roles FALSE
outbound_dblink_protocols ALL
parallel_adaptive_multi_user FALSE
parallel_degree_limit CPU
parallel_degree_policy MANUAL
parallel_execution_message_size 16384
parallel_force_local FALSE
parallel_instance_group
parallel_max_servers 80
parallel_min_degree 1
parallel_min_percent 0
parallel_min_servers 8
parallel_min_time_threshold AUTO
parallel_servers_target 80
parallel_threads_per_cpu 1
paranoid_concurrency_mode FALSE
pdb_file_name_convert
pdb_lockdown
pdb_os_credential
pdb_template
pdc_file_size 4198400
permit_92_wrap_format FALSE
pga_aggregate_limit 2453667840
pga_aggregate_target 1226833920
pkcs11_library_location
plscope_settings IDENTIFIERS:NONE
plsql_ccflags
plsql_code_type INTERPRETED
plsql_debug FALSE
plsql_implicit_conversion_bool FALSE
plsql_optimize_level 2
plsql_v2_compatibility FALSE
plsql_warnings DISABLE:ALL
pmem_filestore
pre_page_sga TRUE
priority_txns_high_wait_target 2147483647
priority_txns_medium_wait_target 2147483647
priority_txns_mode ROLLBACK
private_temp_table_prefix ORA$PTT_
processes 320
processor_group_name
query_rewrite_enabled TRUE
query_rewrite_integrity enforced
rdbms_server_dn
read_only FALSE
read_only_open_delayed FALSE
recovery_parallelism 0
recyclebin on
redo_transport_user
remote_dependencies_mode TIMESTAMP
remote_listener
remote_login_passwordfile EXCLUSIVE
remote_os_roles FALSE
remote_recovery_file_dest
replication_dependency_tracking TRUE
resource_limit TRUE
resource_manage_goldengate FALSE
resource_manager_cpu_allocation 0
resource_manager_cpu_scope INSTANCE_ONLY
resource_manager_plan
result_cache_auto_blocklist ON
result_cache_execution_threshold 2
result_cache_integrity TRUSTED
result_cache_max_result 5
result_cache_max_size 18874368
result_cache_max_temp_result 5
result_cache_max_temp_size 188743680
result_cache_mode MANUAL
result_cache_remote_expiration 0
resumable_timeout 0
rman_restore_file_storage_metadata FALSE
rollback_segments
run_addm_for_awr_report NONE
saga_hist_retention 43200
scheduler_follow_pdbtz FALSE
sec_max_failed_login_attempts 3
sec_protocol_error_further_action (DROP,3)
sec_protocol_error_trace_action TRACE
sec_return_server_release_banner FALSE
serial_reuse disable
service_names CDB
session_cached_cursors 50
session_exit_on_package_state_error FALSE
session_max_open_files 10
sessions 504
sga_max_size 3690987520
sga_min_size 0
sga_target 3690987520
shadow_core_dump partial
shard_apply_max_memory_size 0
shard_enable_raft_follower_read FALSE
shard_queries_restricted_by_key FALSE
shard_raft_logfile_size 1073741824
shared_memory_address 0
shared_pool_reserved_size 49325015
shared_pool_size 0
shared_server_sessions
shared_servers 1
shrd_dupl_table_refresh_rate 60
skip_unusable_indexes TRUE
smtp_out_server
soda_behavior
sort_area_retained_size 0
sort_area_size 65536
spatial_vector_acceleration TRUE
spfile /u01/app/oracle/product/23.0.0.0/dbhome_1/dbs/spfi
leCDB.ora
sql92_security TRUE
sql_error_mitigation on
sql_history_enabled FALSE
sql_trace FALSE
sql_transpiler OFF
sqltune_category DEFAULT
ssl_wallet
standby_db_preserve_states NONE
standby_file_management MANUAL
standby_pdb_source_file_dblink
standby_pdb_source_file_directory
star_transformation_enabled FALSE
statement_redirect_service
statistics_level TYPICAL
streams_pool_size 0
sysdate_at_dbtimezone FALSE
tablespace_encryption MANUAL_ENABLE
tablespace_encryption_default_algorithm AES256
tablespace_encryption_default_cipher_mode XTS
tape_asynch_io TRUE
target_pdbs 6
tde_configuration
tde_key_cache FALSE
temp_undo_enabled FALSE
thread 0
threaded_execution FALSE
time_at_dbtimezone off
timed_os_statistics 0
timed_statistics TRUE
timezone_version_upgrade_integrity enforced
timezone_version_upgrade_online FALSE
trace_enabled TRUE
tracefile_content_classification DEFAULT
tracefile_identifier
transaction_recovery ENABLED
transactions 554
transactions_per_rollback_segment 5
true_cache FALSE
txn_auto_rollback_high_priority_wait_target 2147483647
txn_auto_rollback_medium_priority_wait_target 2147483647
txn_auto_rollback_mode ROLLBACK
txn_priority HIGH
undo_management AUTO
undo_retention 900
undo_tablespace UNDOTBS1
unified_audit_common_systemlog
unified_audit_systemlog
unified_audit_trail_exclude_columns NONE
uniform_log_timestamp_format TRUE
use_dedicated_broker NONE
use_large_pages TRUE
user_dump_dest /u01/app/oracle/product/23.0.0.0/dbhome_1/rdbms/lo
vector_index_neighbor_graph_reload RESTART
vector_memory_size 0
vector_query_capture ON
wallet_root
workarea_size_policy AUTO
xml_client_side_decoding true
xml_db_events enable
xml_handling_of_invalid_chars raise_error
xml_params
7206 rows selected.